Journal of Quantum Information Science
Vol.04 No.04(2014), Article ID:52818,4 pages
10.4236/jqis.2014.44024
Three-Party Simultaneous Quantum Secure Communication Based on Closed Transmission Loops
Xunru Yin1,2
1Department of Mathematics and Systems Science, Taishan University, Tai’an, China
2State Key Laboratory of Integrated Service Networks, Xidian University, Xi’an, China
Email: xryin@outlook.com
Copyright © 2014 by author and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 12 October 2014; revised 7 November 2014; accepted 2 December 2014
ABSTRACT
A kind of novel three-party quantum secure direct communication protocol is proposed with the correlation of two-particle entangled state. In this scheme the qubit transmission forms a closed loop and every one of the three participants is both a receiver and a sender of particle sequences in the bidirectional quantum channels. Each party implements the corresponding unitary operations according to its secret bit value over the quantum channels and then extracts the other two parties’ unitary operations by performing Bell measurements on the encoded particles. Thus they can obtain the secret information simultaneously. Finally, the security analysis shows that the present three-party scheme is a secure protocol.
Keywords:
Quantum Information, Quantum Cryptographic Protocol, Quantum Secure Direct Communication, Bell States

1. Introduction
Quantum key distribution (QKD) is based on quantum mechanics and has the unconditional security, in which all legitimate users can distribute a shared key beforehand to make secure communications. Different from QKD, quantum secure direct communication (QSDC), another important application of quantum cryptography, can allow the messages to be read out after qubit transmission and then exchange the secret information between all parties directly without distributing a shared secret key.
In 2002, Long et al. [1] presented the first QSDC protocol by using EPR entangled states. Then Beige et al. [2] proposed a QSDC scheme with the exchange of single photons. In the same year, Boström and Felbinger [3] proposed a deterministic secure direct communication scheme named “ping-pong” protocol based on two-pho- ton entangled states, which was improved by Li et al. [4] . Deng et al. [5] proposed two-step quantum direct communication protocol using the EPR pair block. However, the transmission of secret messages is unidirectional in QSDC. Then Nguyen [6] proposed a kind of protocol called quantum dialogue. Later, Jin et al. [7] proposed a three-party quantum secure direct communication based on the GHZ states, which was improved by Man et al. [8] . Wang et al. [9] proposed a three-party QSDC scheme with EPR pairs, and their protocol was improved on the quantum channels and the efficiency by Chong et al. [10] . Unfortunately, in 2013, Yin et al. [11] pointed out that [9] [10] can leak out the secret messages of the legitimate users with the classical correlation or information leakage [12] . In the same year, we [13] proposed an efficient quantum secure communication with two-photon entanglement.
In this paper, we propose a novel three-party QSDC protocol by using the idea of quantum dense coding on the two-particle EPR pair. The three parties in our scheme are peer entities and they transmit the particle sequences each other synchronously in a closed loop of qubit transmission. One party can obtain the other two parties’ secret messages through performing the joint measurement on the encoded particles. The rest of our scheme is structured as follows. Section 2 describes the whole protocol in detail. Section 3 analyzes the security of this protocol. Finally, Section 4 gives a conclusion briefly.
2. Description of the Present Protocol
The four Bell states can be written as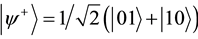 ,
, 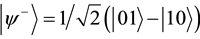 ,
, 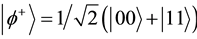 ,
,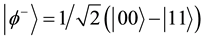 . Where
. Where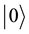 ,
, 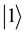 are the up and down eigenstates of Pauli operator
are the up and down eigenstates of Pauli operator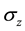 . Let
. Let
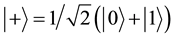 ,
,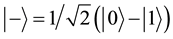 . Then
. Then 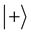 and
and  are the eigenstates of Pauli operator
are the eigenstates of Pauli operator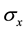 .
.
Suppose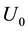 ,
, 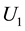 and
and 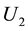 are three unitary operations, That is,
are three unitary operations, That is, 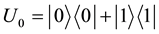 ,
, 






Now, we suppose Alice, Bob, and Charlie as the three parties in our scheme. Let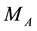


where



If the encoded particle is the second qubit, the rule is the following
Table 1. Encoding rule in the present protocol.

Next, we describe this protocol in detail.
Step 1. Alice/Bob/Charlie prepares 









Step 2. After confirming (Bob, Charlie)/(Charlie, Alice)/(Alice, Bob) has received the mixed sequences, Alice/Bob/Charlie publishes the positions and the measurement basis 

Step 3. After picking out the decoy particles, Bob/Charlie/Alice performs the unitary operations on 






Step 4. After confirming that Alice/Bob/Charlie has received the mixed two sequences, the other two parties announce the positions and the corresponding measurement basis of the decoy particles. Then they check the security of quantum channels by comparing the measurement results of the decoy particles. If the error rate does not meet the requirement, the three parties abort the protocol; otherwise, they continue it.
Step 5. Alice/Bob/Charlie first picks out the decoy particles. Now, each party has two encoded sequences and performs Bell measurement orderly on the corresponding photon pairs in this two sequences, for instance, Alice performs Bell measurement on the EPR pairs in 

