Empirical Investigation of Threats to Loyalty Programs by Using Models Inspired by the Gordon-Loeb Formulation of Security Investment ()
Received 26 December 2015; accepted 14 March 2016; published 17 March 2016

1. Introduction
Loyalty programs (LPs) are structured marketing efforts that reward, and therefore encourage, customers’ loyalty [1] . LPs have proliferated in recent years as companies seek to acquire and retain customers, increase customer spending, and encourage the purchase of additional products [2] . However, some studies such as [3] argued that since most firms now utilize LPs, they are no longer effective in contributing to competitive advantage. Consequently, many firms are attempting to redesign LPs to enhance their effectiveness. In particular, in order to increase customers’ loyalty, point exchange or redemption services have matured worldwide. For example, Points.com1 is a major point exchange or redemption service in the U.S. In Japan, point exchange network is expanding, which enables customers to redeem points from one LP to another LP [4] . However, these services attract not only customers but also attackers whose aim is to obtain monetary benefits. In fact, there are an increasing number of LP incidents worldwide, as shown in Section 2.
When we consider security investment to reduce the damages caused by such incidents, we need to assess the features of LP network from the viewpoint of the efficacy of security investment. In order to answer to the above question, Jenjarrussakul and Matsuura [5] conducted an empirical study of LPs. Their study was performed inspired by the Gordon-Loeb model [6] - [8] of security investment; they considered damage, expense (or security investment), threat, and vulnerability as four fundamental factors when they developed their empirical analysis model. In particular, they provided security-liquidity implications by using the liquidity of an LP as a metric of threat. This analysis is possible because threat (defined as the probability of a threat occurring) and vulnerability (defined as the conditional probability that a threat once realized would be successful) are handled separately.
However, the definition of the liquidity itself is not deeply studied. The possibility of using other metrics is not well considered, either. In this paper, we investigate this threat metric more deeply by considering different metrics based on an observation of actual security incidents on LP systems.
Our work to be reported in the rest of this paper is inspired by this primary study [5] , but there are important differences as follows. First, the liquidity definition is reconsidered, and a more intuitively convincing one is introduced. Second, we observe actual security incidents more deeply and give more implications that help LP operators to manage partnerships; the implications are consistent with recent changes in the LP network. Minor changes over the proxies used to test hypotheses also help our empirical study.
The rest of this paper is organized as follows. In Section 2, we see major incidents on LPs, which occurred worldwide, and their characteristics. In Section 3, we describe related and previous works. In Section 4, the data used in our empirical analyses are shown. In Sections 5, 6 and 7, different threat metrics and liquidity definition are investigated. Lastly, Section 8 concludes the paper.
2. Incidents on Loyalty Programs
In the U.K., compromised credentials enabled the theft of users’ miles from the British Airways loyalty program in March 2015 [9] . In the U.S., Hilton Hotel rewards points were stolen in November 2014 [10] . This case happened because the login process was weak. Hackers can not only sell the stolen accounts or redeem the points but can also buy expensive items at Hilton shopping mall. About 10,000 accounts of American Airlines and United Airlines loyalty programs were compromised in December 2014 [11] . A March 2015 report [12] says “with Starbucks, hackers were somehow (still unclear) able to obtain customer usernames and passwords that opened up access to payment methods, which were used to refill gift card balances and transfer out gift card funds. Hackers can then sell these gift card balances to other people.” In these cases, hackers are said to have used ID-password lists for mimicking successful authentications.
There is an increasing number of LP security incidents in Japan as well [13] . Table 1 shows a list of major security incidents of LPs in Japan collected from web news articles that describe some characteristics of the attackers’ behaviors: they often 1) attempt to go through the web login authentication mechanisms, 2) make malicious attempts in one or two days, and 3) attempt to steal the compromised accounts’ points and redeem them into certain LP points. Regarding the third characteristic, it should be noted that Amazon Gift Card and iTunes Gift Code are often chosen as the redemption destinations by attackers. Their codes can be sold and eventually converted into real money. This is the first possible reason why attackers often choose those gifts. The second possible reason is that most attackers live outside Japan. Both Amazon and iTunes services are provided
![]()
Table 1. Major LP security incidents in Japan.
internationally with their head offices outside Japan, so attackers can avoid investigations by Japanese police. As the third possible reason, it should be noted that Amazon and iTunes are not willing to publish the redemption algorithms; without their disclosure, we cannot trace and find who stole the points.
