Anonymous and Unlinkable Membership Authentication with Illegal Privilege Transfer Detection ()
1. Introduction
The rapid development of the Internet has resulted in an increase in electronic transactions that allow users to buy goods or services from online platforms provided by Internet companies, including Google, Facebook, eBay, and Twitter. Service providers must confirm whether a user is permitted to access its resource. Access control [1] [2] provides a solution by verifying either a cryptographic certificate or a username and password. However, the information provided by the user during an interaction with the service provider may undermine the user privacy: the user must risk being traced or even impersonated by corrupt service providers.
Group signatures [3] [4] [5] [6] allow group members with privilege to sign a signature under the group secret key. On the basis of an auxiliary cryptographic technique called zero-knowledge proof [7] , the verifier can check the member’s access rights by using the group public key without knowing the member’s identity. The member obtains access to the service if their presented signature is verified to be valid. If necessary, the signature can be opened by a specific group manager to identify the signature’s originator in case of a dispute. Several provably secure authentication schemes [8] [9] [10] [11] have been proposed to create anonymous memberships in which any member of a group can prove to the service provider (i.e., the verifier) that they are qualified to access a service or file; however, these schemes are impractical because they do not provide exclusive verification of revoked memberships. As proven by the fact that some members have been revoked, in contrast to the use of fixed time periods [12] by employing a one-way chain, Ateniese et al. [13] require group members to prove that their membership does not appear on the current certificate revocation list (CRL). However, in their scheme, the verifier must check whether the member’s membership fits any of the revocation information on the CRL in turn by using their “REVOKE” algorithm every time a member requests membership authentication. The cost to the group manager is proportional to the number of revoked group members because issuing new memberships to non-revoked members is required every time a membership is revoked. Clearly, the scheme performs inefficiently and has not been improved to date.
Additionally, state-of-the-art authentication schemes provide few revocation methods without describing how to detect malicious members’ illegal behavior; in other words, such schemes are unaware of malicious members who have been involved in privilege transfer. This is known as impersonation or an illegal privilege transfer attack and is a priority for prevention because it regularly occurs in the aforementioned schemes and is difficult to trace. In addition, the modern authentication schemes are becoming more complicated to ensure security. However, this is not a favorable development because it will obstruct the development of membership authentication schemes, resulting in research becoming impractical and unattractive. In summary, a robust authentication scheme should contain two components: a membership authentication approach that can withstand members who engage in membership transfer and proof of membership that is exclusive to the current CRL.
In this paper, a novel membership authentication scheme is proposed that provides a simple solution for membership authentication and revocation. The proposed scheme may suffer from the disadvantage of illegal privilege transfer; however, this problem can easily be solved by employing the traitor tracing technique [14] [15] [16] [17] [18] . Traitor tracing was first suggested by [14] , which discusses how to identify a traitor in a public key cryptographic scheme and proposes some approaches for revoking access rights for at least one of the traitors involved in illegal privilege transfer. To evade accountability, a traitor may attempt to modify their secret key to avoid being traced. Traitor tracing schemes ensure that no such strategy can succeed, and the schemes guarantee that the traitor’s identity is revealed. Typical CRL approaches are not directly applicable to our proposed scheme because the memberships are anonymous and unlinkable. Instead of compiling a typical CRL, the dynamic accumulator technique [19] [20] [21] is employed in the proposed scheme to enable an eligible member to prove the exclusiveness of their membership on the CRL.
Organization of the Thesis
This paper is organized as follows. Section 2 describes the anonymous authentication scheme and its requirements as well as the dynamic accumulators. An anonymous and unlinkable membership authentication scheme with illegal privilege transfer detection is proposed in Section 3. Security and performance analysis of the proposed scheme is detailed in Section 4. Finally, Section 5 presents the conclusion.
2. Background
2.1. Anonymous Authentication Schemes
Group signatures [12] [13] with membership revocation are typically defined using the following algorithms:
Setup:
A probabilistic algorithm that outputs the group public key and group secret key for the group manager, given a security parameter as the input.
Join:
A protocol between the group manager and a user that results in the user becoming a group member and receiving a group signing key.
