An IP Format Based Algorithm for ZigBee Routing Protocol Optimization ()
Received 30 March 2016; accepted 22 May 2016; published 25 May 2016

1. Introduction
Recent years, WSN (Wireless Sensor Networks) is widely used in all walks of life owing to the development of wireless technology and the embedded intelligent control system [1] . With the escalation of basic communication technology, wireless sensor network technology is developing rapidly towards the direction of low cost, low power, small size, versatility and high-density deployment to meet the increasingly demand [2] . However, a large-scale and high-density WSN will surely produce a large amount of raw data and cause the multi-hop data transmission phenomenon. Generally, due to the battery-powered WSN nodes and the changeable and complex environment, WSN has defects of unbalanced network energy consumption, dynamic changes of networks topology and low network reliability [3] [4] etc. By learning the traditional practice of network IP-address format and the cluster heads in WSN [5] [6] , we proposed an optimized algorithm for ZigBee routing protocol based on a new IP-format short address.
The structure of this paper is as follows. In section 1, we address the research background and the problem issue. In Section 2, we briefly describe the standard ZigBee protocol and analyze its shortcomings. In Section 3, a model of IP-format address and a more flexible routing decision in WSN are carried out. In Section 4, several simulation results are given. Finally, this paper is concluded in Section 5.
2. Analysis of Standard ZigBee Protocol
Generally, ZigBee network transfers data in a bidirectional way. Its network layer supports three topologies: star, tree and mesh. Traditionally, ZigBee network combines two routing algorithms: Cluster-Tree based algorithm and AODV-based routing algorithm. As for cluster tree algorithm [7] [8] , the main idea is that the nodes are pre-assigned static addresses according to the given formula, thus forming the parent-child relationship, as is shown in Figure 1. Nodes do not need to maintain router information, and destination can be found according to the static network addresses. To achieve this purpose, three network parameters must be pre-defined: the maximum number of child nodes Cm, the maximum depth of network Lm, and the maximum number of routers Rm. Afterward, the address space of node in depth d, i.e. Cskip(d), satisfies Equation (1). Assuming that the address of a parent in depth d is Afather, then its k-th sub-ZR’s Addresses is assigned to the Equation (2) and its n-th sub-ZED’s address is assigned to the Equation (3). If D is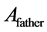 ’s child, then they satisfy formula (4), but not vise versa.
’s child, then they satisfy formula (4), but not vise versa.
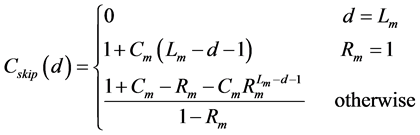 (1)
(1)
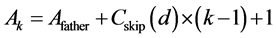 (2)
(2)
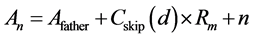 (3)
(3)
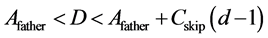 (4)
(4)
Despite the fact that the standard ZigBee protocol, to a certain extent, can avoid defects separately caused by an AODVjr or a Cluster-Tree [9] [10] , but it still has some deficiency. First, the routing decision is inflexible. In Figure 1, node 1 needs to send data to node 43. The most likely path to be found is 1-0-43. But the standard
![]()
Figure 1. ZigBee network with static addresses.
ZigBee protocol will start the AODVjr route-discovery process, which is unnecessary as the path can be easily calculated by the cluster-tree algorithm without consuming energy to broadcast RREQ packets. Second, the AODVjr’s router-discovery process has redundant packets. If node 23 sends data to node 38, node 22 and node 24 will also broadcast RREQ packet, which is redundant in most cases.
3. Related Work
In the Internet, terminals can easily transmit data to each other via IP addresses. Learning from this practice, we set up a new address and format it according to IP’s segment format. Define the depth of node i as CLi. Assuming that Lm = 4, the new address’s default value is [ff.ff.ff.ff.shortAddr]. The coordinator’s address is [0.0.0.0.0]. Nodes distributed in depth 1 are assigned addresses like [Cskip (1).ff.ff.ff.shortAddr] and CLequals 1; nodes distributed in depth 2 are assigned addresses like [Cskip (1).Cskip (2).ff.ff.shortAddr] and CLequals 2, and so on. Figure 2 shows how the network looks like with brand new addresses.
The relationship between nodes can be obtained by analyzing their new addresses. Taking node 38 and node 2 as an example: 38’s address is [21.5.ff.ff.38], we can see that 38 is in the second layer and the step size to its sibling’s address is 5; Node 2’s address is [21.5.ff.ff.2], so it’s also in the second layer. However, because (|38-2|) %5 doesn’t equal 0, so these two nodes do not belong to the same sub-branch, i.e. they are not siblings. If we use the cluster-tree algorithm to transmit data, there are at least 4 hops. The AODVjr will only take one hop if both nodes are routers and can communicate with each other directly. So that we can analysis the positional relationship between source and destination in advance, especially for hops.
