Novel Scheme for Compressed Image Authentication Using LSB Watermarking and EMRC6 Encryption ()
Received 15 April 2016; accepted 12 May 2016; published 17 June 2016

1. Introduction
In the recent era where the data are being transformed into digital content, the need for security of medical images becomes intense. Digital Asset and Right Management Systems (DARMS) is intended to be used with data that are either encrypted or compressed. Encryption schemes are used to provide security to digital data like text, image, audio, video, etc. Encryption is a process in which the input is combined with a key to produce an output that is not in the human readable form. Similarly watermarking methods are used to minimize forgery in the digital data that is being stored in a computer or being transferred over the network.
The method of embedding an image inside the cover image for the purpose of security is called watermarking. Larobina explained various medical image formats that can be used for watermarking [1] . As compressed images are mainly used as input in digital watermarking algorithms, Rabbani described a lossless image compression format for storing images of any type that occupies less storage space in [2] . To overcome the weaknesses of digital signature for content authentication, many researchers proposed watermarking techniques for digital data authentication. In digital signature, content modification or data tampering can be found out. But the location where such alteration has been found could not be identified [3] - [6] .
In addition to watermarking techniques, encryption schemes increase the reliability and security of digital content. Depending on the technology used, cryptographic methods are difficult to detect. The usage of an additional key makes it more robust. Watermarking is said to be a form of communication, since the basic task of watermarking is the reliable embedding and detection of digital content. Secure delivery of content is a major task of cryptography in addition to providing reliability. The decrypted form of the content has no protection in cryptography, but it is complimented by watermarking techniques by embedding the watermark inside the digital content. Thus the “analog hole” created by encryption schemes can be sealed by watermarking techniques [7] - [10] .
Lot of researchers combined watermarking schemes with encryption algorithms to increase the security of the digital content. RSA, Paillier, Goldwasser-Micali, Elgamelare asymmetric encryption schemes with homomorphic property and they have their downsides. There is loss of compression efficiency in the output cipher text if the message size is small and compression loss is reduced, but the payload capacity decreases if the message size is large in the above said schemes [11] - [14] .
The downsides of those are overcome by RC4 symmetric stream cipher scheme with homomorphic property which was proposed by Subramanyam et al. [15] . The chances of data trade-off attacks which are based on the key scheduling algorithm are caused by low sampling resistance in RC4 [16] . The symmetric block cipher RC5 which is more secure and robust than RC4 due to its increased number of rounds to work with the watermarking schemes used in [15] was proposed by Gayathri I.K. [17] . With less than 18 rounds RC5-64 algorithm (64-bit blocks) is prone to differential attack, when the chosen plain text is 244 [17] . RC6 is being used instead of RC5 due to its increased use of registers which was proposed by Kukoo Anna Mathew [18] .
Elashry in [19] proposed a method in which LSB is integrated with RC6 to provide security with good image quality. But RC6 undergoes differential linear attack, statistical attack and X2 attack [20] - [22] . Later to overcome the disadvantages of RC6 an Enhanced version of RC6 (ERC6) is used. It has 8 working registers and it acts on 256-bits input/output blocks.ERC6 encrypts at about 17.3 MB/sec making it about 1.7 times faster than RC6. But it is prone to X2 attack up to 44 rounds [23] .
So in order to overcome the drawbacks of ERC6 a modified version of RC6 (MRC6) is being found with better performance. It uses sixteen working registers instead of four registers in RC6. MRC6 achieves greater security at fewer rounds thus increasing the throughput with minimum encryption/decryption time [24] . But the Enhanced Modified Version of RC6 (EMRC6) has 32 working registers instead of sixteen in MRC6, and integer multiplication is used as an extra primitive operation which intensifies the diffusion obtained per round thus attaining high security and maximum throughput in less number of rounds [25] .
LSB technique is used where the embedding process is simple. It is one in which the image pixels of the cover image are replaced by the bits from the secret message. Embedding can be done in any of the eight bits in a bit plane. Bamatraf proposed a LSB technique where the hiding of data is done in the third and fourth LSB of the cover image [26] .
