1. Introduction
A semiprime is an odd composite number N that has exactly two distinct prime divisors, say p and q, such that
. Factorization of the semiprimes has been a difficult problem in mathematics and computer science, especially factorization of a RSA number that is a large semiprime, as introduced and overviewed in articles [1] [2] [3] [4] [5] . Let
be the divisor-ratio of the semiprime
; article [6] discovered the genetic property of the odd integers and proved that the small divisor p can be calculated by finding the greatest common divisor (GCD) with an odd integer that lies in an odd interval
that is determined by N itself; article [7] further pointed out that, by taking k to be a variable quantity, algorithms could be designed to factorize big semiprimes by parallel computing and the article also demonstrated a deterministic approach to factor the RSA numbers; article [8] recently made a further investigation on k’s influence to the distribution of p, showing that the interval
is a cover of finite subintervals each of which is determined by a k and every two adjacent ones of which are linked with their unique common end. This means that p can be surely found out with a k-subdivision approach. Following such an idea, this paper makes an investigation on the new algorithm design for searching the odd integer that has GCD with N. As a result, an algorithm that incorporates a deterministic search with a probabilistic search is designed. This paper presents the related consequences. Section 2 lists the preliminaries for the later sections; Section 3 proves the mathematical foundations for the new algorithm; Section 4 introduces the new algorithm as well as its designing strategy and numerical experiments.
2. Preliminaries
This section lists the preliminaries that include definitions, symbols and lemmas, which are necessary for later sections.
2.1. Symbols and Notations
In this whole article, a semiprime
means p and q are both odd prime numbers and
. An odd interval
is a set of consecutive odd numbers that take a as the lower bound and b as the upper bound; for example,
. Symbol
is the floor function, an integer function of real number x that satisfies
; symbol GCD means the greatest common divisor; let
; then
,
,
and
are defined by
Symbol
, which was defined in [8] , means A is half of B.
2.2. Lemmas
Lemma 1. (See in [8] ) Suppose
is an odd composite number and
; then
, where
,
,
and
.
Lemma 2. (See in [8] ) Suppose
is an odd integer and
are positive integers. Let
,
,
and
; then it holds
where
,
,
and
.
Particularly, when
it holds
Lemma 3. (See in [8] ) For arbitrary odd number
, let
,
,
and
, where
are positive integers; then odd intervals
satisfy
1)
;
2)
;
3)
; as illustrated in Figure 1.
Lemma 4. (See in [8] ) Let
be the length of the odd interval
,
and
be respectively the lengths of the odd intervals
and
defined in Lemma 3; then when
, it holds
.
Lemma 5. (See in [8] ) Let
be the length of the odd interval
,
,
and
, be respectively the lengths of
,
and
; then
and when
it holds
.
Lemma 6. (See in [8] ) If
for some positive integers
and
, then
is at most
; otherwise it is at least
![]()
Figure 1. Odd intervals’ subdivision and cover.
. Particularly, arbitrary
yields
for
and
for
.
Lemma 7. (See in [8] ) Let
be odd intervals defined in Lemma 3;
then there are intervals that contain at most
nodes and there are intervals that contain at least
nodes.
3. Algorithm Design and Numerical Experiments
Based on the previous lemmas, theorems and corollaries, one can easily draw the following conclusions.
1) If
is a semiprime, then there is a term
that lies in the odd interval
and satisfies
;
2) If
is subdivided into a series of subintervals that are defined in Lemma
3, then
with
, and the bigger k is the fewer nodes are
contained in
. Among all the subintervals,
,
and
dominate half of
. Lemma 6 shows that, when
there are at least
nodes in
.
These provide a guideline for designing new algorithm for integer factorization, as the following subsections demonstrates.
3.1. Strategy for Algorithm Design
Now it has gotten to know that finding
out means a successful factorization of
. Since
hides itself in one of
, it can surely be found out by searching the intervals one by one. Considering by Lemma 7 that there are intervals that contain small number of nodes that can be searched in small time and there are also intervals that contain too many nodes to be searched when N is very big, it is necessary to know which intervals contain small number of nodes and which ones contain large number of nodes and then perform a brute-force search on the small ones and perform other searches on the large ones. Since the brute-force search is a time-consuming process, a Tolerable Number (TN) can be defined to be an upper bound of nodes that are sure to be searched out in a Tolerable Time (TM), which was introduced in FU’s article [9] . Obviously, Lemma 6 indicates that TN can be used to determine
by
and thus
. Since the number of nodes in
is
smaller than that in
if
by Lemma 6, TN is a critical number for the brute-force search. All the intervals
can be searched by the brute-force search.
Now it turns to the big intervals
, each of which contains more than TN nodes. It is sure that, applying TN to subdivide each of these big intervals can obtain a series of new small odd intervals and then assigning each of the newly-subdivided small subintervals a process in a parallel computing system can perform the brute-force search in TM, as tested by FU [9] . However, this might require huge computing resources. For example, FU’s approach took more than 8 days to factorize a big number of 46-decimaldigits on Chinese Tianhe Supper Computer with 392 processes. On the other hand, by Lemma 3, there is a big probability to find the objective node when applying a probabilistic approach. Thus it is worthy of trying a probabilistic search.
By now, setting a TN, calculating an
by
plus an
by
and imagining varying
result in a subdivision of the
interval
into two kinds of subintervals, the kind of small ones and the kind of big ones, as shown in Figure 2. Each of the small ones contains no more than TN nodes and can be searched by the brute-force search while each of the big ones contains more than TN nodes that need probabilistic searching approaches to search.