Sign:
A probabilistic algorithm that outputs an anonymous membership for a member, with some necessary parameters (including the member’s group signing key) as the input.
Verify:
An algorithm for examining the validity of an alleged membership with respect to a group public key.
Open:
An algorithm, which can only be implemented by the group manager, used to determine the originator’s identity.
Some authentication schemes [10] [11] have been proposed for creating anonymous memberships by extending the idea of group signatures. Three parties are involved in generic authentication schemes, namely the prover (i.e., the member), issuer (i.e., the key generation center [KGC]), and verifier (i.e., the application server [AS]). The issuer is assumed to be a trusted third party responsible for generating unique and anonymous memberships for eligible provers. A prover with membership can prove to the verifier that they have been given an appropriate membership. The verifier can verify the validity of memberships, but knows nothing about the prover’s real identity. The scheme must guarantee that different authentication messages submitted by the same prover cannot be linked.
Additionally, the following security requirements, which have been identified and discussed in the literature, should be inspected.
Unforgeability:
Only an eligible prover can obtain a unique valid membership. An adversary cannot feasibly forge a membership that can obtain verification.
Strong/weak unlinkability:
Strong unlinkability ensures that the pseudonym and real identity of a prover cannot be linked during multiple uses of the membership. Conversely, weak unlinkability allows only a pseudonym but not the prover’s real identity to be linked when the prover uses the membership more than once.
Nontransferability:
Even though the verifier knows nothing about the prover’s real identity during the interactions; however, a sound authentication scheme must guarantee that membership transfer behavior can be detected and abused memberships can be revoked.
Excludability:
Neither a group member nor the group manager can sign on behalf of other group members.
For efficient exclusive verification of the CRL and detection of illegal privilege transfer, the following attractive security properties are necessary:
Dynamic membership:
The membership can easily be updated by any eligible member of the group when inserting (deleting) a new (abusive) member rather than issuing a new membership or requiring the verifier to refer to the CRL.
Traitor detection:
The scheme must be able to determine the real identity of the malicious member.
2.2. Dynamic Reversed Accumulator
Accumulators were first proposed by Benaloh and de Mare [22] for combining a set of members’ specific values into one accumulator. Each corresponding member is assigned a unique witness, which is used to prove the validity of their membership. However, the computational complexity of the Benaloh-de Mare scheme increases linearly, either according to the number of group members or the number of revoked members. In 2002, Camenisch and Lysyanskaya [19] proposed an efficient dynamic accumulator scheme in which members can update their witness dynamically without the authority’s help. Additionally, the computational complexity of inserting and deleting a member as well as updating members’ witnesses is independent of the number of accumulated values. In 2009, Camenisch et al. proposed an additional accumulator scheme [20] that involves using a bilinear cryptography technique. However, the schemes in [19] [20] were later proved insecure by Kuo et al. [21] later. Although other accumulators [23] [24] [25] [26] utilize bilinear cryptography, these schemes are either vulnerable to collusion attacks or inefficient.
In this section, we review the dynamic reversed accumulator scheme of Kuo et al. [21] , which relies on the strong RSA assumption [7] [27] . To the best of our knowledge, their scheme is the most efficient and secure accumulator scheme for state-of-the-art dynamic accumulators and is highly applicable for the granting and revoking of privileges.
Initialization:
Let the modulus
, with p and q safe primes; U be a set of t eligible members, each with an identity
(
); and
be a set of members being revoked. All identities are assumed to be pairwise relatively prime, and the authority maintains the sets U and
, which are initially empty. The authority chooses an element
and a prime z (which can be 2); computes the accumulator as
, where
; and publishes
. Here,
is a public quasi-commutative function [21] . It holds that
・
;
・
Member insertion:
To include a new member
, the authority examines whether
, and if so, adds
to the set U (new set of eligible members as
) and updates the aforementioned archive. The new member is given a witness
and a value
for
. Here, the accumulator ACC is not changed; therefore, the group members do not need to update their witnesses.