3. Related Works
3.1. Loyalty Programs
Effectiveness of LPs is well investigated in the management area [3] . Also, some research focuses on Japanese LPs. For example, the research has been conducted on the characteristics of Japanese LP network [38] , the factor which leads LP partnership [39] , LP network’s economic reliability [40] and the network’s impact on marketing performances [4] . These works do not consider LP security problems.
LP security issues were first economically researched by Jenjarrussakul and Matsuura in 2014 [5] . They show two implications: the impact of LP security incidents gets lower if stronger security requirements in web authentication process are satisfied, and it is higher if the liquidity of the LP points gets higher. Our work is inspired by this primary study, but there are some important differences as mentioned in Section 1.
3.2. Virtual Currency and Security
European Central Bank defined virtual currency as “a type of unregulated, digital money, which is issued and usually controlled by its developers, and used and accepted among the members of a specific virtual community” and pointed out that LP points or miles can satisfy the definition [41] . Other representative virtual currencies include cryptocurrency and game currency. Regarding cryptocurrency, Bitcoin is the main research target [42] - [45] . Although these works handle security problems, they do not consider the relation between Bitcoin and LP systems. Massively multiplayer online games (MMOGs) currencies are also virtual currencies with security issues that have been researched without considering the relationship between the currencies and LP systems [46] - [50] .
4. Data Collection
We retrieved the LP network structure from Poitan.net, a portal site of Japanese LP networks where users can search possible routes of point redemption, find the market value of each LP point, and so on (see Appendix A.1). Each LP operator’s capital size was retrieved from each LP operator’s website. The data of the security investment, damage amount and security requirements are the same as those in [5] . Table 2 summarizes the data used in our study.
5. Point Liquidity and Number of Partners
5.1. Hypothesis Development
Reference [5] shows an important implication: an LP with higher liquidity suffers a bigger impact from incidents. However, the definition of the liquidity in [5] was not intuitively convincing as described in Appendix C.
It may be more convincing if liquidity is defined more simply as:
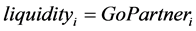 (1)
(1)
where 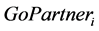 is the number of partners into which one can redeem points from LPi. In order to examine this definition, we set the following hypothesis:
is the number of partners into which one can redeem points from LPi. In order to examine this definition, we set the following hypothesis:
H1. An LP with more outgoing partners suffers greater damage.
5.2. Model
In order to test H1, the following linear regression model is set:
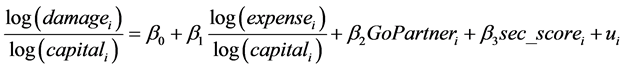 (2)
(2)
where i is an index that indicates each LP, 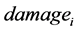 is the annual damage amount of the overall IT security
is the annual damage amount of the overall IT security
incidents of LPi’s operator, 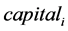 is the capital size of LPi’s operator,
is the capital size of LPi’s operator, 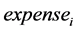 is the annual IT security expense of LPi’s operator,
is the annual IT security expense of LPi’s operator,  is the security requirement level of the LPi’s authentications, and
is the security requirement level of the LPi’s authentications, and 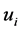 is the model’s error term, assumed to be independent of the observed covariates. For more calculation details of these proxies, see Appendix B.3. Correlations between variables are shown in Table 3.
is the model’s error term, assumed to be independent of the observed covariates. For more calculation details of these proxies, see Appendix B.3. Correlations between variables are shown in Table 3.
5.3. Results
To test H1, let the null hypothesis be 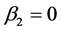 in Equation (2). H1 is accepted if this null hypothesis is rejected.
in Equation (2). H1 is accepted if this null hypothesis is rejected.