Now consider a big odd subinterval I that contains n terms. Suppose the objective odd number
lies at the m-th position. Referring to the analysis in [10] , it knows that, choosing randomly k (
) terms on the left of o, say
, and their respectively symmetric terms on the right of o, namely,
, yields
with
. Therefore, choosing in I randomly 2k terms and adding the chosen terms might obtain o in big probability, as proved in [10] . With the help of multi-dimensional random-number generator, as introduced in [11] , it is easy to pick 2k random terms in I. Considering the case that o lies near the start-position or the end-position of the interval I might fail to pick the necessary number of terms, it is reasonable to make near I’s ends one or more small subintervals each of which contain TN of nodes. These small subintervals are called TN intervals and they can be searched in TM with brate-force searches. The remained part of I is called a probabilistic intervals, as shown in Figure 3. Such a subdivision that includes two TN intervals near the ends and a probabilistic interval in the middle is called a TNPTN subdivision. With the TNPTN subdivision, it is necessary to perform brute-force searches on the two TN intervals and a probabilistic search on the whole interval I.
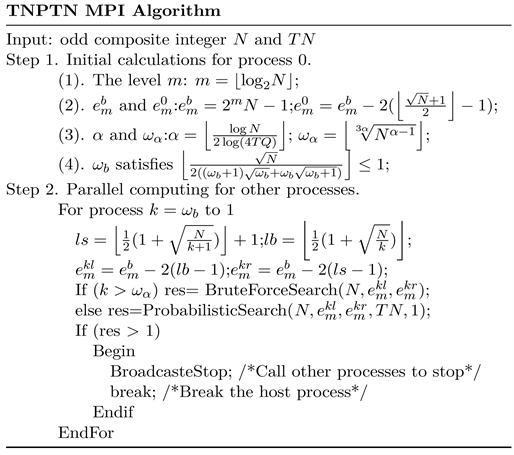
3.2. TNPTN Parallel Probabilistic Algorithm
Based on the strategy for algorithm design stated in previous section, a parallel algorithm, which is called TNPTN MPI Algorithm, is designed to find an
objective node
that has common divisor p with
. The algorithm assumes that
varies from 1 to an upper bound and assigns for each k a process to search
. It requires initial input data N to be the big semiprime, TN to be the number of the maximal steps that a brute-force search performs and a number
with
to set the number of random odd integers that are randomly picked in its searched interval with the multi-dimensional random-number generator introduced in [11] . It also requires a brute-force searching subroutine and a probabilistic searching subroutine to perform the operations.


3.3. Numerical Experiments
Numerical experiments were made on a Sugon workstation with Xeon(R) E5-2650 V3 processor of 20 cores and 128GB memory via C++ MPI programming with gmp big number library. Several big semiprimes with 27 to 46 decimal-digits are factorized, as shown in Table 1.
4. Conclusion and Future Work
It is a convention to make a comparison of a new approach to the old ones although, sometime, there is no comparability between two things. Accordingly, this section makes comparisons and then prospects some future work.
It can see from the implementation of algorithms list in previous section that, each of the algorithms 1, 2 and 3 needs memory only for storing a few integers to be taken into the computation. They cost less memory. Since the whole procedure is a parallel one, the time it costs depends on the resources joining the computation. Theoretically, it is at most
bit-operations
providing that there is
process joining the computation.
Now turn to the old ones. It is known that, ever since John Pollard raised in 1975 his Pollard’s Rho algorithm, which is a probabilistic algorithm and is efficient in factoring small integers, many algorithms of integer factorization have developed. As stated in the introductory section, the GNFS has been regarded the fastest approach to factorize big integers under both sequential and parallel computing and almost all the factorized RSA numbers are factorized by the approach with parallel computing. So here the new approach is merely compared to the Pollard’s Rho approach and the GNFS approach.
![]()
Table 1. Experiments on some big semiprimes.
First compare with the Pollard’s Rho approach. From the point-view of memory cost, the new approach is like the Pollard’s Rho approach that costs less memory. From the point-view of time consumption, the two are almost the same efficiency according to the experiments in articles [6] and [12] . However, as pointed out in article [13] , the Pollard’s Rho approach cannot be parallelised. Actually, this article is the first one that proposes a parallel probabilistic approach in factoring integers.
Next compare with the GNFS approach. The GNFS approach is a deterministic one that can be parallelised. As article [14] has pointed out, GNFS requires a large amount of memory. Hence from the point-view of memory cost, the new approach is superior to the GNFS. From the point-view of time consumption, the comparison cannot be available because the new approach has not been applied on the many computers as the GNFS used in factoring large RSA numbers. Nevertheless, it can see from the experiments of factoring the 46 decimal bits semiprime that, one computer of 20 cores can factorize it in 3 days.
There is another approach stated by Kurzweg U H [15] . Seeing from his series of Blogs, one can see that Kurzweg actually tried to find out
to factorize the semiprime N. The idea was early seen in chapter 6 of YAN’s book [1] . Actually, it is quite occasional for Kurzweg’s to factorize the numbers he reported because he has not brought an approach that finds out
inevitably.
By now it can see that, the approach raised in this article is surely worthy of investigation because it is truly derived from the theorems and corollaries that are proved mathematically. In spite that the new approach is less of successful cases of factoring the RSA numbers, it does factorize many odd integers as many old approaches did in the history. As a new approach, it leaves of course quite a lot of researches to improve and perfect. For example, the probabilistic searching procedure is very rough and needs improving, and the time complexity of the algorithm has not be evaluated till now for its probabilistic trait and also for the authors’ limitation of the required knowledge. This points out the study of the future work. Hope it is concerned more and successful in the future.
Acknowledgements
The research work is supported by the State Key Laboratory of Mathematical Engineering and Advanced Computing under Open Project Program No.2017A01, Department of Guangdong Science and Technology under project 2015A030401105, Foshan Bureau of Science and Technology under projects 2016AG100311, Project gg040981 from Foshan University. The authors sincerely present thanks to them all.