Witness verification:
Only an eligible member
can prove the validity of their system access to a verifier, that their unique value
is included in the public accumulator ACC, and that they know the corresponding witness
on the basis of the zero-knowledge proof technique. The verifier can verify the correctness by using the online public information ACC maintained by the authority, and the group member
is granted access rights if the following Equation (1) holds for their claim:
. (1)
Member deletion:
When the membership of group member
is revoked, the authority deletes
from the set U and moves the value
into the set
. The authority computes the new accumulator
, updates the archive, and publishes the revocation information
. Knowledge of p, q is required for computing
. Kuo et al. called their scheme a dynamic reversed accumulator because the value
here is subtracted from the accumulator and the accumulator decreases gradually. Additionally, each member in U must update their witness to reflect the result of the updated accumulator. On the basis of the extended Euclidean algorithm, the eligible members
can compute the integers a and b satisfying
and update their witnesses as
, such that
. Computing the witness update does not require knowledge of (p, q) and can be performed only by the eligible members
. It is infeasible for the revoked member
to update their witness because
. Crucially, the computational costs of both updating the group accumulator and each individual member’s witness are independent of the size of
.
The scheme of Kuo et al. features a substantial computational cost reduction compared with the existing methods because renewing the accumulator and valid members’ witnesses is required only when revoking violating members (not including new members).
3. Proposed Anonymous Authentication Scheme
In this section, a basic scheme of anonymous membership authentication with anonymity, unlinkability, and efficiency is proposed. Furthermore, we discuss its security. Subsequently, an enhanced version of the scheme is accordingly proposed, and this scheme is analyzed in the next section. The member must additionally establish a secure channel with the verifier in contrast to the aforementioned authentication schemes; in other words, a lower layer node-to-node secure channel with randomized encryption is assumed.
3.1. Bilinear Groups and Security Assumptions
The following definition of a bilinear map comes from [28] and is a fundamental building block of our proposed scheme. Let
,
, and
be three groups of the same prime order q, and let P, Q be two generators of
and
, respectively. We say that
are asymmetric bilinear map groups if
and the bilinear map
satisfies the following properties:
・ Bilinearity:
and
,
.
・ Nondegeneracy:
.
・ Computability:
,
is efficiently computable.
The proposed membership authentication scheme can be operated in both symmetric and asymmetric settings. For greater efficiency, the symmetric setting is more appropriate, whereas the asymmetric setting has greater security. Here, we directly use the asymmetric setting to enrich our cryptanalysis content in Section 4 and demonstrate the flexibility of our proposed scheme.
The security of our scheme relies on the hardness of the following problems, which were introduced in [29] .
Definition 1 (Fixed Argument Pairing Inversion Problems). Let
be an asymmetric pairing. The fixed argument pairing inversion 1 (FAPI-1) problem is as follows: Given
and a value
, compute
such that
. The fixed argument pairing inversion 2 (FAPI-2) problem is as follows: Given
and a value
, compute
such that
.
Both problems FAPI-j (for j = 1 or 2) have a unique solution for each given pair
because the pairing is non-degenerate and the groups
,
, and
are cyclic of order q. Finally, a general case of the pairing inversion problem is presented in the following definition.
Definition 2 (Generalized Pairing Inversion (GPI) Problem). The problem is to find two values
and
such that
when a pairing
as above and a value
are given.
3.2. Basic Scheme
In this section, we first introduce a basic anonymous authentication scheme comprising three parties, namely the group member, KGC, and AS. A KGC is a trusted third party responsible for issuing private keys to all valid members, and an AS provides services to any eligible member with proof of valid membership. The basic scheme comprises the following algorithms:
Setup.
As mentioned in Section 3.1,
,
, and
are three bilinear cyclic groups of prime order q;
is a bilinear mapping with underlying groups of same order q; and
and
are two generators. Let
be N prime numbers chosen from the field
, for
. The KGC selects a large even integer k with
and computes the group secret key as
and the corresponding group public key as
. The KGC then publishes the system parameters as
Join.
For each legitimate member
of a group, the KGC randomly selects
elements of
(the components of this subset are denoted as
) and computes
and
. Subsequently,
is given their private key (
,
). Clearly, we have
, but
and
cannot be used directly as proof of membership, otherwise any two application service requests are easily linked and the member’s privacy is threatened. Here, an archive is required for maintaining the tuple (
,
,
) in which the KGC can reveal the real identity of a malicious member who has been recognized as a traitor.
