Towards Post-Quantum Cryptography Using Thermal Noise Theory and True Random Numbers Generation ()
1. Introduction
The emergence of quantum computers exposes classical cryptosystems. These cryptosystems whose semantic security is based on difficult mathematical problems and algorithmic complexity become vulnerable. Shor’s [1] and Grover’s [2] algorithms are a perfect illustration. The first solves the problems of large numbers factorization and discrete logarithm in polynomial time [3] while the second [4] favors cryptanalysis of the AES for size keys of 128 and 192 bits [5]. This challenge to the fundamentals of symmetric and asymmetric cryptography worries the researchers. It leads to the rise of quantum and post-quantum cryptography [6]. However, post-quantum cryptography implemented through NP-complete problems [7] cannot guarantee perfect secrecy [8]. A promising related theory is the generation of random numbers associated to quantum physical phenomenon [9]. The aim is to exploit the laws of quantum physics associated to basic principle of cryptology for the implementation of new cryptographic primitives.
In this work, we propose a random number generation model using the thermal noise theory. This model is described as a sequence of concatenation of the integer and decimal parts of the thermal power of each volume element of an electronic system. The power is evaluated by sampling the temperature in non-equilibrium state according to Fourrier’s law [10]. For a sampling period (t) with
, we prove that it is impossible for an attacker to determine exactly the variations of the temperature (
), so the sequences of generated numbers.
We devote the first and second sections respectively to an exhaustive study of TRNG using the properties of quantum physics, and the description of the proposed mechanism. In third section, we carry out the experiments and performances analysis.
2. Related Works
In this section, we make an exhaustive study of the random numbers generators based on the properties of quantum physics.
2.1. True Random Number Generator
A True Random Number Generator (TRNG) is a device able to produce a sequence of numbers for which there is no known deterministic link paradoxically to the pseudo-random number generator [9]. According to Stipcevic and Koç [11], it follows that a true random numbers is a sequence of numbers for which there is no deterministic algorithm.
In computer science, a hardware random number generator is a device that generates random numbers from a physical phenomenon rather than use of a computer program [12] [13] [14] [15]. These systems are in most cases based on laws of quantum physics and proven random phenomena. Several techniques exist for the generation of these random numbers whose properties are widely used in cryptography. These properties ensure the absolute information security. As example, we mention the techniques based on noise amplification, phase jitter in oscillators, the impact of noise on metastable behavior [16] and noise amplification based on chaos circuits [12]. These mechanisms are real entropy sources for random number generation.
However, they have the limits that require researchers to move towards other innovative primitives. For illustration purposes, research topics are oriented towards nano-devices, inverters, oxide distribution and random telegraph noise. Although these methods are efficient for producing true random numbers, their implementation proves to be complex for 14 nm processors and its derivatives [12].
2.2. Thermal Noise Study
Noise refers to all harmful signals that overlap with the useful signal at any point in a measurement chain or transmission system. The useful signal represents the information, while noise is a hindrance to understanding the information conveyed by the signal. In electronics, it presents interesting properties due to its randomness. According to Johnson-Nyquist work [17] [18], we define thermal noise as the noise generated by the thermal agitation of charge carriers. In other words, that is electrons at thermal equilibrium in electrical resistance. It is expressed:
- when we evaluate the noise across resistor [17] [18] by:
(1)
with:
: Voltage variance across the resistor,
K: Boltzmann constant,
,
T: resistor absolute temperature expressed in kelvin,
R: resistance expressed in Ohms,
: bandwidth expressed in Hertz.
This application enables to predict the minimum noise in electronic system and its detection limit:
- when we evaluate the power of thermal noise [17] [18] by:
(2)
with:
K: Boltzmann constant,
,
T: conductor temperature expressed in Kelvin,
: bandwidth in Hertz,
: thermal noise power, expressed in Watt.
