Trust Evaluation Based on Node’s Characteristics and Neighbouring Nodes’ Recommendations for WSN ()
1. Introduction
A WSN consists of large number of spatially distributed autonomous wireless sensor nodes to cooperatively monitor physical or environmental conditions, such as temperature, humidity, light intensity, sound, vibration, pressure, motion etc. The nodes are densely deployed in a hazardous/unattended environment with the capability of sensing, computing and communicating wirelessly to the base station (BS), via neighbouring benevolent nodes [1] -[4] . The traditional security systems proposed in [5] -[9] such as public-key cryptographic, authentication and other mechanisms cannot be applied directly because they are computation intensive and each sensor node in WSN, is limited in its memory, battery life, computation and communication capabilities. Also, WSNs are susceptible to many varieties of attacks [10] -[13] like node capture, eavesdropping, worm-hole, Sybil attack, sink-hole and denial of service etc. Due to these attacks, total breakdown of network may take place. Hence, cryptographic and authentication methods are not sufficient to detect the malicious and/or selfish nodes and to separate the appropriate nodes among many neighbouring nodes for secure message routing from source to destination. Therefore, a new way of security mechanism that consumes less resources of network and detects malicious nodes easily, is required. Trust, the degree of reliability [14] of other node in performing actions, i.e. in QoS characteristics is a new mechanism for secure packet routing. The trustworthiness of a node on any neighbouring node can be evaluated based on its previous transaction records.
In this paper, we extend our previous work presented for the calculation of trust, based on direct trust only as in [15] ; to a new approach of trust calculation considering both direct trust and indirect trust. The direct trust is evaluated based on node’s performance in QoS characteristics, i.e. in trust metrics such as data packets and control packets forward, data rate, power consumption, reliability, etc. is presented. Similarly, the indirect trust is evaluated based on the recommendations given by node's neighbouring nodes. The direct trust is combined with indirect trust using the traditional weighting approach to calculate total trust of a node. We have presented simulated results graphically, showing the trustworthiness and risk formed among the nodes for different trust thresholds and for different percentage of malicious nodes. Also, we have shown simulated results for the detection of malicious nodes and percentage of packet loss in the network. Rest of the paper is organized as follows: we present existing trust evaluation methods in section 2, the proposed TENCR: Trust Evaluation method for WSNs based on Node’s QoS Characteristics and neighbouring nodes Recommendations in section 3, while performance evaluation is included in section 4 and finally, section 5 concludes the paper.
2. Trust Models for Sensor Networks
There are many trust evaluation techniques available in the literature [14] -[18] for WSNs. In [14] Mohammad Momani defined the trust in different ways, as per him trust is the degree of reliability on other node/s in performing actions and can be formed by maintaining a record of the transactions with the nodes directly as well as indirectly. Trust can also be stated as a level of confidence that the assigned work can be done at a particular moment. This level of confidence can be extracted from the past history of transactions. Trust is dependent on time; it can increase or decrease with time based on the available evidence through direct interactions with the node or recommendations from other trusted neighbouring nodes. We need mathematical models to represent trust and reputation and update these continuously.
Trust management system for WSNs is a mechanism that can be used to support the decision-making processes of the network [13] . It aids the members of WSN to deal with uncertainty about the future actions of other participants. As WSNs are highly application oriented, these applications bring various security needs. Survival of a WSN is dependent on the cooperative and trusting nature of its nodes. Hence, the trust establishment between nodes is must. Overview of the existing trust evaluation techniques proposed in different trust management systems and trust based routing protocols are given below.
1) Mohammad Momani [14] introduced a computational model for trust in his doctoral thesis. He proposed different methods for modelling and managing trust to enable WSN to be secure and reducing the computing and communication overheads. He proposed one algorithm for trust calculation and risk assessment based on trust factors and dynamic aspects of trust. He modelled the direct trust computation with direct experiences, and indirect trust with recommendations given by the neighbours. He modelled total trust using traditional weighting approach for direct trust and indirect trust as shown in following equations. DT is direct trust (experience), IT is indirect trust (recommendations), T is total trust. The direct trust DT of A on B is given by the following equation.

The indirect trust IT of node A on node B is given by the following equation.

where 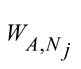 is weight for jth neighbouring node recommendation.
is weight for jth neighbouring node recommendation.
The total trust T is function of DT and IT, and is given by the following equation where WD and WI weights assigned to each.

2) A novel flexible trust management system proposed in [16] defined the trust as the ratio of successful transactions S to the total transactions made by the node. The proposed model is a decentralized trust scheme, i.e. the trust management functionality is distributed over the network nodes. In this model, each node is responsible for computing its own trust value per relation in the network, collecting direct and indirect information. The both direct and indirect trust values are used to evaluate each node’s trustworthiness. The proposed model has inherent reputation scheme of getting trustworthiness of any node, when direct evidences does not suffice, i.e. the number of direct evidences remain under threshold. Node A calculates trust value regarding node B based on the following equation:
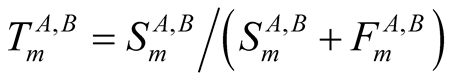
where S is successful and F is unsuccessful transactions.
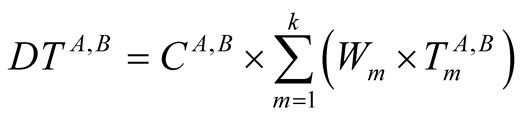
where 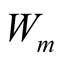 is weight of each trust metric.
is weight of each trust metric.
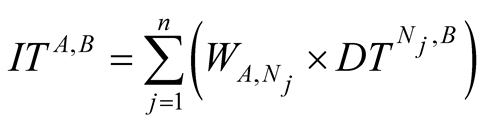
where 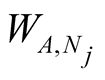 is weight for recommendation made by jth neighbour.
is weight for recommendation made by jth neighbour.