Sign.
When the member
requests service from an AS,
selects two random numbers
and computes
and
.
also computes
,
, and
. Here, the tuple
is the membership of
for obtaining access to application services provided by a specific AS.
Verify.
1)
over a secure channel.
2) AS verifies the membership proof by checking whether
(2)
Because blinding factors
and
are used,
can prove their membership multiple times to the same or to a different AS; by contrast, all the authentication messages
cannot be linked to reveal that they are all generated by the same member
.
Correctness of the scheme.
The correctness of the verification is shown as follows. Given the group public key
and the membership proof
,
gains access to AS’s services if the scheme works correctly and Equation (3) holds:
(3)
cannot compute and send
directly to the AS. Otherwise, the scheme becomes insecure if it is designed in the aforementioned approach. Because the verification equation would become
and any attacker could select two random
and
and then compute
, where
and
are also randomly selected. The attack can thusly pass the verification procedure with the forged membership proof
.
Selection of parameter k.
Let k = 100 and 200; it yields
and
combinations of the value
, respectively, where
is a combination function.
Remarks and Discussion
Impersonation or illegal privilege transfer attack.
A sound anonymous membership authentication scheme should consider how to counteract a forged membership duplication to others from a valid member. That is, a valid member
may attempt to share their private key
with their untrusted friend
. We assume that collusion among the AS, KGC, and
is possible. With knowledge of both
and
(and the related identity of its owner revealed by the
), the AS can obtain both
and
when the original member
logs in to the AS. To check whether a service request is made by
, the AS verifies whether
(4)
Clearly, this “private key revelation” forces
not to share their private key and privilege with others; otherwise, any two of
’s service requests can be linked and their anonymity will be ruined. In this attack, the original member
also risks privilege revocation by the KGC (here, a typical blacklist is required) after an unauthorized privilege transfer is confirmed. The privilege is thus nontransferable.
In the following, we show another privilege transfer approach launched by the member
, but this approach does not undermine
’s anonymity. Let
and
be two blinding factors as before;
uses a third blinding factor
and sends the “transformed” private key
to their friend
, who can be either trusted or untrusted. On the basis of this transformed private key, the unprivileged
can prove their membership to the AS through the same anonymous authentication scheme by computing
,
,
,
, and
. The AS also verifies the membership proof by checking whether Equation (2) holds. In this attack, collusion between the AS and
to threaten the original member
’s privacy is impossible. Nevertheless, the untrusted friend
can disclose the fact of illegal privilege transfer to the KGC by providing
. Recall that the KGC keeps the
and
selected for each member
and can therefore check whether a member
is involved in an unauthorized privilege transfer as follows:
(5)
If Equation (5) holds, the original member
is revoked, and this forces
to not share their transformed private key and privilege with others.
In addition, if
would never betray
, the trusted KGC can be consulted online to recognize this privilege transfer as follows. Assume that the KGC can compute
in advance for all registered members. If the AS provides a suspicious
to the KGC for investigating potential privilege transfers, the KGC attempts to use all registered members’ information
, for
, and computes both
(6)
and
(7)
The KGC then tests whether any
equals
to verify whether the received authentication message was generated by privileged member
. Clearly, the authentication message generated from a transformed private key with
will fail to pass the verification, and we can conclude that someone has transferred their membership to someone else. The KGC knows nothing regarding the malicious member’s real identity, which is known as “weak unlinkability.” In a medium-sized setting with a moderately large number of members, the described online investigation might be possible if not performed frequently. However, this method cannot completely prevent illegal privilege transfer attack.
Replay attack.
This basic scheme cannot withstand the replay attack.
3.3. Enhanced Version of the Proposed Scheme
Consider the potential illegal privilege transfer attack and unpreventable replay attack mentioned in Section 3.2.1. An enhanced scheme is proposed in this section. The scheme features anonymity and unlinkabilty and guarantees security against the aforementioned attacks. Because some algorithms are identical to those defined in Section 3.2, including Setup and Join, this section describes only the differences. The algorithms of the enhanced scheme are detailed as follows:
Sign.