Singh et al. proposed a watermarking method using replacement of second LSB with inverse of LSB which is a powerful method for image authentication and copyright protection [27] . Puneet analysed various image watermarking using LSB algorithms and the results show that the hiding of the secret data in the first bit is without noticeable distortion on it [28] .
The current work is intended to convert the input into JPEG2000 format and encrypt the watermark with LSB watermarking scheme and then watermarking the encrypted watermark with EMRC6 encryption scheme so as to provide content authentication.
Figure 1 shows the basic model for content authentication, in which the cover image is a color image and the watermark image is the one that has to be embedded in to the cover/input image. The watermark image in encrypted using any encryption scheme and the output encrypted watermark is then watermarked using any spatial or frequency domain watermarking algorithm producing the final watermarked output.
2. Proposed System
The proposed system is aimed at combining LSB watermarking method with Enhanced Modified Version of RC6 (EMRC6) encryption scheme to provide content authentication for compressed images. The cover image “I” may be of any image type and is given as input to the JPEG2000 encoder. The JPEG2000 encoder processes the input image by undergoing five stages by dividing the image into rectangular tile that does not overlap and then it undergoes discrete wavelet transformation (DWT) and is quantized and is further divided into different bit planes.
This is then block coded with optimized truncation which results in stream of compressed byte which is packed into different wavelet packets. This JPEG2000 encoded output is represented as “Ij”.
The watermark image represented as “Wm” is encrypted using Enhanced Modified Version of RC6 (EMRC6). The encryption process takes the input watermark and is converted into stream of bits. This is encrypted using the key “K” which is generated from the key of “b” bytes supplied by the user. The encryption process has a round function which has 16 rotations per round. The input stream undergoes 18 such rounds to produce the output ciper “Ew”. The Encoded cover image “Ij” and the output cipher “Ew” are given as input to the LSB watermarking scheme
The LSB embedding scheme replaces few characteristics of the last bit of each pixel of the cover image “Ij” with few information from the watermark image “Wm”. A pseudo Random Number generator (PRNG) that produces a seed value is used with the LSB embedding in order to overcome the attacks on LSB embedding since LSB is a fragile scheme. Thus the output of the embedding process is the watermarked image “We” which is highly secure and has good image quality. The Peak signal to noise ratio (PSNR) value is high and the Mean Square Error (MSE) value is low when compared to the previous method where LSB technique is integrated with MRC6. This method increases embedding volume and make the watermark more secure thus providing content authentication for compressed medical images. Figure 2 shows the embedding of the watermark in the encrypted image.
![]()
Figure 1. Basic model for content authentication.
2.1. JPEG2000 Encoder
In the Proposed algorithm the input is any image and this image is converted into JPEG 2000 compressed code image using JPEG 2000 encoder by undergoing five steps. First the image is split into non overlapping tiles which are unsigned values and is reduced by a constant value. Then Discrete wavelet Transformation (DWT) is done followed by quantization and further the co-efficient are split into different bit-planes using embedded block coding with optimized truncation (EBCOT) coding method. As a final step compressed stream are packed into different wavelet packages [29] .
2.2. Enhanced Modified Rivest Cipher 6 (EMRC6)
EMRC6 (32/18/16) has 32 registers each with ‘w’ bit words, whereas the working registers is less in numbers in the previous version of RC6. EMRC6 has an integer multiplication as an extra basic operation which increases the diffusion attained per round. This provides high security, increase in number of rounds and greater throughput. It can process 1024 bits as a single block per round. The EMRC6 algorithm has three basic modules.
1) EMRC6 key expansion.
2) EMRC6 encryption.
3) EMRC6 decryption.
