Received 20 October 2015; accepted 29 November 2015; published 2 December 2015


1. Introduction
IoT is typically composed of smart objects that are equipped by sensors and RFID systems [1] such that the connectivity requirements between the IoT smart objects are achieved over advanced communication standards like Wifi, Wimax, LTE, and cloud computing [2] [3] . More precisely, the IoT sensor nodes are provided with one or more integrated sensors with limited computing, memory and power capabilities. They have also the ability to communicate in a short-range distance [4] . On another hand, each RFID includes a reader to uniquely identify tagged objects or people [5] . After their deployment, IoT devices are expected to be intelligent by handling, transmitting, and reasoning about the occurred event. Consequently, the event manager is a core element of the IoT architecture that may successfully integrate a publish/subscribe middleware system which is a software that coordinates the communication between heterogeneous devices [1] [6] . Multiple protocols have emerged to address the routing problem in IoT. Most of them extend IPV6 [7] and rely on IEEE 802.15.4 [8] standard that is suitable for tiny sensor networks allowing their radio components to alter between the active and idle state according the medium’s conditions. The literature on routing protocols for IoT systems depicts that a large number of protocols implement clustering techniques to route efficiently data across the IoT devices. A more frequently issue in IoT concerns events’ routing that should be delivered at real-time to accomplish the requirements of some applications. We mention that event-based routing protocols have already been applied to distributed systems. The idea of event-based routing is to allow a set of devices to specify interests in certain event conditions. If an event has been trigged, the subscribers are interested to that event will be notified. The taxonomy of event-based routing protocols includes content and context based routing [9] . Our idea in this paper is to assume an IoT system that is provided by a publish/subscribe middleware and to propose a protocol for routing events in such environment. Our protocol is simple and uses the concept of content-based routing which is carried in a distributed manner via two simple rules. The fundamental characteristic of energy-efficiency of our protocol has been achieved through the construction of a virtual topology [10] that balances the energy load between IoT devices due to the self-organization property of the obtained hierarchy. This paper is organized as follows: Section 2 presents basic concepts behind IoT. Section 3 surveys IoT routing protocols. Section 4 presents potential event-based routing protocols that are addressed in distributed systems. Section 5 is concerned with the assumptions of EECBR. It details also the steps that are required for constructing the virtual topology and the rules that are used for distributed content-based routing. Then, Section 6 illustrates our simulation results. Finally, Section 7 concludes the paper.
2. IoT Concepts
IoT has been attracting much interest of researchers in the last few years. This is so as it enables a set of things/objects to be:
・ Pervasive: IoT devices are able to interact with the environment by sensing, and reasoning about data that have been produced. They may be connected through wired or wireless networks to exchange information and interact with the environment for taking the best decision at real-time.
・ Identified via a unique address. This desirable characteristic is obtained by IPV6 which grants an expanded addressing space.
・ Cooperative with other things by granting them an access to the local information to create new applications or services [11] .
In this sense, IoT creates a worldwide network of interconnected objects that should be uniquely addressable. Computers, smartphones, vehicles, homes appliances, cameras are examples of such things/objects. Moreover, IoT interconnects generic objects [1] . For example, smart refrigerators trace and report the availability and expiry dates of food items. They also rely on IoT network to place an order to grocery shops once a certain limit of the supply of food items is reached [12] . The integration of many technologies is the power behind IoT. Some of these technologies help to acquire and process contextual information while others improve security and privacy. Namely, sensor networks and RFID technologies play a major role for IoT systems. More specifically, RFID includes a tag that is equipped with an antenna for object identification. A sensor network based on RFID provides not only the possibility to identify objects but also to track their behavior or measure some parameters that are related to the environment [1] [5] . In addition, cloud computing is also exploited in some IoT systems to create contents and applications for the users. Cloud computing is an emerging model that has been used by industrial professionals and academics to provide a set of services over a public or a private cloud. Such services may refer to a hardware, a software or a system. A cloud computing model may contain a collection of physical data centers and virtualized computers to handle data and computation in a distributed and parallel manner. The idea of virtualization was introduced to provide high-speed computation by dividing a single job into many tasks that may be executed by the virtual machines. Moreover, cloud computing services may be categorized into: Saas, Paas, and Laas. The first service concerns web-based access and storage; while, the second one allows the developers to host web applications. Finally, Saas is a set of applications that are accessible from various client devices [13] [14] . The motivation behind integrating IoT and cloud computing is to enhance an IoT environment by taking benefit from the storage and processing capacities of cloud computing. This helps a lot to avoid sensors’ constraints. The cloud computing may also benefit from IoT by providing services to smart objects [15] [16] .