Let
be a timestamp and
be a collision-free one-way hash function. When the member
requests service from an AS,
selects two random numbers
and computes
,
,
, and
, where
. Here, the tuple
is the membership of
for obtaining access to the application services provided by a specific AS.
Verify.
1)
over a secure channel.
2) Let
be the current timestamp of the AS and
be an appropriate tolerance in the time delay. Given the group public key Y, the AS can verify the membership proof presented by a member
, and
is granted access rights if the following Equations ((8) and (9)) hold; otherwise, the AS rejects the request of
:
(8)
(9)
The scheme enables the AS to validate
’s claim while learning nothing about their real identity, even if it colludes with the KGC. For the purpose of anonymous authentication and strong unlinkability, two blinding factors and a timestamp are employed so that a member can prove their membership multiple times to the same or to a different AS. All the authentication messages
cannot be linked to reveal that they are all generated by the same member. Cryptanalysis of this enhanced scheme is presented in Section 4.
3.3.1. Detection of Illegal Privilege Transfer
The member
is assumed to be able to send the transformed private key
to their friend
, who can be either a trusted or an untrusted individual, where
is a random number and
. After obtaining the transformed private key,
computes
,
,
, and
, where
. The unprivileged party
can prove their membership to the AS through the aforementioned improved anonymous authentication scheme and obtain access to the resource on the AS if Equations ((8) and (9)) hold. Here, collusion between the AS and
that threatens the original member
’s privacy is impossible. As mentioned in Section 3.2.1, two approaches exist for detecting whether a member
is involved in an unauthorized privilege transfer. The first is to let
disclose
’s illegal privilege transfer by providing
to the KGC; however, this approach is passive and impractical for preventing private keys from being transformed. The second is that the trusted KGC can be consulted online to recognize the privilege transfer as follows. Recall that the KGC retains
and
when generating private keys for each member
. If the AS provides a suspicious
to the KGC for investigating potential privilege transfer, the KGC attempts to use all values of
, for
, of registered members and computes both
(10)
and
(11)
The KGC checks whether any
equals 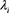 to determine whether the received authentication message was generated by privileged member
to determine whether the received authentication message was generated by privileged member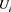 . Clearly, the aforementioned authentication message generated from a transformed private key with
. Clearly, the aforementioned authentication message generated from a transformed private key with 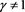 fails to pass the verification. We can conclude that the received authentication message is an impersonated membership and that someone has shared their private key and privilege with another, but the KGC does not know who is the traitor at this stage because the proposed authentication scheme provides “anonymity”. Consequently, the KGC uses the information (
fails to pass the verification. We can conclude that the received authentication message is an impersonated membership and that someone has shared their private key and privilege with another, but the KGC does not know who is the traitor at this stage because the proposed authentication scheme provides “anonymity”. Consequently, the KGC uses the information ( ,
,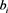 ) to compute
) to compute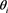 , for
, for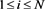 , as follows:
, as follows:
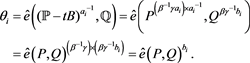 (12)
(12)
The KGC subsequently examines all values of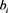 , for
, for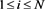 , to determine whether any
, to determine whether any 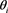 equals
equals 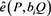 and thus discover the real identity and revoke the membership of the traitor
and thus discover the real identity and revoke the membership of the traitor 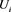 who is involved in an unauthorized privilege transfer. This online detection approach can be performed regularly in case the AS has noticed that an unauthorized privilege transfer has occurred in the system.
who is involved in an unauthorized privilege transfer. This online detection approach can be performed regularly in case the AS has noticed that an unauthorized privilege transfer has occurred in the system.
3.3.2. Exclusiveness of the Membership
By employing the dynamic reversed accumulator of Kuo et al., which is described in Section 2.2, a member Alice who has been included in the set U receives a membership (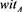 ,
,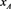 ) and can therefore prove to the AS that her identity
) and can therefore prove to the AS that her identity 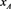 is not on the CRL; this is called “exclusiveness of the membership”. Of course, a dynamic public archive is required for storing information regarding joined and revoked members as well as the current accumulator ACC. Each member is assumed to read the archive regularly and update their witness when ACC has been changed. This accumulator performs more efficiently than existing methods because renewing the accumulator and valid members’ witnesses is required only when revoking violating members but not when adding new members. The AS thus does not have to verify whether a member is on the CRL in contrast to those presented in [6] [13] . Additionally, forging of the witness by an adversary is infeasible according to the strong RSA assumption [7] [27] .