2.2.1. EMRC6 Key Expansion
The key expansion algorithm of EMRC6 is almost similar to the one in the previous version of RC6. But the main difference in EMRC6 is, more number of words are extracted from the key supplied by the user. The key of length “b” bytes where 0 ≤ b ≤ 255 is supplied by the user. To this user defined key, enough zeroes are added to make the length of the key equal to non-zero integral values and stored in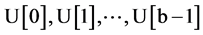 . These user supplied “b” bytes of keys is stored in another array “V” in the little endian format as
. These user supplied “b” bytes of keys is stored in another array “V” in the little endian format as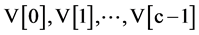 . The values from “V” table is expanded and stored in a table
. The values from “V” table is expanded and stored in a table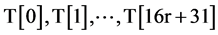 , thus producing 16r + 32 sub keys. The left barrel shifter shifts the sub keys by three positions and the resultant is stored again in “T” table. The below algorithm shows the key expansion algorithm of EMRC6.
, thus producing 16r + 32 sub keys. The left barrel shifter shifts the sub keys by three positions and the resultant is stored again in “T” table. The below algorithm shows the key expansion algorithm of EMRC6.
The two values Pw and Qw are called magic constants and is defined as
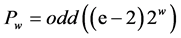 and (1)
and (1)
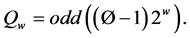 (2)
(2)
where
e = 2.7182818 and Ø = 1.618033 is called the golden constant.
2.2.2. EMRC6 Encryption Algorithm
EMRC6 encryption module convert the input into the cipher output using the generated sub key. It uses 32 working registers (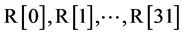 ) to store the initial input and the final output. The steps involved in EMRC6 encryption is
) to store the initial input and the final output. The steps involved in EMRC6 encryption is
・ Addition (+)
・ Bitwise EX-OR operation
・ Left rotation, a <<< b.
・ Integer Multiplication modulo 2n (*).
The 32 working registers contain the initial input for the encryption process represented as R[ ]. The first byte of the input is stored in the LSB of first register i.e., R[0] and the last byte is stored in the MSB of the last register. For example, the assignment from right to left is parallel as (R1, R2, R3, R4) = (R2, R3, R4, R1).
2.2.3. EMRC6 Decryption Algorithm
The EMRC6 decryption process reproduces the original content from the cipher using the sub key. This is the inverse operation of EMRC6 encryption. The following algorithm represents the EMRC6 decryption process. Various steps involved in decryption process are
・ Integer subtraction (−)
・ Bit wise EX-OR
・ Integer multiplication
・ Right shift, a >>> b.
2.3. LSB Watermarking
Least significant Bit (LSB) technique is based on exchanging few characteristics of each pixel’s last bit with some of the information from the input image. The embedding can be done in any of the bit plane, but LSB embedding focuses on embedding in the least significant bit of each pixel. This bit plane is chosen in order to reduce the difference in colors in the watermarked image. Basically LSB embedding scheme is fragile and hence it can be easily broken. But it is being widely used because of its simplicity. This overcomes cropping attack but undergoes a number of attacks if all the LSB is changed to one. For example, Let “01110100” be the bits to be embedded into the least significant bit (LSB) of the input image values. The watermarked output obtained using LSB technique for the given sample input is shown in Table 1.
2.3.1. LSB Embedding Algorithm
The steps in LSB embedding algorithm is listed below
・ “Ew” is read and is stored as matrix element “Ew[][]”.
・ “Ij” is normalized and rounded off to the adjacent integer with a bit precision of eight.
・ Determine the size of “Ew” and “Ij”.
・ Expand “Ew[][]” such that the size of watermark is same as that of “Ij”. The Components in “Ew[][]” are individual bits that represent pixel values of the “Ew”.
・ “Ij” is split into pixel and stored in “Ij[][]”.
・ LSB of each element from “Ij[][]” is replaced by the matching elements from “Ew[][]”.
・ The resultant matrix is converted into the watermarked image.
2.3.2. LSB Extraction Algorithm
The steps in LSB extraction process is listed below
・ “We” is read and the pixel values are stored in “We[][]”.
・ Find the size of “We”.
・ An expansion matrix is formed by extracting the LSB of each pixels from “We[][]”.
・ The bits per pixel of “We” are determined and the bits are clustered based on it. The expansion matrix consists of repeated pattern of bits at constant intervals.