The estimated result of Equation (2) is shown in Table 4. The coefficient of 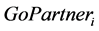 is significantly positive, so the null hypothesis
is significantly positive, so the null hypothesis  is rejected, and H1 is accepted. Additionally, the coefficient of
is rejected, and H1 is accepted. Additionally, the coefficient of 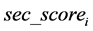 is significantly negative. This result is consistent with the results of [5] .
is significantly negative. This result is consistent with the results of [5] .
6. Does Time Required for Redemption Affect the Damage?
6.1. Hypothesis Development
A redemption request is not always approved quickly; it may take one week or longer. If the LP operators have more time to give approval, they may notice suspicious redemption applications and reject them with higher chances. Thus attackers may prefer quicker redemption to avoid the risk of being detected. In fact, the incidents surveyed in Section 2 suggest this preference. So let us consider the following hypothesis.
H2. If an LP has more outgoing partners with short redemption time, the damage from incidents is bigger.
6.2. Data and Descriptive Statistics
Figure 1 shows the histogram of the time required for redemptions of all the exchange routes of 274 LPs and Table 5 shows the descriptive statistics. Table 6 shows the descriptive statistics regarding the 82 selected LPs.
6.3. Model
To test H2, we set the linear regression model as follows:
 (3)
(3)
![]()
Table 3. Correlations between the variables in Equation (2). To save space, the following notation is used: ldam is log(damagei), lcap is log(capitali), lex is log(expensei), GoPartner is GoPartneri, and SecScore is sec_scorei.
![]()
Table 4. Results of the linear regression by Equation (2). The notations are the same as in Table 3.
**Indicates significance at 5% level. ***Indicates significance at 1% level.
![]()
Figure 1. Histogram of the time required for redemption in December 2014.
![]()
Table 5. Descriptive statistics of the time reqiured for redemption.
![]()
Table 6. Descriptive statistics of the number of outgoing partners regarding the 82 selected LPs. GoNrepresents the number of partners into which one can redeem points from each LP within N days.
where ![]() is the number of partners into which one can redeem points from LPi within N days and the other variables are the same as those in Equation (2). Correlations between variables are shown in Table7.
is the number of partners into which one can redeem points from LPi within N days and the other variables are the same as those in Equation (2). Correlations between variables are shown in Table7.
6.4. Results and Discussion
The estimated results of Equation (3) for ![]() are shown in Table 8. When N is 0 or 5,
are shown in Table 8. When N is 0 or 5, ![]() is significantly positive, but
is significantly positive, but ![]() does not show any significances. This means that if an LP suffers greater damage if it has more point-redeeming partners over the time threshold, 0 or 5 days. On the other hand, when N is 45 or 60,
does not show any significances. This means that if an LP suffers greater damage if it has more point-redeeming partners over the time threshold, 0 or 5 days. On the other hand, when N is 45 or 60, ![]() shows no significance but
shows no significance but ![]() is significantly positive. This suggests that a LP suffers more damage when it has a larger number of point-redeeming partners under the time threshold, 45 or 60 days. When N is 10 or 30, no significances were provided.
is significantly positive. This suggests that a LP suffers more damage when it has a larger number of point-redeeming partners under the time threshold, 45 or 60 days. When N is 10 or 30, no significances were provided.
These results suggest that the number of outgoing partners that require at least 45 days for redemption does not affect the liquidity. Although it is not supported if the threshold time is 5 days, H2 is supported if the threshold time is 45 days. It is shown that the damage gets bigger if the LP has more partnerships with shorter redemption times. Thus we find that redemption time has some effects on liquidity, and hence, on the threats to LPs.
7. Do Specific Partners Affect the Damage?
7.1. Hypothesis Development
Table 9 and Figure 2 show the number of LPs (out of the 82 selected LPs) from which one can redeem points
![]()
![]()
Table 8. Results of the regression by Equation (3) for N = 0, 5, 10, 30, 45, 60. The notations are the same as in Table 7.