is not on the CRL; this is called “exclusiveness of the membership”. Of course, a dynamic public archive is required for storing information regarding joined and revoked members as well as the current accumulator ACC. Each member is assumed to read the archive regularly and update their witness when ACC has been changed. This accumulator performs more efficiently than existing methods because renewing the accumulator and valid members’ witnesses is required only when revoking violating members but not when adding new members. The AS thus does not have to verify whether a member is on the CRL in contrast to those presented in [6] [13] . Additionally, forging of the witness by an adversary is infeasible according to the strong RSA assumption [7] [27] .
In addition, the accumulator of Kuo et al. provides efficient multiwitness verification in which a group member may access multiple services or files simultaneously and the AS can verify the member’s qualifications simultaneously. This property is outstanding and has not been demonstrated in previous studies. Suppose that m services exist, namely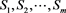 , provided by various AS. The KGC must generate m accumulators in advance as
, provided by various AS. The KGC must generate m accumulators in advance as 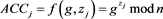 for service
for service![]() , where
, where![]() . If Alice is permitted to access the services
. If Alice is permitted to access the services ![]() and
and ![]() both provided by the same AS, she may be assigned the witnesses
both provided by the same AS, she may be assigned the witnesses ![]() (
(![]() ). Thus, Alice can convince the AS of the validity of her membership and gains access to services
). Thus, Alice can convince the AS of the validity of her membership and gains access to services ![]() and
and ![]() by providing the corresponding witnesses
by providing the corresponding witnesses ![]() and
and ![]() on the basis of the zero- knowledge proof technique. The AS must obtain the current accumulators
on the basis of the zero- knowledge proof technique. The AS must obtain the current accumulators ![]() and
and ![]() of services
of services ![]() and
and ![]() and verify whether Alice is qualified to access these services through Equation (13):
and verify whether Alice is qualified to access these services through Equation (13):
![]() (13)
(13)
4. Performance and Security Analysis
This section verifies our claim of an efficient, anonymous, and unlinkable membership authentication scheme. We first detail the security properties provided by our scheme. Note that some properties have been detailed in the aforementioned sections.
Resistance of replay attack
An adversary may attempt to resend a stolen membership tuple to pass verification. Recall that AS accepts a membership proof if Equation (8) holds (one of the necessary conditions); thus, resending a stolen membership tuple would increase the time of (![]() ) and therefore the adversary cannot pass the verification.
) and therefore the adversary cannot pass the verification.
Membership nontransferability
Recall that a valid member ![]() can send the transformed private key to their friend
can send the transformed private key to their friend ![]() by adding a random number
by adding a random number ![]() as
as![]() . The unprivileged party
. The unprivileged party ![]() can prove their validity to the AS by computing
can prove their validity to the AS by computing ![]() with the transformed private key. Through detection of illegal privilege transfer, as described in Section 3.3.1, the membership of any traitor who is involved in unauthorized privilege transfer will be revoked by the KGC. This can force the member
with the transformed private key. Through detection of illegal privilege transfer, as described in Section 3.3.1, the membership of any traitor who is involved in unauthorized privilege transfer will be revoked by the KGC. This can force the member ![]() not to share their private key and privilege with others; otherwise, any two of
not to share their private key and privilege with others; otherwise, any two of![]() ’s service requests can be linked and their anonymity will be ruined.
’s service requests can be linked and their anonymity will be ruined.
The following two lemmas from [29] [30] must be given before demonstrating theorems related to our scheme.
Lemma 1. The GPI is not harder than either FAPI-1 or FAPI-2.
Proof.
(FAPI-1 ⟹ GPI:)
Given a GPI instance Y and an element ![]() as input, call the FAPI-1 oracle and output
as input, call the FAPI-1 oracle and output![]() ; the FAPI-1 solver can solve the GPI problem.
; the FAPI-1 solver can solve the GPI problem.
(GPI ⇏ FAPI-1:)
By contrast, given an FAPI-1 instance as input, the GPI solver cannot solve the FAPI-1 problem.