3) In trust management scheme “Securing Geographic Routing in WSN” proposed in [17] , honest nodes are favoured by giving them the credit for each successful packet forwarding, while penalizing suspicious nodes that exaggerate their contribution to routing. Initially, trust value 0.5 will be assigned to the node. Then, it monitors the behaviour of the nodes (one hop neighbouring nodes) to which it forwards packets.
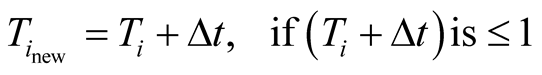
= 1 otherwise. ∆t, step size is 0.01.
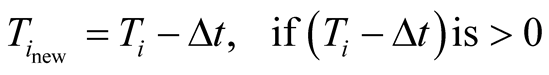
= 0 otherwise. ∆t is predefined penalty.
4) Trust establishment system “Defense of Trust Management Vulnerabilities in Distributed Networks” proposed in [11] has two ways to establish trust in computer networks. First, when the subject (first party) can be directly observing the agent (second party). Second, when the subject receives recommendations from other entities about the agent, indirect trust can be established.
Direct Trust DT = (S + 1)/(S + F + 2) where S, F are the number of successful and unsuccessful interactions respectively between the Subject and Agent. Initially DT = 0.5 because S = F = 0.
Indirect Trust IT = Recommended by others.
5) A trust model for WSN using fuzzy logic is proposed by Tae Kyung Kim, and Hee Suk Seo in [18] for centralized network. Reputation defined as a perception of a party, created through past actions about its intentions and norms. The different components in the suggested trust modelling are minimum trust, maximum trust and un-trust. The proposed model calculates the trust level of a sensor node, trustworthiness T, untrustworthiness U assuming that the wireless sensor network has the reputation value of each sensor node. In reputation components, minimum T, maximum T, minimum U and maximum U are defined between each pair of nodes. From this, trust T and un-trust U are acquired. Using the T and U, the trust evaluation level is acquired.
The trust evaluation between two nodes I and J is shown below, where Ti is trust of node I on node J and Tj is trust of node J on node I and U is the corresponding un-trust.
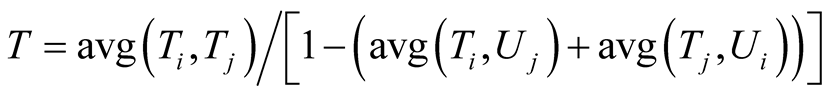 ,
, 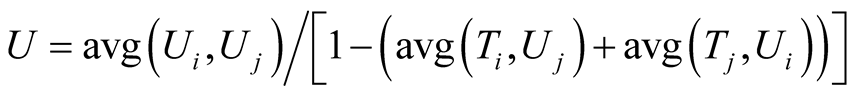
Trust evaluation between I and J = T/(T + U).
3. Proposed Technique for Trust Evaluation
In this section, we propose a new trust evaluation method TENCR for WSNs. By applying this technique, any node of WSN can evaluate how much trust it is having on its neighbouring nodes. Here, neighbouring nodes means, nodes those can be connected by node’s radio signal. The trust, which is the level of confidence, is a time dependent entity. That means the trust may vary as time goes on based on the nodes’ behaviour in transactions performed among them. The trust can be evaluated from the history of transactions with the node and from the recommendations given by the other neighbouring nodes. Here, the history means the behaviour of the node in different aspects, i.e. trust metrics, also called Quality of Service Characteristics [10] [16] . The level of confidence extracted from trust metrics is called direct trust (DT). The indirect trust (IT) can be extracted from the recommendations, called indirect information given by the neighbouring nodes. The overall Trust (T) on any node can be formed by manipulating these direct and indirect trusts. As shown in Figure 1, node A is evaluating trust on node B. It evaluates direct trust from its direct experiences and indirect trust from the information given by the neighbouring nodes.
Some of the useful trust metrics of WSNs are listed in Table1 Each of the nodes of WSN shall update the trust metrics of its neighbouring nodes for every event occurred in the network. The indirect trust (IT) on any neighbouring node can be calculated by gathering the information about that node from all other neighbours.
Every node in the network keeps an eye on the behaviour of their neighbouring nodes and maintains a record on them for every event happening in the network. This record contains the information about neighbouring node QoS characteristics. These trust metrics data will be helpful for calculating the direct trusts on them. Also, as and when requested by neighbouring nodes, trust of one node, can be transferred to other nodes, and there it helps in evaluating the indirect trust. In our trust evaluation method, trust of any node on its any neighbouring node is a function of DT and IT. The trust metrics [16] listed in Table 1, can defined as below:

Figure 1. Node A evaluating trust on node B.
Availability to hello messages: Detection of neighbouring nodes those are available in the radio range of any node, and to examine them for packet forwarding.
Packet forwarding: Detection of nodes that deny to forward packets, acting in malicious manner, each time a source node sends a packet to a neighbour for further forwarding, it enters the promiscuous mode and overhears the wireless medium to check whether the packet was actually forwarded by the selected neighbour.
Acknowledgements: Detecting the successful end-to-end forwarding of the messages, we suggest that each source node waits for a acknowledgement per transmitted message to check whether the message has successfully reached the Sink node.
Packet delay: Detection of the time delay taken by the packet to reach the Sink node successfully, and to find network congestion status from source-to-end.
Packet precision: Each time a source node transmits a packet for forwarding and then overhears the wireless medium to ensure that the packet was forwarded, it additionally processes it to check the packet’s integrity, i.e. that no unexpected modification has occurred.
Routing protocol execution: All the nodes may not having the routing function. Some nodes meant for only monitoring the environment, and some may be only for forwarding packet and some for both the functions.
Reputation: In the trust evaluation technique the node’s indirect information will be requested from the node’s neighbouring nodes. It will be helpful when there is no direct trust information regarding that node.
Remaining Energy: Although the energy level of each neighbour is not a pure trust metric, taking into account the remaining energy level, apart from extending the network lifetime, contributes towards load balancing (partially defending against the traffic analysis attack). In our novel routing protocol, the remaining energy value is piggy-backed in the Beacon message.
In our trust evaluation method, we are dividing trust metrics into two categories called higher priority category, and lower priority category. This is because, we do not want to compromise in some fundamental functional characteristics of a node. A node’s main functionality can be seen by its higher priority trust metric levels. Hence, node’s higher priority trust metrics shouldn’t fall below the threshold level. For example, the trust metrics Data packets forwarded, Control packets/Messages forwarded and Reputation values should not be less than the higher priority threshold because node’s functionality is hidden in these trust metrics. All other trust metrics can be considered as of lower priority category.
The direct trust on any neighbouring node can be evaluated from higher priority trust metrics and lower priority trust metrics. A node should maintain minimum trust threshold in the higher priority trust metrics hence, they are multiplied or geometric mean value will be taken. Similarly, all other trust metrics (of lower priority), are averaged or arithmetic mean value will be taken. To evaluate the direct trust, these two are combined by giving some weight to each one. Here, a node can become malicious/selfish/un-trusted at two different stages, one is, when any one of the higher priority trust metrics are falling below the threshold, and second, over all direct trust is falling down by direct trust threshold. The indirect trust on any node, actually depends on the neighbouring nodes recommendations on that node. The indirect trust (IT) on any neighbouring node can be evaluated by gathering the information about that node from all other neighbouring nodes. The neighbouring nodes are divided into two categories, most trusted neighbour and normal neighbour. Every node not only maintains the trust metric data but also, maintains their trusts history. Based on their history, some neighbouring nodes are most trustworthy and can be separated into most trusted/high reputation neighbours and some are into less trusted neighbours. The most trustworthy neighbouring node must recommend positively. Similarly, all other neighbouring nodes are of lower priority, and their recommendations will be averaged. To evaluate the indirect trust, these two are combined by giving some weight to each one. Here, a node can become malicious/selfish/un-trusted at two different stages, one is, when any one of the higher priority neighbouring node is not recommending, i.e., most trusted neighbouring node recommendation is falling below the threshold, and second, over all indirect trust is falling down by indirect trust threshold.
The overall trust or total trust T of any node on any neighbouring node is again a function of direct trust (DT) and indirect trust (IT). Our proposed model uses the traditional weighting approach for combining direct trust and indirect trust to form the total trust (T) per relation in the network.
3.1. Direct Trust (DT)
One of the most important aspects of trust management schemes is the process of data collection for trust calculation. The Direct Trust value of a neighbouring node can be determined by the different trust metrics of that particular node in different events occurred in the network. The trust metrics, i.e. the QoS characteristics that can be taken into account are given in [16] . The Direct Trust is a function of trust metrics. The listed trust metric data for different events are essential and can provide a useful feedback to the system, towards the proper decision making by the trust management system in the node. Here, depending on the application, we can insist the minimum level (threshold) to all the trust metrics, or we can have different thresholds to different groups of trust metrics. Once one/more trust metric threshold/s are fixed, our trust management system considers that no node is trusted unless it is having minimum threshold level in a given trust metric strictly. This is the main advantage of our proposed trust management model compared with other models. And, this is where our proposed Trust Evaluation model filters the malicious and selfish nodes in participating in the packet routing in WSN.
As already mentioned, all the trust metrics are divided into two categories called higher priority and lower priority trust metrics as shown in Figure 2. Let  be the set of different higher priority trust metrics on node A on node B for different trust metrics, where m = 1 to k. And Let
be the set of different higher priority trust metrics on node A on node B for different trust metrics, where m = 1 to k. And Let 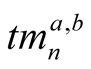 be the set of different lower priority trust metrics on node A on node B for different trust metrics, where n = 1 to l. Also, let
be the set of different lower priority trust metrics on node A on node B for different trust metrics, where n = 1 to l. Also, let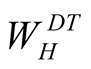 ,
,  are weights given to higher priority trust metrics and lower priority trust metrics respectively in finding the Direct Trust. Here,
are weights given to higher priority trust metrics and lower priority trust metrics respectively in finding the Direct Trust. Here, .
.
In our trust management system, the direct trust of any node on any other neighbouring node is weighted sum of the geometric mean of all higher priority trust metrics, provided every higher priority trust metric is greater than or equal to threshold, and arithmetic mean of all lower priority trust metrics. The set of trust metrics are called trust metric vector. Every node consists of set of metric vectors called trust metric matrix of its neighbours. From these records, Direct Trust (DT) of neighbouring node is calculated, and is shown below.