IoT applications are numerous. Broadly speaking, IoT would be adopted in [1] [5] [12] :
・ Transportation: where advanced cars, trains, roads, and trails would be equipped by sensors and tags and communicate with traffic control sites.
・ Smart homes and offices: in this case IoT enables controlling the room heating to our preferences. It can also be used to change the room lightning according to the time and day.
・ Cities: the control of a parking and the monitoring of material conditions in buildings and bridges are two examples of IoT exciting applications.
・ Environment: the sensors that are integrated to the things may help hugely to detect combustion gases, fire conditions, and soil moisture.
・ Healthcare: IoT supports healthcare applications by sensing medical data of the patients and allowing a remote diagnosis. It makes also the life of elder and disabled people easier. IoT may also be needed for controlling medical fridges.
・ Energy: the monitoring and management of energy consumption is a practical application of IoT that yields to an intelligent grid which is based on renewable energy resources. It reacts to power fluctuations to execute efficiently the requests and the actions of the end users and devices [11] .
A simplified architecture of IoT has two main layers consisting of two sub-layers each. The perception layer includes all technologies that allow perceiving and collecting data. The network layer takes care of transporting data in a transparent manner using the suitable communication standards including Wifi, Wimax, GPRS, and WSN. Rather than using the data management sub-layer of the service layer which treats complex and uncertain data structures, the application service sub-layer handles transforming data into content and providing an interface to user applications [5] . The data management sub-layer is also called the middleware layer and it re- presents the most critical layer of the architecture.
IoT has a profound effect on standardisation efforts because it is intended to support many diverse applications, protocols, and technologies as mentioned above. Three European bodies namely CEN, CENELEC, and ETSI are playing a vital role in developing IoT standards but the final objective of standardisation is not achieved yet. The standardisation is a bottleneck in the area of IoT for the reason that it requires a formal specification for testing any standard before providing it. We note that the test specification is resource consuming. In fact, the standardisation bodies are focusing on elaborating an interoperable protocol stack that expands HTTP, TCP, IP stack [17] to integrate sensor data within RFID and support new application in collaboration with some working groups of experts. The working groups are responsible for creating large documents, technical specifications and technical reports for any proposed standard.
3. IoT Routing Protocols
Routing is a topic that has attracting the research community in last years and intense works have been devoted to this field. Traditional routing protocols for Ad hoc networks may fall into three categories: reactive, proactive, and hybrid protocols [18] [19] . The first category establishes a route on demand; while, the second one maintains the topology and updates the routing tables periodically. The hybrid protocols perform both reactive and proactive routing to reduce the delay. Later, new protocols for sensor networks have been proposed. Two features are handled in such protocols: data exchange is performed hop by hop and the lifetime of the network is maximized [20] . Routing in IoT systems is highly related to routing in Ad hoc and sensor networks. Energy consumption of sensors, mobility of things, and the type of the IoT’s middleware are three primary concerns that may affect routing in IoT. 6LoWPAN (IP6 over power personal area networks) [21] is a major routing protocol for IoT systems. It has been defined by the Engineering Task Force (IETF) to route data through the Internet among non IP sensors. It relies on IEEE 802.15.4 [8] that is suitable for low power sensors. The network topology of 6LoWPAN includes a set of reduced function sensors that are connected to full function sensors. Moreover, a gateway is placed between two different network domains. By another hand, the network stack of 6LoWPAN is composed of seven layers: the IEEE 802.15.4 physical and Mac layers, the adaptation layer, IPV6 [22] , the transport, and the application layers. More specifically, the physical layer of IEEE 802.15.4 provides 27 channels that operate in different frequency bands with varying data rates (20 - 250 Kbps). The Mac layer manages the medium via the CSMA/CA protocol [23] and ensures also the device’s association, disassociation, and synchronization. The function of the adaptation layer is to adapt IPV6 packets and fit them into the IEEE 802.15.4 format. It also ensures the fragmentation of IPV6 packets into Mac frames. The transport layer of the network stack adopts a simple transmission protocol which is the User Datagram Protocol (UDP) [24] .
