Evaluation of Different Electronic Product Code Discovery Service Models ()
1. Introduction
Supply chain is a process of transforming natural resources or raw materials into finished goods, by passing through suppliers, manufacturers, wholesalers, retailers, customers and other supply chain partners [1]. When various supply chain partners work together to deliver the right amount of goods to the right customers at right time and right place, good coordination and information sharing are critical.
Lack of information sharing among supply chain partners can lead to a lot of negative consequences. For instance, when downstream retailers are not willing to share their end customer information (e.g. for security and privacy reasons), upstream suppliers and manufacturers have no idea about the customers. The manufacturers predict the customer demand from wholesalers’ orders, while wholesalers predict the customer demand from the retailers’ orders. This lack of information transparency can lead to “bullwhip effect” where each upstream supply chain participant observes greater demand variation and greater need for safety stocks, consequently bearing greater costs [2]. The whole supply chain can suffer as it becomes less responsive to demand fluctuations.
Therefore, in today’s market where competition is very intense, it becomes increasingly important to have a structured way of fast and secure information sharing among supply chain partners. Standardized systems and communication methods, which can be used uniformly across different organizations around the globe, are required to be developed.
As such, EPCglobal organization [3], which is responsible for standardization of Electronic Product Code (EPC) technology [4], created EPCglobal Network [5] for sharing RFID information. EPCglobal Network is implemented, using standards from EPCglobal Architecture Framework [6]. It has four components, namely Object Naming Service (ONS), EPC Discovery Services (EPCDS), EPC Information Services (EPCIS) and EPC Security Services [5]. In this paper, we focus mainly on EPCDS models, since standardization of EPCDS design is still an open research question [6].
Our paper is structured as follows. Section 2 provides background information on EPCDS and EPCIS. Section 3 briefly describes existing EPCDS models which include Directory Service Model, Query Relay model and Aggregating Discover Service model. In Section 4, we describe SecDS model which is an extension of Directory Service Model. Section 5 gives comparison of the different models and Section 6 summarizes the analysis. Then, we identify possible improvements for SecDS model in Section 6 and finally we conclude the paper in Section 7 with the role of EPCDS in future Internet of Things (IOT) [7].
2. Background
2.1. EPCDS
Electronic Product Code Discovery Service (EPCDS) is a service that allows users to find supply chain partners who possess a given product. A user just need to key in a particular EPC number, such as RFID number of the product, to search for EPC Information Services (EPCIS) provided by the related supply chain partners within the network.
EPCDS can be compared to telephone directory or search engines of the internet. To request information about a particular EPC, a supply chain participant needs to have knowledge of who are its supply chain partners and their network addresses or URLs that should be queried. This is like the need to know the phone numbers before contacting each other. Then, EPCDS acts like a telephone directory or yellow page where the contacts or addresses of EPC information providers or repositories are aggregately stored and returned to the appropriate queries accordingly, as shown in Figure 1 [8].
Basically, EPCDS supports two operations, publishing operation and querying operation. Publishing operation is for EPCIS to publish their information on EPCIS whereas querying operation is for supply chain users, who want to find published EPCIS addresses.
2.2. EPCIS
In this context, EPC Information Service (EPCIS) can simply be viewed as a database or repository owned by a supply chain participant. It stores event information of supply chain products, where each product is uniquely identified by an EPC number. EPC event information includes product information, product location, date and time of product arrival and departure, involved business processes, and other important business information [6].
To share its critical business information with its trusted supply chain partners, EPCIS provides a querying

Figure 1. EPCDS as a directory of EPCIS.
interface for its repository. However, EPCIS may maintain access control mechanisms to ensure that only authorized users can access its sensitive information. With EPCIS querying service, any authorized users, who know the address of EPCIS service, can get access to its EPC repositories or databases easily.
2.3. Definition of Terms
In our paper, the terms “users” or “clients” is used for supply chain participants who want to get EPC event information from EPCIS. EPCIS company (owner), database and its services are collectively mentioned as “EPCIS”, “resource”, “EPCIS resource” “EPCIS repository” or “EPCIS company”.
3. Existing Discovery Service Models
BRIDGE (Building Radio frequency identification for the Global Environment) project has modeled and analyzed eight possible high level designs of EPCDS in 2007. After considering each model’s feasibility, BRIDGE selected the two models of EPCDS, called Directory Service Model and Query Relay Model [8]. Although there are a lot of variations of these two models, our paper only use basic models suggested in BRIDGE document for simplicity purpose. The third EPCDS design is Aggregating Discovery Service (ADS) Model, proposed by Hasso Plattner Institute for IT Systems Engineering in 2010 [9].
3.1. Directory Service Model
In Directory Service Model, EPCDS stores a directory of EPC numbers and corresponding EPCIS addresses. Figure 2 illustrates the steps of this Directory Service Model.
Step 1: An owner of an EPCIS first registers at EPCDS with the details on which EPC numbers they are handling, together with its service address or URL. EPCDS stores the pairs of EPC numbers and EPCIS addresses in its lookup table.
Step 2: User sends query to EPCDS with a specific EPC number or a range of EPC numbers as parameters.