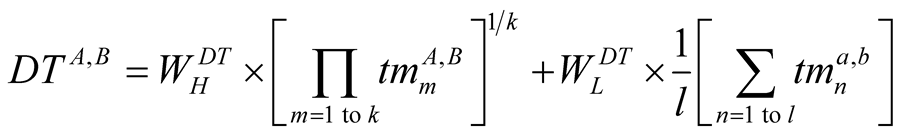 (1)
(1)
3.2. Indirect Trust (IT)
The indirect trust of any node on any neighbouring node can be evaluated from the indirect information given by the neighbouring nodes. Again, as in trust metrics, the neighbouring nodes also divided into most trusted and normal other neighbouring nodes. The geometric mean will be applied to the information given by the most trusted neighbouring nodes and arithmetic mean will be applied to the information given by the other normal neighbouring nodes. Let us assume for the calculation of IT the set of nodes (say 8) are situated in some nearby area in the WSN field as shown in Figure 3. Their names are A, B, C, D, E, F, G, H and I. Here, we are interested to find the IT of node A on the neighbouring node B, i.e. ITA, B. The node A, first collects the recommendations from their neighbouring nodes. In this case the nodes C, D, E, F, G, H and I are neighbours. Assume that

Table 1. Trust metrics

Figure 2. Different trust metrics levels.
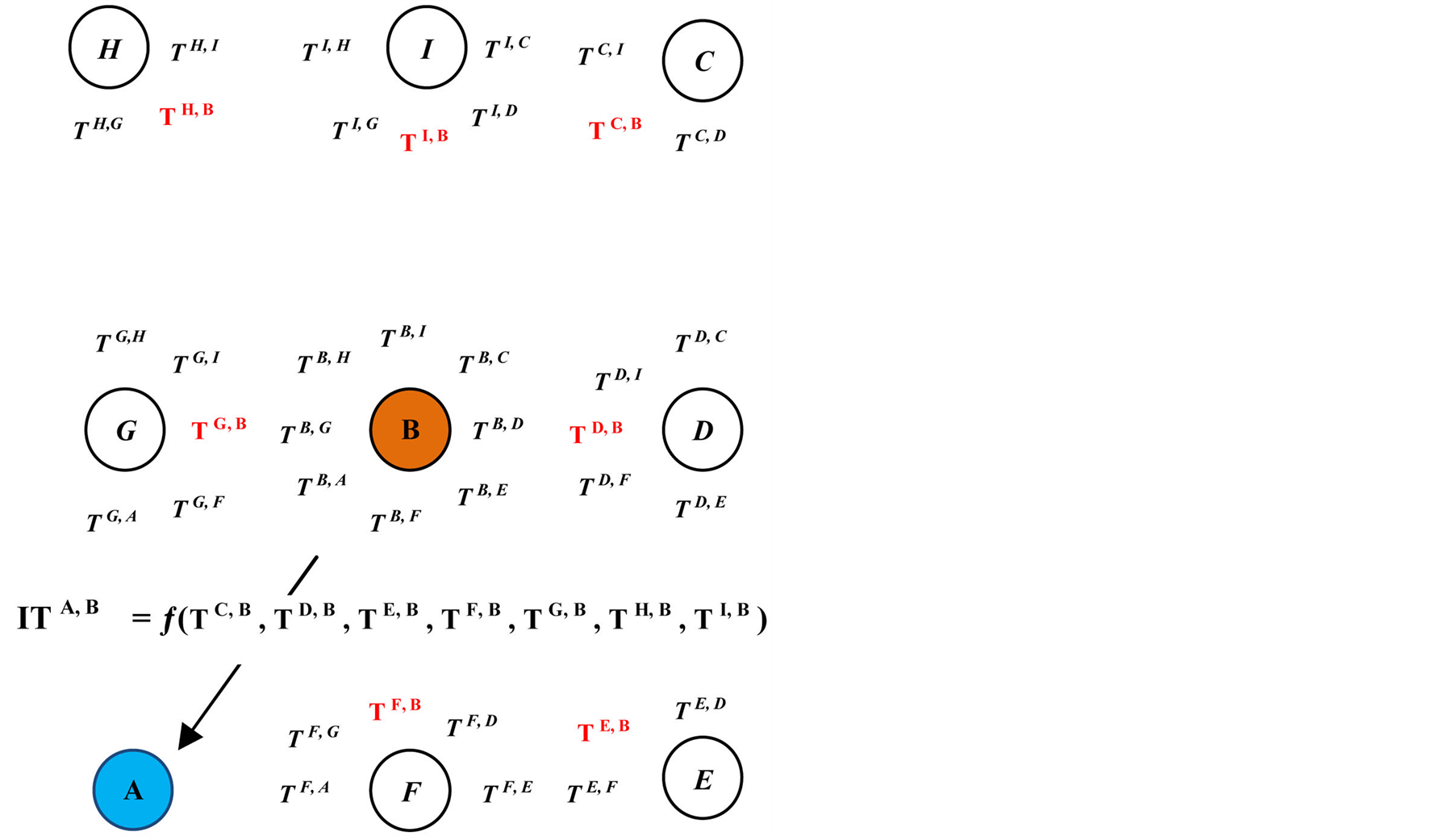
Figure 3. Indirect trust of node A on node B.
collected recommendations are TC,B, TD,B, TE,B, TF,B, TG,B, TH,B and TI,B respectively. Among the neighbouring nodes, let us say G and F are most trusted neighbours. The indirect trust is a function of indirect information given by most reputed nodes (higher priority node trusts) and ordinary neighbour nodes. Here, the geometric mean function is applied to most reputed category and arithmetic mean is applied to less reputed category with weights ,
, 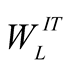 respectively. From Figure 3, the following three equations can be extracted.
respectively. From Figure 3, the following three equations can be extracted.
IT = Geometric mean of trusts given by higher priority neighbour nodes + Average of trusts given by lower priority neighbour nodes.
In general, the indirect trust IT of node A on node B is given by the following equation.
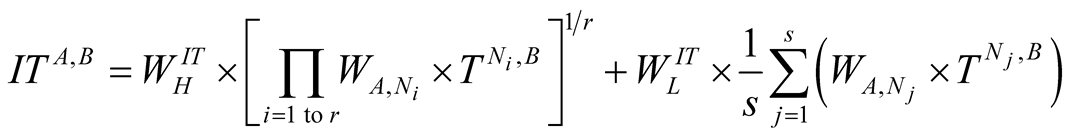 (2)
(2)
where,  is weight for recommendation made by ith neighbour.
is weight for recommendation made by ith neighbour.
Selection of higher priority neighbouring nodes:
As already explained, every node of WSN shall maintain the database for its every neighbouring node, related to the transactions occurring in the network. Among the neighbouring nodes, some nodes may be the most trusted neighbouring nodes. If any neighbouring node is maintaining its trust (T) more than or equal to the trust threshold level on average all the time or say for the last x events/transactions, then it can be the most trusted neighbour node. Table 2, shows the history of 8 neighbouring nodes of node A for last x events. It is the node’s responsibility to check its database, and selects few most trusted nodes if any. The indirect information given by such neighbouring nodes would be applied to the geometric mean function in the equation of indirect trust (IT). The indirect information given by all other neighbouring nodes would be applied to the average function in the calculation of IT.
3.3. The Trust (T)
The overall trust or total trust (T) of any node on any neighbouring node is again a weighted some of direct trust (DT) and indirect trust (IT). T = WD × DT + WI × IT.
The WD is a weight given to direct trust and WI to the indirect trust where WD + WI = 1. Weights can be assigned using different approaches. Sometimes DT may be given more weight, and IT may be given less weight i.e. WD > WI. Hence, we define a new equation for trusting one sensor node by the other in Wireless Sensor Networks as shown below.