Thermal noise is inevitable and unpredictable in electronic systems and has quite important characteristics when Shannon theory is associated it [19]. Indeed, by considering the noise as information source, it is possible to evaluate the quantity of derived information. In cryptography, this quantity of information is an entropic source for true random numbers generation. Through Table 1, we make a comparative study of mechanisms of which entropy describe good results for true random numbers generation [12] [16] [20].
![]()
Table 1. Comparative study of the mechanisms leading to true random numbers generation.
Scott A. Wilber [13] proposes a mechanism for non-deterministic random numbers generation. It uses an electronic assembly of two oscillators producing output signals, of which one is multiplexed. The processor extracts the entropy resulting from the fluctuation during successive emission of signals by the two oscillators for true random numbers generation. The author mention that random number generators use physical sources of entropy evaluation. This value is then used as information source for true random numbers generation. Thus, it is possible to establish a hypothesis between the entropy and its evaluation sources. However, we estimate that Scott A. Wilber’s approach inherits the limits of the oscillatory phenomena due to periodic properties of these phenomena. Indeed, study and determination of the frequencies of emitted signals by each oscillator influence the entropy. The device is therefore vulnerable to side channel attacks. Let’s consider g, as the fluctuation between two signals according to time t and respectively frequencies
,
, if:
(3)
an attacker who studies behavior of the system, could compute the entropy accurate values. Therefore, they are many theories and implementation for true random numbers generation [21] [22]. Despite research efforts, the weaknesses persist and the semantic security still a great challenge due to advances in the implementation of quantum computers and side channel attacks. So, new theories need to be developed.
3. Architecture of Proposed Mechanism
In this section, we present logical structure of the proposed true random number generation mechanism. Also we perform the tests.
3.1. Logical Structure
Let’s consider an embedded system in non-equilibrium state. Its density is given by:
(4)
with:
: density expressed in kg∙m−3,
m: mass expressed in kg,
v: volume expressed in m3.
According to Fourier’s law [10] this non-equilibrium state generates a variation in temperature and creates a heatflow defined by:
(5)
with:
F: heatflow in Watts,
S: plane area expressed in m2,
I: thermal conductivity expressed in W∙m−1∙K−1,
: temperature gradient expressed in K∙m−1.
Let’s consider:
a volume element of embedded system defined by:
(6)
: the measured temperature according to time (t) and space (
). We evaluate it considering two parameters:
- time(t): it is sampling period of temperature;
- volume element (
): it is the volume element considered during temperature evaluation. The evaluation of thermal noise power in relation to its volume element is defined by:
(7)
with:
K: Boltzmann constant,
,
: volume element temperature expressed in Kelvin,
: bandwidth expressed in Hertz,
: thermal noise, expressed in Watt.
Let’s consider:
and
respectively as the integer part and the decimal part of the thermal noise power.
TRNG as the concatenation of
and
(
) such as :
(8)
where
: the sequence of random numbers generated and
the clock step of each temperature evaluation. Also, we describe through an algorithm, the proposed mechanism for true random numbers generation.
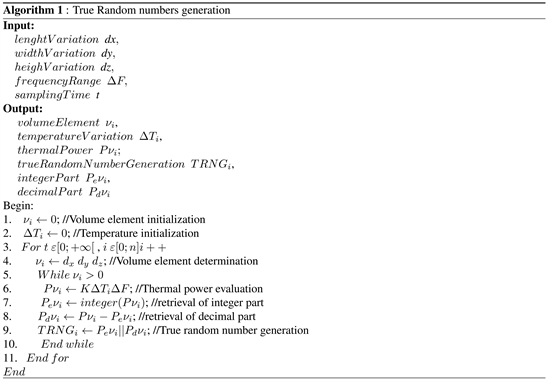
3.2. Security Proof
We evaluate the robustness of the proposed mechanism through the notion of entropy derived from Shannon [23] and Yamamoto [24] and the constraints to which the model is subjected:
- the numbers are generated following the measured temperature (
) within each volume element (
) of the proposed device;
- the measured value determines the power (
) of the thermal noise.