Based on the new address, the improved algorithm is described as follows.
Assuming S sends data to D:
• Step 1: If S is ZED, the data are transmitted directly to its parent. Otherwise, skip to step 2.
• Step 2: If S is a router and has a valid path to D, then transmits data directly. Otherwise, skip to step 3.
• Step 3: If S and D are in a parent-child relationship (That’s to say, hop equals 1), then transmit data directly. If the hop between S and D equals 2, set RREQ’s TTL to 1 and wait for ALLOWED_HELLO_LOSS * HELLO_INTERVAL (AHLHI for short) milliseconds. If S do not receive RREP, then transmits data using the Cluster-Tree algorithm, otherwise establish a new communication link based on the content of the RREP to transmit data. Otherwise, skip to step 4.
• Step 4: Start an improved AODVjr router-discovery sub-process to find a path to transmit data.
Flowchart for proposed methodology is depicted in Figure 3 (C stands for the current node).
In order to balance network’s power consumption, the improved algorithm optimized the direction and the flooding scope of RREQ packets. First, we can acquire the relationship between S and D by pre-analyzing their addresses, and we can set RREQ’S TTL to an appropriate value. Second, we optimize redundant RREQ packets: if the destination is a child of the current node, then the current node’s parents should discard RREQ; else if the destination is a parent of the current node, then the current node’s children discard RREQ. Last, during the route discovery process, nodes in relatively high energy level have priority to the route. Improved AODVjr router discovery process is shown in Figure 4.
![]()
Figure 3. (a) The contour of improved algorithm; (b) the improved zbr_forward method.
![]()
Figure 4. Flowchart of improved AODVjr router discovery sub-process.
4. Simulation
In order to effectively evaluate the improved algorithm, this paper carried out several simulations based on NS2 platform. Simulation parameters are shown in Table 1.
Data’s format is CBR (Constant Bit Rate); the packet size is set to 80 Bytes; sending interval is 0.2 seconds. Experimental results of this analysis are shown as follows.
4.1. Jitter
Delay jitter is the assessment of the network’s stability at a certain frequency. Network’s traffic rate is 250 Kbps, transmission interval is 0.2 seconds. Simulation curves are shown in Figure 5.
As is shown above, the upper and lower limits of two algorithms’ network delay jitter are basically bet- ween±0.05 s, which means that network has high stability. The comparison also shows that the improved algorithm’s delay jitter spikes are significantly reduced, indicating that network latency is relatively stable and network stability has also improved to some extent.
4.2. Network Residual Energy Percentage
Figure 6 shows that network with the improved algorithm has a higher level of residual energy: First, the improved algorithm pre-analyzed relationship between source and destination, making routing-decision more flexible. Second, the improved algorithm optimized the direction and flooding scope of RREQ packets, thus reducing packet redundancy. Last, during the routing discovery process, nodes in relatively high energy level have priority to route, making energy consumption more balanced.
4.3. Network Routing Overhead
Figure 7 shows that the improved algorithm optimized the direction and flood scope of RREQ packets and dropped useless RREQs, reducing the routing overhead to some extent.
![]()
Table 1. Simulation scenario parameters.
![]()
Figure 6. Network residual energy percentage.
4.4. Network Throughput
Figure 8 shows that the improved algorithm’s network throughput is relatively lower than the standard algorithm. The reason is that each network packet needs to add a 4-byte prefix representing the depth of the node and a 1-byte node relationship flag, thus causing a decrease in the proportion of valid data. However, the decline of network throughput is slightly, and the new network throughput still remains at a relatively high level; So that, taking its good performance in delay jitter, network residual energy and routing overhead into account, the algorithm’s performance has been greatly improved on the whole.
5. Conclusions
The Internet assigns a unique IP address to each host in all sub-networks and divides the IP address into 4 segments. This format makes IP address contain much information about the network’s topology. Learning from this practice, this paper creatively combined the nodes’ short address and their cluster head into a new address and divided the new address’s field according to IP format. Based on the new address, this paper optimized routing decisions by pre-analyzing the relationship between source and destination and enhanced the control of RREQs’ direction and flooding scope. The simulation shows the new algorithm’s superiority over the standard algorithm in network’s delay jitter, overhead and residual energy.
Our work will provide a research direction for node localization in the large-scale network as well as attracting researchers to draw more attention to existing effective techniques in the cable network. In the future, we will focus on solving the decrease in the proportion of valid data and reduce throughput the by using compressed sensing technology.
Acknowledgements
The Specialized Research Fund for the Doctoral Program of Higher Education has supported this work-project (No. 20130031110032). Furthermore, the authors gratefully appreciate the Tianjin Key Technology Program of the Ministry of Science and Technology (No. 14ZCZDNC00014).