*Indicates significance at 10% level. **Indicates significance at 5% level. ***Indicates significance at 1% level.
![]()
Table 9. Number of LPs (out of the 82 selected LPs) from which one can redeem points into Amazon and iTunes for N = 0, 5, 10, 30, 45, 60, 90.
into Amazon Gift Cards and iTunes Gift Codes with respect to the time required for redemption. As we mentioned in Section 2, attackers seem to prefer Amazon Gift Cards and iTunes Gift Codes for malicious redemptions. Taking alliances with specific partners might expose an LP to bigger threats. So we set the following hypothesis.
H3. An LP that takes partnership with Amazon or iTunes suffers greater damage.
![]()
Figure 2. Number of LPs (of the 82 selected LPs) from which one can redeem into Amazon Gift Card or iTunes Gift Code within N days.
7.2. Model
To test H3, we set the linear regression model as follows:
![]() (4)
(4)
when![]() , and
, and
![]() (5)
(5)
when![]() , where
, where ![]() is the binary value representing whether one can redeem points from LPi to an Amazon Gift Card or iTunes Gift Code within
is the binary value representing whether one can redeem points from LPi to an Amazon Gift Card or iTunes Gift Code within ![]() days (1 if possible, 0 otherwise), and the other variables are the same as in Equation (2).
days (1 if possible, 0 otherwise), and the other variables are the same as in Equation (2).
Correlations between the variables in Equation (4) and Equation (5) are shown in Table 10.
7.3. Results and Discussion
The estimated results for ![]() are shown in Table 11.
are shown in Table 11.
When![]() ,
, ![]() is significantly weakly positive at 10% level. When N is 10 or 45,
is significantly weakly positive at 10% level. When N is 10 or 45, ![]() does not show any significance. This means that H3 is weakly supported for the redemption time, 10, 45 and 90 days. Additionally, it suggests that availability of redemption into Amazon or iTunes does not affect the damage if one has to wait more than 45 days to complete the transaction. When N = 30 or N = 60, the p-values of
does not show any significance. This means that H3 is weakly supported for the redemption time, 10, 45 and 90 days. Additionally, it suggests that availability of redemption into Amazon or iTunes does not affect the damage if one has to wait more than 45 days to complete the transaction. When N = 30 or N = 60, the p-values of ![]() are rather small, although it is insufficient for the 10%-level weak support. On the other hand, when N = 0 or N = 5,
are rather small, although it is insufficient for the 10%-level weak support. On the other hand, when N = 0 or N = 5, ![]() is significantly positive and
is significantly positive and ![]() is insignificant. This means if an LP has an outgoing partnership with Amazon or iTunes and the redemption takes more than 0 or 5 days, it suffers more damage, while we cannot see any relation between the damage and the availability of 0 or 5-day redemption. While it differs from the intuition, the same discussion as in Section 6.4 can be applied.
is insignificant. This means if an LP has an outgoing partnership with Amazon or iTunes and the redemption takes more than 0 or 5 days, it suffers more damage, while we cannot see any relation between the damage and the availability of 0 or 5-day redemption. While it differs from the intuition, the same discussion as in Section 6.4 can be applied.
In Japan, some of the LP operators who experienced damages by malicious redemption into Amazon Gift Cards or iTunes Gift Codes introduced countermeasures; they either temporarily stopped their alliance with Amazon and iTunes or introduced phone authentication regarding the redemption into. This recent trend is supported by the above result of our empirical analysis.
8. Concluding Remarks
In this paper, we revisit the empirical models used in a former study [5] regarding the security of loyalty
![]()
![]()
Table 11. Results of the linear regression by Equations (4) and (5) for N = 0, 5, 10, 30, 45, 60, 90. The notations are the same as in Table 10.