・ Thus multiple watermarks are recovered inside the expansion matrix.
3. Analyzing and Evaluating the Performance
3.1. Analyzing EMRC6 Encryption
EMRC6 is better than any other version of RC6 due to its increased complexity, security and throughput. The EMRC6 encryption is three times faster than RC6 and the throughput is high when compared to its predecessor MRC6. Table 2 shows the comparison between various parameters of EMRC6 and the parameters of other version of RC6.
![]()
Table 2. Comparisons of RC6 versions.
3.2. Security Issues
The diffusion per round in achieved by the use of multiplication which provides high security in lesser number of rounds. Because of sixteen rotations per round the complexity of the algorithm is increased which proportionally increases the security. It is robust against differential linear attack, statistical attack and chi-square attack due to its increased no of rotations per round [25] .
Figure 3 shows that the encryption time is increased with increase in the size of the data block. But when compared with the previous version of RC6 it has got better encryption time. Figure 4 shows the throughput
![]()
Figure 3. Consequence of encryption time over varied data size.
![]()
Figure 4. Consequence of number of rounds on throughput.
decreases with increased number of rounds which gives the conclusion that the security is high with more number of rounds since security and throughput are inversely proportional.
3.3. Correlation Coefficient
Correlation Coefficient is the value between pixels in the same place in the input image and watermarked image. Correlation Coefficient is used to measure the image quality between the pixels in the original image and watermarked cipher image at a particular location.
Coefficient Correlation 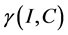 is found using Equation (3).The Expectation and variant value to be substituted in Equation (3) is found using Equation (4) and Equation (5).
is found using Equation (3).The Expectation and variant value to be substituted in Equation (3) is found using Equation (4) and Equation (5).
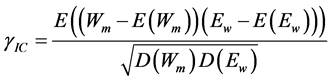 (3)
(3)
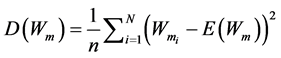 (4)
(4)
![]() (5)
(5)
where,
![]() &
& ![]() are Expectation of pixel from
are Expectation of pixel from ![]() and
and ![]()
![]() &
& ![]() are Variants of pixel from
are Variants of pixel from ![]() and
and![]() .
.
Table 3 shows the correlation coefficient of three sample images for the existing method and the proposed method which concludes that the correlation coefficient is low for the proposed method is low when compared with other encryption scheme.
3.4. Analysis of LSB Embedding Efficiency
The image quality of the output watermarked cipher image “We” is found using the PSNR and MSE calculation. Equation (6) depicts the PSNR calculation and Equation (7) calculates the MSE value.
![]() (6)
(6)
![]() (7)
(7)
where
m is the row values of the images.
n is the column values of the images.
x, y is the pixel values of the images.
The PSNR value from Table 4 predicts that the PSNR value of the sample images is high when compared with the previous method and hence the quality of the watermarked cipher image is of good quality for the proposed method. Table 5 includes the output of each level and the overall output, for the test images.
![]()
Table 3. Comparison of correlation coefficient.
![]()
Table 4. PSNR of the watermarked encrypted Image.
![]()
Table 5. Overall output for test data.
4. Conclusions
The combination of EMRC6 (Enhanced modified version of RC6) Scheme with LSB (Lest Significant bit) is a proper method for medical image authentication. The input image is converted into JPEG2000 image to make encryption and embedding scheme simple. EMRC6 provides high security since it withstands almost all attacks which was imposed on previous RC6 version. The security level of watermark is increased by this encryption and the watermark embedding capacity also improved. Even though LSB is a fragile watermark scheme, it is best suited for content authentication. But the watermark is encrypted to make the watermark robust. So that extraction of the watermark is difficult. The encryption speed of EMRC6 is high and the throughput is high when compared with its predecessor. The correlation coefficient is very low proving that the image quality is good. After embedding the PSNR value is high and MSE value is low when compared with other algorithm.
The upcoming work is to provide copyright production using a frequency domain algorithm and EMRC6 encryption scheme.