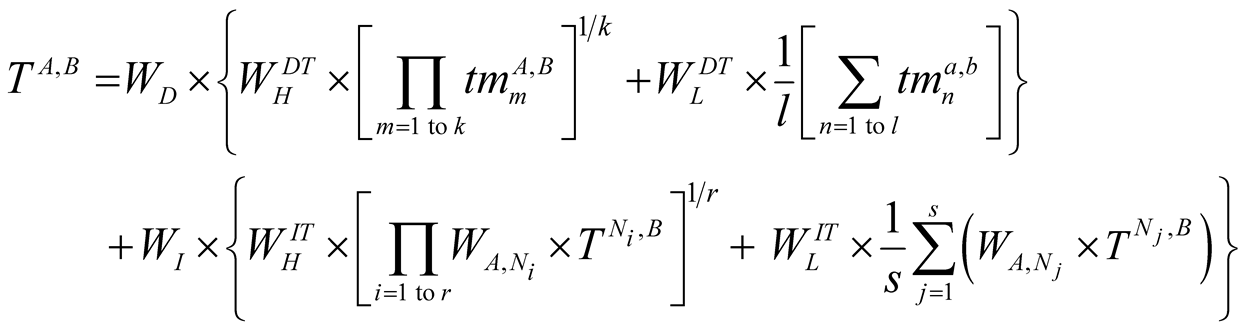 (3)
(3)
where, A is the node that is evaluating its trustworthiness on node Bk is higher priority trust metrics, l is lower priority trust metricsr is most trustworthy neighbours, s is ordinary neighbours,
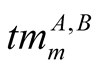 is
is 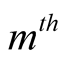 higher priority trust metric of node A on node B,
higher priority trust metric of node A on node B,
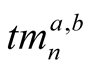 is
is  lower priority trust metric of node A on node B,
lower priority trust metric of node A on node B,
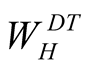 is higher priority trust metric weight,
is higher priority trust metric weight, 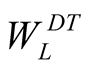 is lower priority trust metric weight.,
is lower priority trust metric weight.,
 is higher priority neighbour weight,
is higher priority neighbour weight, 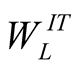 is lower priority neighbour weight,
is lower priority neighbour weight,
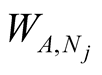 is weight for recommendation made by jth neighbour,
is weight for recommendation made by jth neighbour,
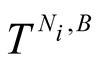 is trust given by neighbour Nj about node B, and
is trust given by neighbour Nj about node B, and
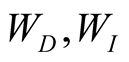 are weights of direct and indirect trusts respectively.
are weights of direct and indirect trusts respectively.
Figure 4, shows the relation among the direct trust, indirect trust and the trust graphically for WD = 0.75 and WI = 0.25 respectively. From Figure 4, we can also see the trustworthy area where trust quantity will be towards 1.0 and risky area where trust quantity will be towards 0.0.

Table 2. Node A’s neighbouring node trusts for different events.
3.4. Adaptive Trust Evaluation Algorithm
The proposed trust evaluation method is an adaptive trust evaluation method. First, it tries to find the trustworthy neighbouring node from the available trust metric database. If any node’s trust value greater than or equal to trust threshold then that neighbouring node will be selected for packet transmission for that moment. But, if no node found trustworthy then it adapts another way to find and evaluate the trustworthy node for packet routing. Node makes the transactions with neighbouring nodes and gets the indirect information from all neighbours those are situated in its radio range. Then it updates the database of the node, and evaluates the trusts and chooses the best node, if not better node with risk factor. If trustworthy node found as a result of first step, i.e. benevolent node from already available database then much energy of a node can be saved. When no trustworthy neighbour node found from its radio range, the node increases its radio communication range to find good neighbouring nodes through indirect information. This is an energy consumption process which is adaptive and occurs in risky situations. Hence, this evaluation method saves the energy of node as long as the trusts of neighbouring node is greater than or equal to trust threshold. This increases the life of the node as well as lifespan of the entire WSN.
When node wants to make the communication with its neighbouring nodes for indirect information data, it simply sends a request command to its neighbours. This command may take only one byte or two byte in size. But, when it is getting indirect information the size of the message from each neighbouring node may be approximately 20 to 25 bytes by assuming that each node’s information takes 2 bytes and it may have 10 neighbours. The communication among nodes for indirect information will take place only when there is risky situation and not all the time as explained in the following algorithm. Hence, this adaptive TENCR method is not only energy efficient but also decreases the communication overhead.