*Indicates significance at 10% level. **Indicates significance at 5% level. ***Indicates significance at 1% level.
programs. In the models, the choice of variables is inspired by the Gordon-Loeb formulation of security investment: damage, investment, vulnerability, and threat. The liquidity of LP points corresponds to the threat in the formulation and plays an important role in the empirical study because it captures a particular feature of LP networks. However, the actual proxy used in the former study is artificial due to the fact that its original definition is not LP-wise but industry-wise. In this paper, we reconsidered the liquidity definition based on a further observation of LP security incidents. By using newly defined proxies corresponding to the threat as well as other refined proxies, we conducted hypothesis testing to derive more implications. We show the damage from LP incidents grows if partnerships with short redemption times or with Amazon or iTunes are accepted. These implications will help LP operators manage partnerships. In fact, these findings are consistent with recent trends in the LP network. Thus we can see the impacts of security investment models include a wider range of empirical studies in the economics of information security.
Acknowledgements
We thank the editors and the referees for their helpful comments. This work was partly supported by JSPS KAKENHI Grant Number 25280045 and 25240017. The authors express sincere appreciation to Mr. Takahito Kikuchi, the owner of Poitan.net, who provided the data and useful information for this study.
Appendix A. Poitan.net
Poitan (http://poitan.net) provides information on more than 200 LPs in Japan, such as estimated real-currency values of LP points, exchange/conversion rates between different LPs and how long the conversion would take. Suppose that a consumer would like to convert a certain amount of ANA (All Nippon Airways, a star alliance member) miles, say, 20,000 miles, into JAL (Japan Airlines, a one-world alliance member) miles. In response to this query, Poitan shows some possible conversion routes. For example, on December 25, 2015, Poitan said there were 87 possible routes. One of the possible routes with the best rate was as follows:
1) Convert 20,000 ANA miles (estimated value is 30,000 JPY (Japanese Yen)) into 20,000 JQ Card Points2 points (estimated value is 20,000 JPY). This would take about 60 days.
2) Convert 20,000 JQ Card points into 20,000 Epos Card Points3 (estimated value is 20,000 JPY). This would take about 3 days.
3) Convert 20,000 Epos Card Points into 10,000 JAL miles (estimated value is 15,000 JPY). This would take about 60 days.
Appendix B. Data and Proxies for Empirical Analyses
B.1. 82 Selected LPs
Table A1 shows the 82 selected LPs. LP ID indicates the LP’s ID of Poitan.net. You can access the information of an LP via http://dir.poitan.net/(.*).html, where (.*) is its ID number.
B.2. Industry
Table A2 shows the nine industries which operate LPs in Japan.
B.3. Calculations of the Proxies
Our empirical studies were conducted based on the Gordon-Loeb security investment model [6] , which considers the following four parameters as fundamental parameters: expense―the amount of security investment, damage―the amount of damage when the attack occurred, threat―the probability that an attack occurs, and vulnerability―the conditional probability that a threat once realized would be successful. When we consider the security of LP systems, one possible interpretation of the four parameters is as follows: Expense is the expense on IT security countermeasures by the LP-operating company; Damage is the amount of damage from IT incidents; Threat is considered to be high if the LP points’ liquidity is high because higher liquidity implies more chances of achieving criminal benefits by malicious conversion of LP points or their redemption and it can be a main attractive factor; Vulnerability is considered to be lower if the online user authentication system of an LP is implemented in a more secure manner.
This appendix shows how we set and calculate each proxy based on this interpretation, other than threat.
B.3.1. Damage
As is shown in Table A3, METI’s numerical data of IT damage represent only the ranges because of its questionnaire design [52] . So we calculated the average damage size for every industry and every capital size level by using the middle value of the range (e.g. 0.75 million JPY for the range “0.5 million to 1 million”) with an exception at the edge (i.e. we use 200 million JPY for the range “over 100 million.” This method is also used by METI [51] .
Then, from each LP’s industry and capital size, we calculate its damage. We set this damage size as ![]() where
where ![]() indicates each respective LP. For example, if LP1’s industry is “Information Service” and its capital size is “under 50 million JPY”,
indicates each respective LP. For example, if LP1’s industry is “Information Service” and its capital size is “under 50 million JPY”, ![]() .