Let’s note respectively: X, Y, Z the random variables associated to the sources (
), (
), (
) and H(X), H(Y), H(Z), their entropies.
Let’s consider the determination of the thermal noise power of a volume element as a source of information. Its probability and entropy follow respectively the relation:
(9)
(10)
(By identification following to (10));
with:
.
For an infinity of volume elements (z),
:
1)
(equiprobability);
2)
(nonequiprobable due to the source (
);
3)
.
From 1), 2) and 3), we have:
(11)
Thus, an attacker has none information to determine the thermal power of each volume element.
We conclude that the proposed mechanism is efficient.
3.3. Description of Experimental Environment
We use an Arduino Uno ATMega 328p [25] as source of the thermal noise. It generates a solid (
) of space (
).
We mention that the function which characterizes each volume element of the solid (
) is defined by:
(12)
We define by framing in black (Figure 1) the considered volume elements during the temperature evaluation. They are referenced by numbering. We perform the tests on a set of 7 volume elements.
For each volume element of the electronic system, we deploy a temperature sensor type LM 35. Then, we determine the power for each volume element according to the temperature values measured.
We summarize through Table 2 and Table 3, the obtained results following the experiments.
![]()
Table 2. Obtained results (Power computation).
![]()
Table 3. Obtained results (Retrieval of integer part and decimal part).
4. Analysis and Discussions
We devote this section to the analysis of the results obtained during the tests. Thus, Figures 2-4 represent graphs relating to the achieved results during the experiments. It is constant to note that the thermal noise power varies for each volume element at Figure 4. This variation happened due to changes of the temperature for each volume element over a time. Thus, the thermal noise power in a volume element means the determination of the following parameters: Temperature (T), time (t), and volume element (
). We conclude that the power varies according to temperature, volume element and time. As a result, the generated numbers vary in time and space and do not follow any deterministic approach. Therefore, they are deemed to be true and random.
We generate a number by concatenation of the integer and decimal parts of the thermal noise power obtained per volume element ignoring the decimal point. A sequence of generated numbers is equivalent to a sequence of concatenation of integer and decimal parts of the power of each volume element according to its assignment index j. So:
for
For 7 volume elements, we get a sequence of random numbers of 187 digits distributed as follows:
Let’s note:
: number of digits for each volume element,
: number of digits enumerated for the integer part of each volume
,
: number of digits enumerated for the decimal part of each volume element
. The results are represented in Table 4.
Therefore, for z volume elements,
, it is very difficult for an attacker to determine exactly the different temperatures within each volume element and:
![]()
Figure 2. Variation of temperature depending on volume elements.
![]()
Figure 3. Sampling the temperature for each volume element.
![]()
Figure 4. Variation of temperature depending on the power of thermal noise.
![]()
Table 4. Number of digits counted per volume element.
The obtained TRN is converted into binary and recovered as a keystream. This keystream will be transmitted from the transmitter to the receiver through quantum cryptography properties. We will associate it on-time pad cryptographic method to secure the transmitted data.
5. Conclusion
In this paper, we have proposed a mechanism for true random number generation which can resist to an attacker with quantum computers. This mechanism uses the fundamentals of thermal noise theory which is a random phenomenon. For tests and experiments, we used an ATMega microcontroller as a solid space that generates volume elements. We sample the temperature of these volume elements to determine the power of thermal noise for each volume element. Thus, we have obtained for 7 volume elements, a series of random numbers of 187 digits which conversion into binary represents the cryptographic key. Our analysis shows that it is not possible for an attacker to determine the generated sequence numbers for infinity of volume elements. In future work, we will propose a quantum cryptography mechanism to exchange the generated keystream and associate it the One-Time Pad cryptographic method.
Acknowledgements
The authors would like to thank the reviewers for their constructive comments. Many thanks to the Doctoral School of University of Burundi, IMSP-UAC of Benin and Antenne Afrique des Grands lacs de l’AUF-Burundi for their support.