3.5. Advantages
This method provides many advantages as compared to the existing ones. First, it allows us to find out the Trust (T) levels of all neighbouring nodes, even when the trust threshold (Tth) cannot be decided or evaluated, and hence the separation of benevolent and malicious nodes is possible before selection of any neighbouring node for data/packet transmission. The second advantage is that this method allows us to give more weight to certain trust metrics, also to some neighbouring nodes, depending on the requirement of the application. The third and

Figure 4. Relation between direct trust, indirect trust and trust.
important advantage of this Trust Evaluation method is that the calculation of direct trust and indirect trust of any neighbouring node is not on the basis of the average of the trust metrics as in the case of other trust models. If it is on the basis of average function, then the neighbouring node can be trustworthy even if some major trust metrics of neighbouring node like, data packets forwarded, control packets forwarded are fallen down to 0 or less than the Tth, which should not be the case. This situation occurs when WSN is attacked by the Sybil node or malicious node. But, in our proposed trust evaluation model, a node is treated as faulty or malicious when one of the trust metrics is failed to form trustworthy relation. Hence, in this Trust Evaluation method, the malicious and/or selfish nodes can easily be detected and discarded from making transactions with the other nodes.
4. Performance Evaluation
To evaluate the performance of the proposed TENCR technique, we have taken some assumptions in the Sensor Network. The Sink node sends a test signal to the all nodes of the network periodically. The period of the test signal is not defined and it can be application dependent. This test signal will be received by all nodes and it may contain any information from Sink node to a node/group of nodes/all nodes. Also, the test signal may be an instruction or can be node/s behaviour information in a particular period/transaction. Based on the application, the WSNs functionality can be centralized or decentralized. In a decentralized model, the trust evaluation and management functionality is distributed over the network nodes. Each node is responsible for computing trust value per relation in the network, collecting events from direct relations, and collecting trust values from other nodes in the network. The trust formation, evaluation and updating can be centralized where trust will be computed by one single node (may be Sink) periodically and will be communicated to all network nodes. Our proposed trust evaluation technique, the trust computation will be at the Sink node because of the resource constraints at sensor node.
Also, we assume that there are two main functions of WSN, initialization phase or setup phase and the normal routing or run phase. The setup/initialization phase is primarily to detect the malicious nodes of the WSN if any using our proposed trust evaluation method and the run phase is a normal packet routing phase with the benevolent nodes after eliminating the detected malicious nodes.