From the above steps, we can see the qubit transmission forms a closed loop and every party sends or receives particles simultaneously. For conciseness, we take 
and


respectively. Bob performs 





3. Security Analysis
Now we analyze the security of our scheme. From the five steps, we can see that there must be a security check over quantum channels when one party sends a particle sequence to another party. On the other hand, the decoy particles are chosen from 








Then the whole system is in the state
where
If Eve wants to avoid any error, the following conditions should be satisfied
According to the above equations, we can have
On the other hand, in the security check step, the measurement basis are chosen from 

From the correlations of Bell states, the state 
Then the whole quantum system is in the following state
Similarly, from the above formula and the correlations of



That is, regardless of what the legitimate users take the measurement basis, the eavesdropper Eve cannot extract any useful information of the secret messages by observing the ancillary particle. Then our scheme is secure according to the above analysis and discussion.
4. Conclusion
In this paper, we propose a three-party quantum secret direct communication protocol with the bidirectional qubit transmission. In the whole process, we can see that all the parties form a return qubit circuit and they are peer entities. The three parties can exchange their own secret messages by using Bell measurement and unitary operations over the quantum channels. This scheme has a novel characteristic for the quantum return circuit and the member equivalence. However, the security discussion is based on the condition of ideal quantum channels. We have not considered the actual physical environment. In the quantum channel, noise and loss cannot be ignored with the particle transmission because they reduce the efficiency of quantum communication and increase the risk of information leakage. With the existing technologies, it has become more difficult to study such quantum communication protocols. We hope this problem can be solved in future research.
Acknowledgements
This work was supported by the Shandong Provincial Natural Science Foundation (No. ZR2013FQ011), the Project of Shandong Province higher Educational Science and Technology Program (No. J13LN60), Technology Development Projects of Tai’an (No.20140629-2) and Project of Taishan University Doctoral Fund (Y-01-2014020).
References
- Long, G.L. and Liu, X.S. (2002) Theoretically Efficient High-Capacity Quantum Key Distribution Scheme. Physical Review A, 65, Article ID: 032302. http://dx.doi.org/10.1103/PhysRevA.65.032302
- Beige, A., Englert, B.G., Kurtsiefer, C., et al. (2002) Secure Communication with a Publicly Known Key. Acta Physics Polonica A, 101, 357-368.
- Boström, K. and Felbinger, T. (2002) Deterministic Secure Direct Communication Using Entanglement. Physical Review Letters, 89, Article ID: 187902. http://dx.doi.org/10.1103/PhysRevLett.89.187902
- Li, J., Jin, H. and Jing, B. (2011) Improved Quantum “Ping-Pong” Protocol Based on GHZ State Operation. Science in China Series G, 54, 1612-1618. http://dx.doi.org/10.1007/s11433-011-4448-0
- Deng, F.G., Long, G.L. and Liu, X.S. (2003) Two-Step Quantum Direct Communication Protocol Using the Einstein- Podolsky-Rosen Pair Block. Physical Review A, 68, Article ID: 042317. http://dx.doi.org/10.1007/s11433-011-4448-0
- Nguyen, B.A. (2004) Quantum Dialogue. Physics Letters A, 328, 6-10. http://dx.doi.org/10.1016/j.physleta.2004.06.009
- Jin, X.R., Ji, X., Zhang, S., et al. (2006) Three-Party Quantum Secure Direct Communication Based on GHZ States. Physics Letters A, 354, 67-70. http://dx.doi.org/10.1016/j.physleta.2006.01.035
- Man, Z.X. and Xia, Y.J. (2007) Improvement of Security of Three-Party Quantum Secure Direct Communication Based on GHZ States. Chinese Physics Letters, 24, 15-18. http://dx.doi.org/10.1088/0256-307X/24/1/005
- Wang, M.Y. and Yan, F.L. (2007) Three-Party Simultaneous Quantum Secure Direct Communication Scheme with EPR Pair. Chinese Physics Letters, 24, 2486-2488. http://dx.doi.org/10.1088/0256-307X/24/9/007
- Chong, S.K. and Hwang, T. (2011) The Enhancement of Three-Party Simultaneous Quantum Secure Direct Communication Scheme with EPR Pairs. Optics Communication, 284, 515-518. http://dx.doi.org/10.1016/j.optcom.2010.08.037
- Yin, X.R., Ma, W.P., Shen, D.S. and Hao, C. (2013) Efficient Three-Party Quantum Secure Direct Communication with EPR Pairs. Journal of Quantum Information Science, 3, 1-5. http://dx.doi.org/10.4236/jqis.2013.31001
- Gao, F., Guo, F.Z., Wen, Q.Y., et al. (2008) Revisiting the Security of Quantum Dialogue and Bidirectional Quantum Secure Direct Communication. Science in China Series G, 51, 559-566. http://dx.doi.org/10.1007/s11433-008-0065-y
- Yin, X.R., Ma, W.P., Liu, W.Y. and Shen, D.S. (2013) Efficient Bidirectional Quantum Secure Communication with Two-Photon Entanglement. Quantum Information Processing, 12, 3093-3102. http://dx.doi.org/10.1007/s11128-013-0584-y