.
This proxy calculation differs from [5] in the following three points. 1) Reference [5] ignored firms which answered “did not suffer information security incidents,” but we consider them as zero because it is more accurate. 2) In [5] , they calculated the average damage considering only the industrial categorization, but we also considered the capital size for segmentation. 3) Reference [5] used ![]() as the proxy
as the proxy
![]()
![]()
![]()
Table A1. List of the 82 Selected LPs (Part 1). LP ID indicates registered ID at Poitan, Industry ID indicates each industry (details are in Appendix B.2), and Capital size is each LP operator’s capital size. Security score shows a security requirement level calculated by the methods described at Appendix B.3.3. N/A means that we cannot access the corresponding information.
![]()
Table A2. Nine industries which operate LPs in Japan. Each industry ID is the same as in [5] .
of damage, where ![]() indicates LPi’s belonging industry ID,
indicates LPi’s belonging industry ID, ![]() is the average damage amount of its industry and
is the average damage amount of its industry and ![]() indicates the LP’s ranking score at Poitan.net. However, this might be somewhat artificial.
indicates the LP’s ranking score at Poitan.net. However, this might be somewhat artificial.
B.3.2. Expense
The proxy of expense is also calculated from METI’s data by the same method used for the damage. Then, ![]() is set.
is set.
B.3.3. Vulnerability
The metric of vulnerability is the same as [5] used. We used six requirements in the registration process, the authentication (login) process, and the back-up authentication process of each LP. Table A4 shows these six requirements. They computed the security score, ![]() , of LPi as the ratio of “the number of satisfied requirements in LPi” to “the number of requirements about which we can obtain data regarding LPi.”
, of LPi as the ratio of “the number of satisfied requirements in LPi” to “the number of requirements about which we can obtain data regarding LPi.”
![]() represents how unsuccessful an attack is, so we can view
represents how unsuccessful an attack is, so we can view ![]() as a metric for anti- vulnerability.
as a metric for anti- vulnerability.
![]()
Table A3. Examples of METI’s data about the IT damage amount [51].
![]()
Table A4.Security requirements in web authentications used for the calculationof sec_score [5] .
B.3.4. Normalization
Reference [5] did not normalize any parameters, but we normalize damage and expense with capital size as follows:
damage:![]() ,
,
expense:![]() .
.
Each LP-operating company has a lot of IT systems, and an LP system is just one of them. Since the empirical data of expense and damage is for all the IT systems of the company, some normalization would be necessary when we measure the expense and expense on its LP system.
Appendix C. Liquidity Definition at the Previous Research
We briefly describe how Jenjarrussakul and Matsuura [5] defined liquidity and used this metric.
Before they conducted quantitative analysis, they first considered the LPs security issues by industry. They listed 204domestic LPs and classified them into 9 industries. They drew a graph of the Japanese LP partnership network where each node indicates an industry. Since they were interest in how each industry node is connected, they checked the edge types―one-directional, opposite one-directional, or bidirectional―between industries and the average number of connecting LPs of all the LPs belonging to each industry.
In order to quantitatively examine which industry is more willing to connect with other industries via LP, they introduced a metric liquidity as a multiplier of the number of edge types, x, and the average number of partners regarding the LPs in a node, y:
![]() .
.
Then, using METI’s data, they discussed the relation between liquidity and damage or security investment in the industry-wise level.
After this industry based discussion, they entered upon a LP divided discussion and carried on quantitative empirical analysis with the same liquidity definition above. However, this definition does not seem suitable and intuitively convincing when we consider how easily attackers convert the points into actual monetary profit when we consider the LP-wise situation divided from the industry-wise cluster.
NOTES
![]()
1https://www.points.com/.
![]()
2JQ Card Point is a reward program of a credit card provided by a Japanese railway company.
3Epos Card Point is a reward program of a credit card provided by one of the biggest department store in Japan, Marui.