Initialization phase is also called trial phase. In this phase, all nodes will be deployed and will be initialized. For this, the Sink node will be sending appropriate signal to nodes. To detect the status, working conditions and maliciousness if any of all network nodes, Sink node instructs all the nodes to send some dummy packets from every node to Sink. In turn, these dummy packets from all nodes will be collected at Sink node. The Sink node collects these dummy packets and analyze them to know the working conditions of all nodes. As Sink node will be containing the central database for all nodes as well as for neighbouring nodes with respect to every node, it finds the malicious nodes of the network. Finally, the Sink node detects the all malicious nodes in the network, and informs to all benevolent nodes. Then in the second phase, normal routing will be performed without considering the malicious nodes. But, the Sink node will be evaluating the trusts of all nodes periodically and it will inform malicious node information if any to all nodes.
The performance of the proposed trust evaluation technique has been evaluated through computer simulations. Using MATLAB, a new simulation package for routing has been developed based on distance of neighbouring nodes towards the Sink node. We have used our trust evaluation mechanism TENCR in this protocol. The other settings and assumptions are given below.
4.1. Trustworthy Relations for Randomly Taken Trust Metrics
4.1.1. Node Location Is Fixed Equally Spaced WSN in Square Area
Figure 5, shows trustworthy relations formed for randomly taken trust metric quantities. Here, WSN with 36 nodes deployed in square area as 6 × 6 nodes in X and Y directions. The radio range of the node here is assumed as it covers the one-hop nodes. That means one hop nodes (8 nodes) are neighbour nodes to any node. Here, our main aim is to find how the trustworthy relations are being formed among the nodes, depending on the trust threshold level. Both direct trust and indirect trust are considered for the calculation of total Trust. The number of trust metric categories are taken is 10, out of which 4 are taken as higher priority category and 6 are lower priority category. Similarly, every node is having 8 neighbour nodes, out of which 3 are most trusted neighbouring nodes and rest are ordinary neighbouring nodes. Finally, we have shown how the Trustworthy relations changed for different trust threshold levels graphically for four different cases.
4.1.2. Random Deployment and Fixed Location in a Square Area
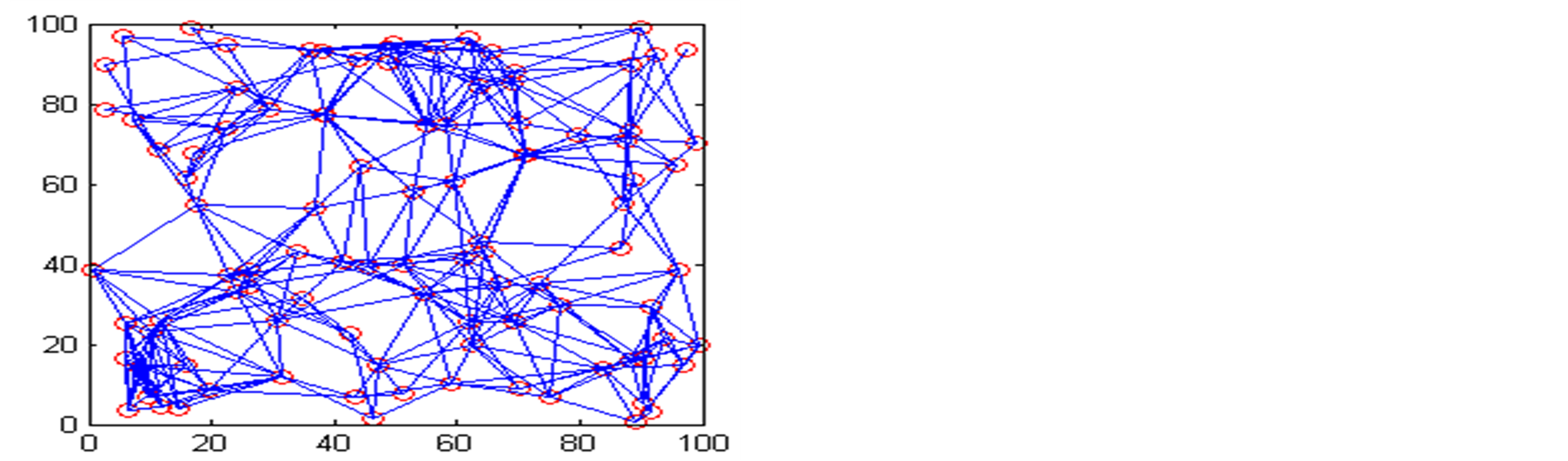
WSN with random deployment with fixed node location in a square area as shown in Figure 6. Here, our assumptions are, a WSN with 100 nodes deployed in square area of 100 × 100 meters randomly in X and Y directions. The radio range of the node assumed here is 15 meters. The number of trust metric categories are taken is 8, out of which 3 are taken as higher priority category and 5 are lower priority category. The neighbour nodes of any node are dependent on the locations. Because locations are random, they vary node to node. Here, we are assumed 2 are most trusted neighbouring nodes and rest are ordinary neighbouring nodes. The other assumptions are same as the manual deployment WSN. Table 3, shows the detection of malicious nodes in two different trust evaluation systems with some randomly taken trust metric data and neighboring node recommendations. For cases 2 and 4, as shown in Table 3, though the higher priority trust metrics are below the threshold level,
 (a)
(a)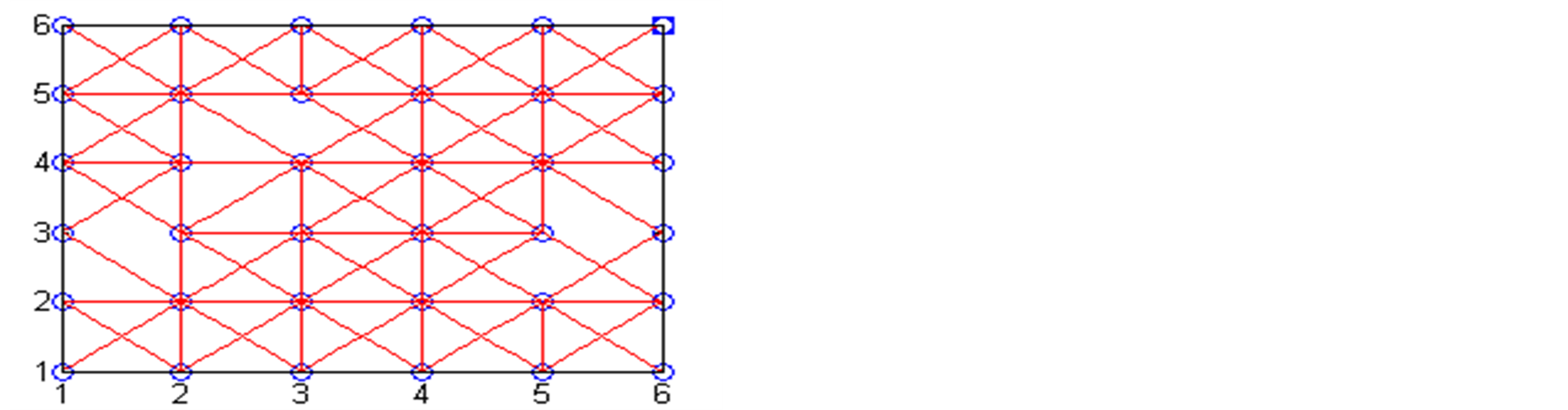 (b)
(b)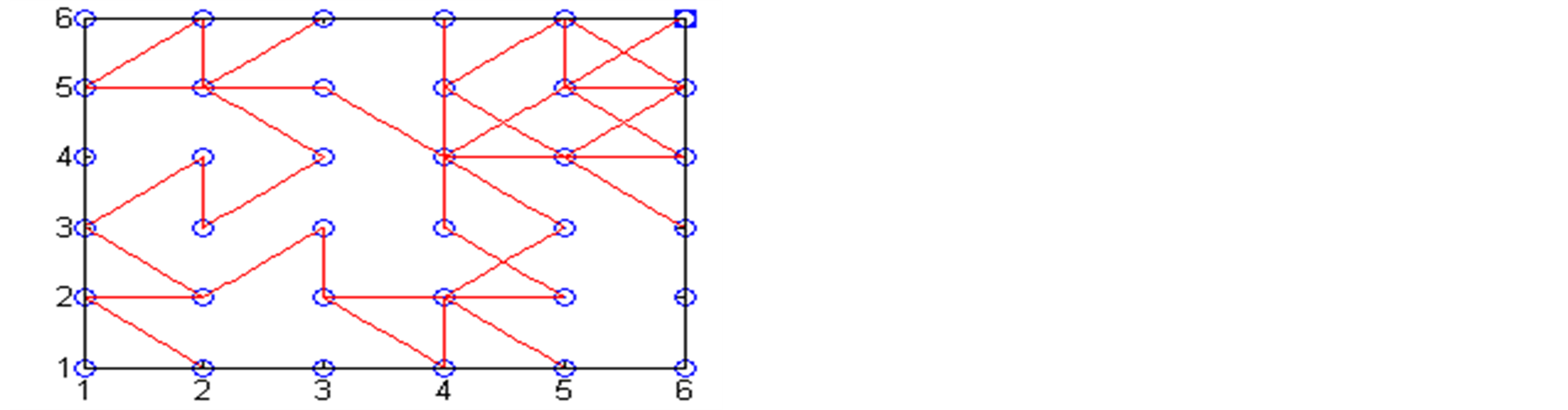 (c)
(c)
Figure 5. Trustworthy relations among the nodes. (a) Trusted relations for trust threshold ≥ 0.35; (b) Trusted relations for trust threshold ≥ 0.4; (c) Trusted relations for trust threshold ≥ 0.45.
 (a)
(a)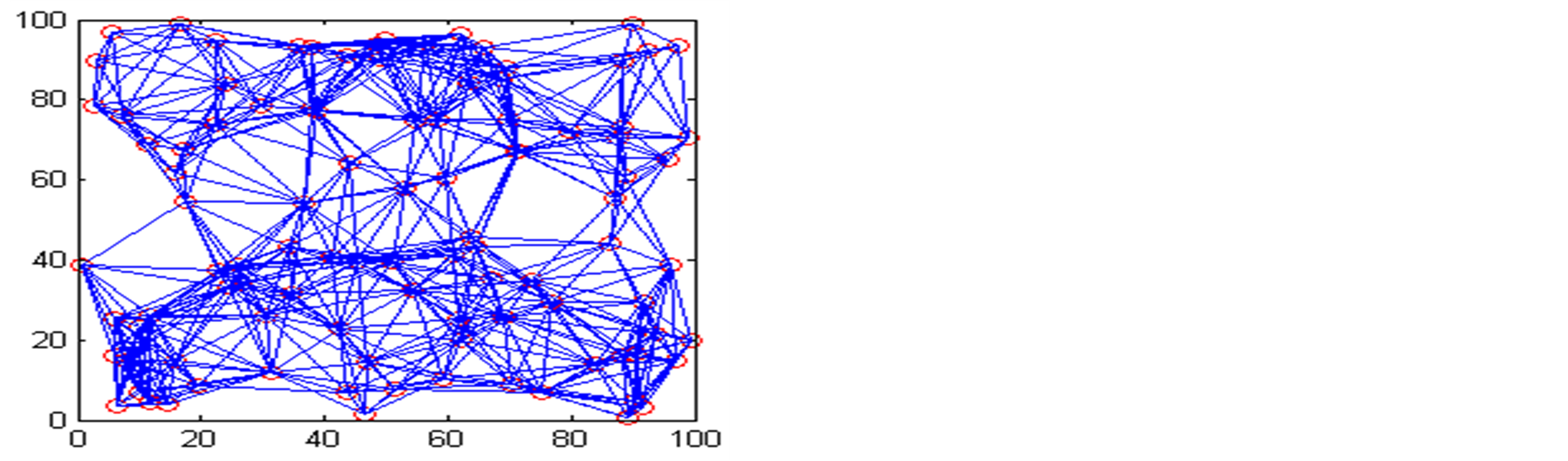 (b)
(b)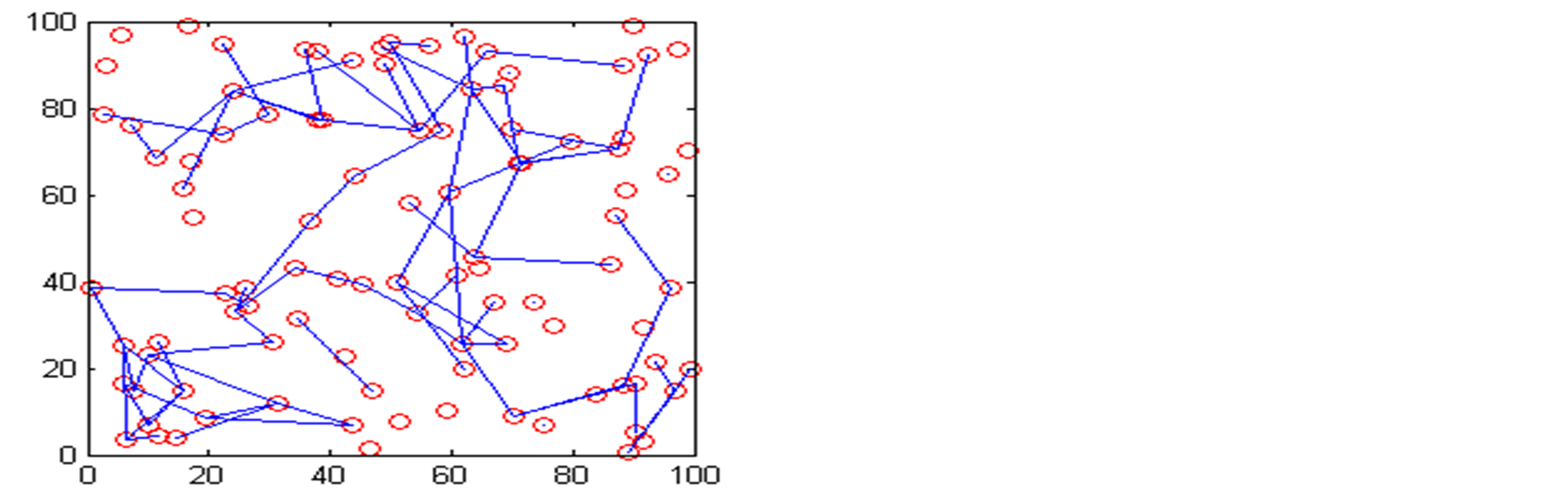 (c)
(c)
Figure 6. Trustworthy relations among the nodes for random deployment. (a) Trusted relations for trust threshold ≥ 0.25; (b) Trusted relations for trust threshold ≥ 0.30; (c) Trusted relations for trust threshold ≥ 0.35.