Step 3: EPCDS uses lookup table to look up queried EPC numbers, finds corresponding EPCIS addresses and returns them to the user.
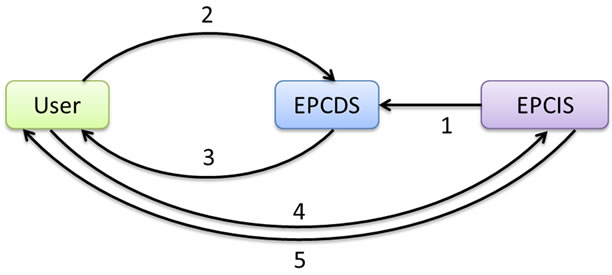
Figure 2. Steps in Directory Service Model.
Step 4: With the returned addresses, the user queries directly to EPCIS repositories to get the desired required EPC event information.
Step 5: EPCIS repositories return the required EPC event information to the user.
One of the main problems of Directory Service Model is that EPCDS returns all the related EPCIS addresses to every user who queries. Access control mechanisms are not specified in detail.
Based on the query result, every user knows exactly which EPCIS repositories are handling which EPC numbers. Availability of EPCIS addresses indicates ownership of product information in that EPCIS companies. Therefore, many companies, who consider their possession of items as confidential or sensitive information, do not want to expose their EPCIS addresses and are reluctant to publish them on EPCDS.
3.2. Query Relay Model
In the query relay model, EPCDS does not return the service addresses of EPCIS repositories immediately upon request. Instead, it redirects the query to corresponding EPCIS repositories which have their own access control mechanisms. As shown in Figure 3, query relay model has the following steps.
Step 1: An owner of an EPCIS first registers at EPCDS with the details on which EPC numbers they are handling, together with its service address or URL. Then, EPCDS stores the pairs of EPC numbers and EPCIS addresses in the lookup table.
Step 2: User sends query to EPCDS with a specific EPC number or a range of EPC numbers as well as user’s credentials as parameters.
Step 3: EPCDS uses lookup table to look up queried EPC numbers, finds corresponding EPCIS addresses and relays user’s query and credentials to those EPCIS resources.
Step 4: Each EPCIS resource checks user’s credentials against its own access control database and returns the query result to the authenticated user directly.
Actually, in query relay model, user query can be of two types. The first one is a full query, directly requesting EPCIS to return the full EPC event information. The second query type is a resource query, where EPCIS returns only the service address that user should query to
get required EPC event information.
3.3. Aggregating Discovery Service (ADS)
Aggregating Discovery Service (ADS) model is based on the query relay model. In this model, instead of returning EPC event information directly to user, each EPCIS returns the result back to EPCDS. Only after getting replies from different EPCIS repositories, EPCDS aggregates their information and sends them back to the user. Figure 4 shows the steps of aggregating discovery service model.
Step 1: An owner of an EPCIS first registers at EPCDS with the details on which EPC numbers they are handling, together with its service address or URL. Then, EPCDS stores the pairs of EPC numbers and EPCIS addresses in the lookup table.
Step 2: User sends query to EPCDS with a specific EPC number or a range of EPC numbers as well as user’s credentials as parameters.
Step 3: EPCDS uses lookup table to look up queried EPC numbers, finds corresponding EPCIS addresses and relays user’s query and credentials to those EPCIS resources.
Step 4: Each EPCIS resource checks user’s credentials against its own access control database and returns the query result to EPCDS.
Step 5: EPCDS aggregates the results and relays them back to the user.
4. Secure Discovery Service Model
Secure Discovery Service model (SecDS) is based on Directory Service Model.
As described in Section 3.1, Directory Service Model has a critical problem due to the lack of access control system in EPCDS. Sensitive business information may be leaked, since EPCDS returns related EPCIS addresses to every user query.
In SecDS model, the basic Directory Service Model is improved by implementing a secure access control mechanism inside EPCDS. Access control mechanism in EPCDS makes sure that it does not release EPCIS addresses to any unauthorized users. Confidentiality of important EPC information is preserved.
As shown in Figure 5, steps in SecDS model are the same as steps in Directory Service Model, except that in
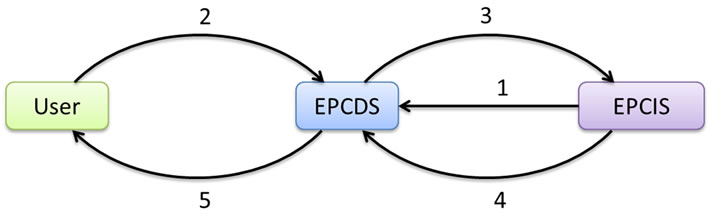
Figure 4. Steps in aggregating discovery service model.
step 1, access control policies are sent together with EPC numbers and EPCIS address from EPCIS. In addition to lookup table of EPCIS addresses, EPCDS maintain a database on access control policies in SecDS model.
Moreover, EPCDS provides interfaces for adding, deleting and modifying access control policies. EPCIS owners can use these interfaces to synchronize access control polices between EPCDS and EPCIS.
4.1. Architecture of SecDS Model
Figure 6 describes the overview EPCDS architecture of SecDS model with attribute-based access control system [10].