We can similarly prove that GPI ≤ FAPI-2.
Lemma 2. If FAPI-j is solvable, then the computational Diffie-Hellman (CDH) problem in![]() ,
, ![]() , and
, and ![]() is solvable.
is solvable.
Proof.
Let ![]() be the oracle to solve FAPI-j, for j = 1 or 2. Recall that
be the oracle to solve FAPI-j, for j = 1 or 2. Recall that ![]() returns
returns ![]() and
and ![]() returns
returns ![]() such that
such that![]() . Suppose that (
. Suppose that (![]() ,
, ![]() ,
,![]() ) is a CDH input in
) is a CDH input in![]() . Choose a
. Choose a ![]() and compute
and compute![]() . Call FAPI-1 solver
. Call FAPI-1 solver ![]() to obtain
to obtain![]() . Finally, compute
. Finally, compute ![]() and call FAPI-2 solver
and call FAPI-2 solver ![]() to obtain
to obtain![]() .
.
The other two cases (solving CDH in ![]() and
and![]() ) are similar.
) are similar.
Theorem 3 (Private key forgery freeness). Let ![]() be a polynomial-time adversary who is not in the group and who is assigned a parameter
be a polynomial-time adversary who is not in the group and who is assigned a parameter ![]() . The proposed scheme can withstand
. The proposed scheme can withstand ![]() from private key forgery through the following manners of attack:
from private key forgery through the following manners of attack:
1) computing ![]() and
and ![]() with
with ![]()
2) choosing an element ![]() and finding
and finding ![]() with
with ![]()
3) choosing an element ![]() and finding
and finding ![]() with
with ![]()
4) extracting the group secret key X from the group public key Y.
Proof.
We discuss these cases of possible forgery in the following.
Case 1:
An adversary ![]() may attempt to find two elements
may attempt to find two elements ![]() and
and ![]() such that
such that![]() , for an unknown X. For
, for an unknown X. For ![]() to forge an eligible private key pair
to forge an eligible private key pair ![]() with a nonnegligible probability
with a nonnegligible probability ![]() as follows is computationally infeasible:
as follows is computationally infeasible:
![]() (14)
(14)
The success of ![]() can be used to solve the GPI problem defined in Section 3.1.
can be used to solve the GPI problem defined in Section 3.1.
Cases 2 & 3:
From Lemmas 1 and 2, we know that 1) the GPI problem is not harder than either FAPI-1 or FAPI-2 and 2) if FAPI-j (where j = 1 or 2) is solvable, then the CDH problem is solvable. That is, an ![]() who can succeed in cases 2 and 3 can be used to solve the problems of GPI and CDH.
who can succeed in cases 2 and 3 can be used to solve the problems of GPI and CDH.
Case 4:
Similarly, if ![]() can succeed in extracting the group secret key X from the group public key
can succeed in extracting the group secret key X from the group public key ![]() without knowledge of k prime numbers, then it can be used directly to solve the discrete logarithm (DL) problem in
without knowledge of k prime numbers, then it can be used directly to solve the discrete logarithm (DL) problem in![]() . Moreover, such an adversary
. Moreover, such an adversary ![]() can create any private key pair by computing
can create any private key pair by computing ![]() and
and![]() . That is, pairing inversion can be computed efficiently by
. That is, pairing inversion can be computed efficiently by ![]() in known pairing groups. This case has been discussed in [31] [32] and is known as the MOV reduction in that the DL in
in known pairing groups. This case has been discussed in [31] [32] and is known as the MOV reduction in that the DL in ![]() and
and ![]() can be solved in polynomial time if a DL oracle exists for
can be solved in polynomial time if a DL oracle exists for![]() . Breaking the DL in
. Breaking the DL in![]() ,
, ![]() , or
, or ![]() is clearly harder than FAPI-j because intuitively breaking FAPI-j (where j = 1 or 2) involves only computing a group element in
is clearly harder than FAPI-j because intuitively breaking FAPI-j (where j = 1 or 2) involves only computing a group element in ![]() or
or ![]() and does not directly provide a method for recovering an exponent in
and does not directly provide a method for recovering an exponent in![]() ,
, ![]() , or
, or![]() . □
. □
From this reasoning, we know GPI ≤ FAPI-j
CDH ≤![]() . A straightforward approach for
. A straightforward approach for ![]() is to forge an eligible private key by using the method of Case 1. However, no efficient algorithm is available that can break the GPI with a nonnegligible probability
is to forge an eligible private key by using the method of Case 1. However, no efficient algorithm is available that can break the GPI with a nonnegligible probability![]() . In summary, we conclude that our proposed scheme is secure against any possible private key forgery. Additionally, forged memberships generated using the aforementioned approaches will be recognized by the proposed scheme for detecting illegal privilege transfer described in Section 3.3.1, if the AS reports suspicious membership to the KGC for investigation.