Table 3. Detection of malicious nodes by TENCR for Tth = 0.35.
the arithmetic/average based trust evaluation systems cannot detect the malicious nodes, whereas the TENCR detects these malicious nodes. Similarly, the most trusted neighboring node recommendations also, cannot be recognized in the arithmetic mean based trust evaluation systems.
4.2. Detection of Malicious Nodes in Setup Phase for Different Weights
During the setup/initialization phase, the malicious nodes can be caught by our trust evaluation method running in the Sink node. The performance of the proposed trust evaluation technique for different settings and assumptions of the network has been evaluated and shown graphically. For this, a new multi-hop routing package has been developed in which the next neighbouring node will be selected for handing over the packet based on distance of neighbouring nodes towards the Sink node. We have evaluated the performance of our trust evaluation mechanism TENCR with this multi-hop routing protocol. The other settings and assumptions are given below.
WSN deployment: Random in a square area Mobility of nodes: Immobile WSN area: 200 × 200 square meter Sink location: top right corner No. of nodes: 150 Node Radio Range: 30 meter Trust metrics: 8 categories Neighbouring nodes: max. 10% of total nodes Initial Trust: 0.5 (initially all nodes are trusted)
Malicious nodes: 0% to 30% (red color marked)
Trust threshold (Tth): 0.48 to 0.5 Direct Trust weight: varies from 0.75 to 0.5Indirect Trust weight: varies from 0.5 to 0.75 Packet generation : randomly with Poisson probability of 0.3
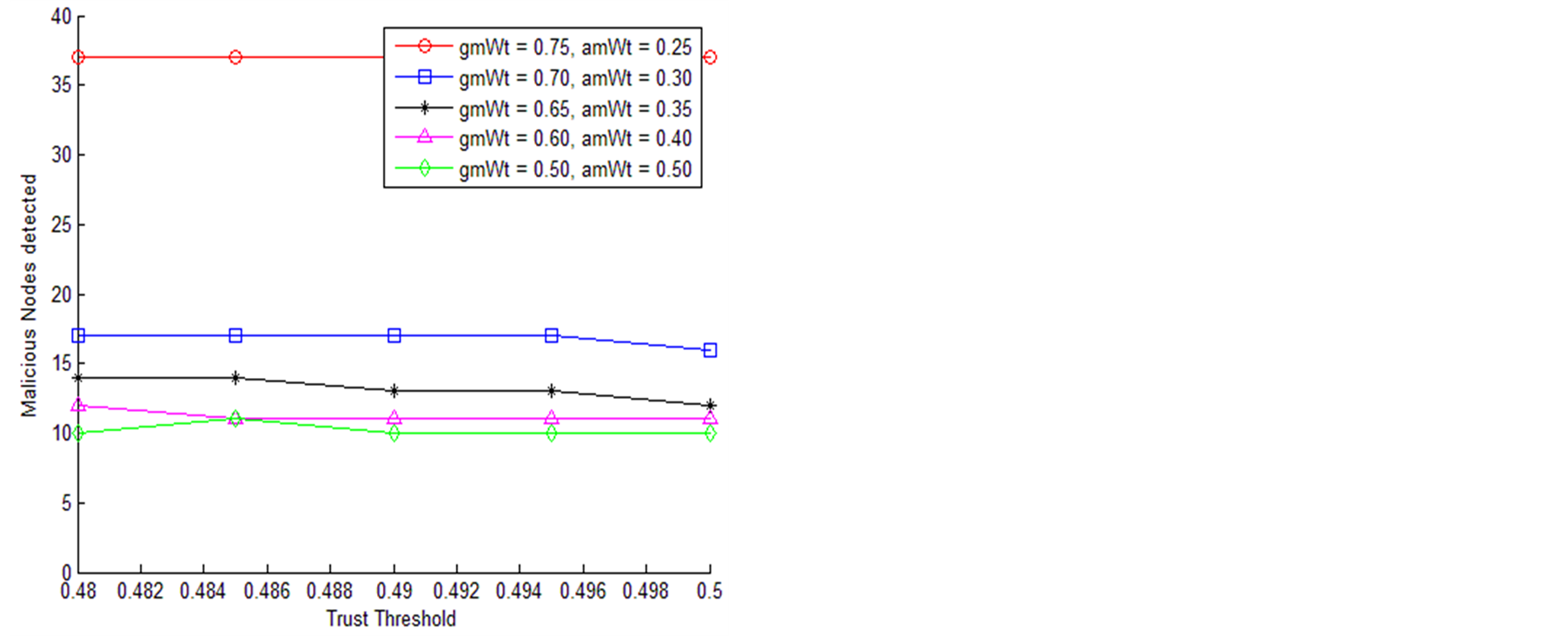
Figure 7(a) and Figure 7(b) shows, the graphical view of WSN for random deployment, and packet routing from nodes to Sink for 30% of malicious nodes and 15% of malicious nodes respectively. This pictorial view contains total 150 nodes, out of which black colored are benevolent nodes and red colored are malicious nodes. Figure 8, shows, the percentage of packet loss in the network versus percentage of malicious nodes. The packet loss values in Figure 8, are the average of ten values taken for different deployments. Figures 9(a) and Figure 9(b) shows, malicious node detection by TENCR in a network for 20% and 30% of malicious nodes respectively for different weights given to direct trust (geometric mean) and indirect trust (arithmetic mean). We can observe the increment in percentage of malicious nodes detection as weight to the geometric mean increases from 0.5 to 0.75; Hence, the application of geometric mean instead of arithmetic mean in the calculation of direct and indirect trust evaluation, captures the malicious nodes efficiently in WSNs.
4.3. Calculation of Direct and Indirect Trusts, and Identification of Trustworthy Node
We have implemented our trust evaluation technique practically, using nesC programming language and TinyOS which is very suitable operating system for wireless sensor network nodes. We have used four nodes, iris motes whose IDs are 0, 1, 2 and 3. Every node in this case will be having three neighbouring nodes and can supply indirect information of one neighbouring node to rest two neighbouring nodes vice versa.
Every node evaluates direct trust on all neighbours from trust metrics those are evolved with direct interactions and stored in its database. Before calculating the trust, it brings the indirect information from neighbours, then it evaluates the trust. Figure 10, shows snapshot of a manual calculation of direct trust, indirect trust and the total trust by all four nodes on their neighbouring nodes. Here, we have assumed only two trust metrics and their initial values are shown in brown colored columns and manually calculated direct, indirect and total trust are also shown in Figure 10.
 (a)
(a) (b)
(b)
Figure 7. WSN random deployment without and with malicious nodes. (a) WSN with 30% malicious nodes; (b) WSN with 15% malicious nodes.
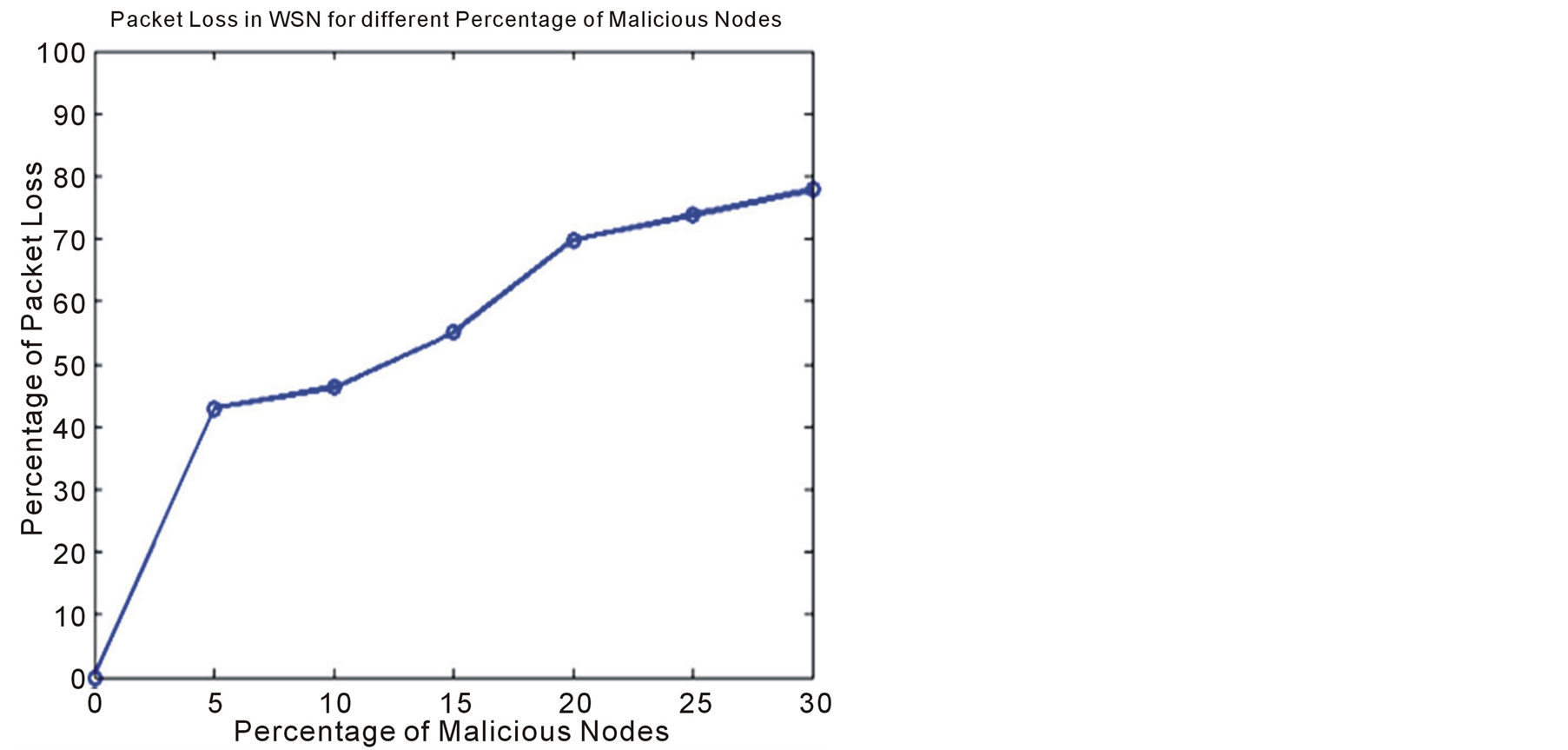
Figure 8. Packet loss by malicious nodes.
 (a)
(a) (b)
(b)
Figure 9. Detection of malicious nodes for (a) 20% and (b) 30% of malicious nodes.
Figure 11, shows the practical implementation results experimented with iris motes. Every node is displaying the node ID whose trust is large among their neighbours. Node is having three LEDs, yellow, green and red (LSB).
5. Conclusion
The TENCR trust evaluation method presented in this paper detects the malicious and/or selfish nodes in the network if any, and provides the trustworthiness among the node and its neighbours based on the trust metrics evolved by previous transactions in the network and the recommendations provided by the neighbouring nodes. The direct trust is formed by trust metrics (QoS characteristics) and indirect trust is formed by neighbour nodes recommendations. In this paper, we argue that few basic and fundamental functional QoS characteristics can be categorized as higher priority and few (others) are lower priority, and the categorization of trust metrics is the application specific. Once the classification of the trust metrics, most trusted neighbour nodes, and their threshold levels are fixed by the application, our proposed model see that they are maintained at the node in finding the trust on any neighbour node. We have shown graphically as well as in tabular form how malicious/selfish node can be captured by TENCR Trust evaluation method for different cases. We have also shown in algorithm

Figure 10. Manual calculation of direct, indirect and total trusts of every neighbours.

Figure 11. Implementation results for identifying trustworthy neighbouring node.
form, the behaviour of node when no trustworthy node found in its vicinity, i.e. adaption of energy consuming operation by increasing its radio range to find trusted node by interacting with the neighbours. In future, we want to concentrate on designing the trust management system for WSN by considering the dynamic change in a) node’s location; b) neighbouring nodes; c) issues related to revocation of nodes, and also trust evaluation and malicious node detection at node level. We also have a plan to develop an algorithm for energy efficient dynamic routing protocol, which elects an indispensable node for routing based on node trust, energy level and the distance towards the sink.