. In summary, we conclude that our proposed scheme is secure against any possible private key forgery. Additionally, forged memberships generated using the aforementioned approaches will be recognized by the proposed scheme for detecting illegal privilege transfer described in Section 3.3.1, if the AS reports suspicious membership to the KGC for investigation.
Theorem 4 (Resistance against membership impersonation). Let ![]() be a polynomial-time adversary with a valid private key. Given the system parameter
be a polynomial-time adversary with a valid private key. Given the system parameter![]() , the proposed scheme can withstand an adversary
, the proposed scheme can withstand an adversary ![]() engaging in a private key impersonation aimed at the other eligible members
engaging in a private key impersonation aimed at the other eligible members ![]() or the new member
or the new member![]() .
.
Proof.
If the adversary ![]() has ever joined the group, they may attempt to add a random number
has ever joined the group, they may attempt to add a random number ![]() to the private key
to the private key ![]() they received previously to find the private key
they received previously to find the private key ![]() of an eligible member
of an eligible member ![]() such that
such that ![]() and
and![]() . Clearly, this attack cannot be recognized by the proposed illegal privilege transfer detection mechanism. This problem can be reduced to the selection of parameter k described in Section 3.2. We assume that k = 200, which yields
. Clearly, this attack cannot be recognized by the proposed illegal privilege transfer detection mechanism. This problem can be reduced to the selection of parameter k described in Section 3.2. We assume that k = 200, which yields ![]() combinations of the value
combinations of the value![]() . The probability that two assignments of the value
. The probability that two assignments of the value ![]() for different members are identical is approximately 1/1059, which is also the probability that the adversary
for different members are identical is approximately 1/1059, which is also the probability that the adversary ![]() can succeed in computing the valid private keys of eligible members
can succeed in computing the valid private keys of eligible members ![]() and is negligible.
and is negligible.
Finally, Table 1 illustrates the substantial improvement of our proposed scheme compared with other schemes for the security concerns that we mentioned and defined in Section 2.1. Our proposed scheme features strong unlinkability, nontransferability, dynamic membership, and traitor detection. Table 2 shows the main enhancement in efficiency achieved by our scheme. The computational cost of our scheme comprises that of the presented anonymous authentication scheme and the dynamic reversed accumulator of Kuo et al. [21] .
5. Conclusion
We propose a novel membership authentication scheme through which anonymity, strong unlinkability, and illegal privilege transfer detection are
![]()
Table 1. Comparison of security requirements.
![]()
Table 2. Comparison of computational costs.
*![]() : number of eligible/revoked members,
: number of eligible/revoked members,![]() : time period, H: hash operation,
: time period, H: hash operation,![]() : exponentiation in
: exponentiation in![]() ,
,![]() : inverse modulo
: inverse modulo![]() ,
,![]() : multiplication modulo
: multiplication modulo![]() ,
,![]() : multiplication in
: multiplication in![]() ,
,![]() : addition/subtraction over exponent, P: pairing operation,
: addition/subtraction over exponent, P: pairing operation,![]() : squaring operation modulo n, Eu: extended Euclidean, and PK: proof of knowledge.
: squaring operation modulo n, Eu: extended Euclidean, and PK: proof of knowledge.
provided. As aforementioned discussion, our proposed scheme can perform more efficiently if the symmetric setting of bilinear map groups is applied. By employing an efficient dynamic reversed accumulator, system members can prove their membership exclusiveness of the CRL to the verifier. Additionally, the practicality and attractiveness of our proposed scheme is supported.