The routing process in 6LoWPAN starts when a reduced function sensor has to send a packet to another IP sensor. In this case, the higher full function sensor that is connected to the reduced function sensor will be responsible to send the packet hop by hop until it reaches the gateway. Actually, the gateway uses the IP address to locate the domain of the remote IP sensor. Further, 6LoWPAN ad hoc on Demand Distance Vector Routing (Load) has been adopted for 6LoWPAN routing. Like AODV [25] , Load uses route request and route reply messages but it does not use the sequence number. It also relies on the Link Layer Notification messages that approve the reception of Mac messages. It creates a mesh topology and runs on full function devices. A route is selected by Load if it includes a certain number of links such that their accumulated route cost (LQI) [26] is worse than a certain threshold. The route should also include less hops between the source and the destination. Hierarchical routing (HiLow) is another protocol that is used in 6LoWPAN to minimize the delay. The idea is to build a hierarchy and then 6LoWPAN device will either join an existing parent or become a parent. According to [27] 6LoWPAN is used for networks with high processing capabilities. For this end, Protocol for Low Power and Lossy Networks (RPL) [28] has been designed for constraint devices in power, computation, and memory capabilities. RPL is a distance vector routing protocol that is based on IPV6. It builds a Destination Oriented Directed Acyclic Graph (DODAG). Many metrics may be used to construct a DODAG: the Expected Number of Transmissions (ETX) [29] , the remaining energy of the devices… Energy-Efficient Probabilistic Routing (EEPR) [30] is an alternative solution for routing in an IoT environment. It is based on the same idea of AODV but the transmission of a RREQ packet follows a certain forwarding probability that depends on the residual energy and the ETX metric The proposed mathematical equation shows that the forwarding probability will be high if the ETX metric is low and the residual energy is high. The simulation results show that the variance of the residual energy of EEPR is smaller than the variance of the residual energy of AODV. The work in [31] proposed the Context Awareness in Sea Computing Routing Protocol (CASCR). It exploits the idea of sea computing that was first announced at the Chinese Academy of Science High Technology Planning Seminar in 2010. The sea computing refers to the embodiment of autonomous devices into various things. It produces effective intelligent decisions through local interactions of the devices. CASCR associates a state and some operations to each device. The states include: full-working, serving, single working, sleeping, and hibernating. The set of operations contains: gather information, transmit information, apply information fusion, and generate a control operation. In particular, CASCR predicts the new state of each device using Markov chains [32] that defines the new state as a function of the device’s history. The device holding a routing request should send it to its first hop neighbors that are provided with a context data table which specifies the network topology in term of: neighbors, subordinators, superior, colleagues and disabled devices. The context data table is used to find the next hop. The simulation results show that CASCR has low energy consumption. The authors of [33] involved in developing a cross-layer protocol to meet the performance parameters of IoT applications: minimum date delivery rate, and maximum packet delay. The proposed protocol runs on the top of IEEE 802.15.4. It combines the network topology information, the performance requirements and the link performance to decide on the next hop for routing data. It extends the ETX metric by considering the packet loss which may be generated by the MAC contention. The authors of [33] conducted a simulation and demonstrated that the reliability metric is better than the ETX metric. The author of [34] addressed traditional routing protocols for Adhoc networks such as AODV, DSR, and OLSR [35] and discussed their performance in an IoT environment. Three metrics were used:
・ Routing overhead: which is the result of the number of route packets by the number of data packets.
・ Average end to end delay: concerns the total delay that is generated by route discovery, queuing…
・ Throughput: it is the result of the number of packets received by the destination by the number of packets sent by the source.
The paper of [34] contains simulation results that are based on the random waypoint mobility model. It illustrates that the overhead of the three protocols depends on the number of nodes. The percentage of mobile nodes is another parameter of the simulation. However, we mention that the authors did not define their network topology nor the IoT architecture.
4. Event-Based Routing
Publish/subscribe is an efficient way for asynchronous communications. It allows to specify interests in a certain event conditions. If an event has been trigged, the subscribers that are interested to that event will be notified [36] . There are two basic types of publish/subscribe systems: topic and content-based publish/subscribe. In the former scheme, the system’s device subscribes to topics, which are identified by keywords; whereas in the latter scheme, the subscription concerns the actual content of the considered event. The drawback of topic-based publish/subscribe concerns the accuracy. Some devices may be notified about events they are not interested in. In return, content-based publish/subscribe has been widely used but it lacks efficiency due to the mapping between subscriptions and events [37] . Our focus in this section is to study the problem of event delivery for publish/subscribe system. Our motivation stems from the architecture of IoT systems that requires a middleware to coordinating between different components of an IoT system and providing abstractions in term of syntax and semantic for a wide range of diverse devices [1] [6] . In reviewing the literature on middleware for IoT systems, we considered that many middleware systems are based on publish/subscribe communications for IoT devices to ensure a real-time tracking of the events [38] -[41] … So, we will present existing event routing protocols for publish/subscribe systems which are classified into namely, filter and multicast-based routing as shown in Figure 1. The idea of filter-based routing is to impose a certain forwarding scheme: the sub-server that is aware about an event should only forward it to its sub-servers leading to the subscribers that are interested to a specific event. The concept of multicast-based routing is different because the routing decision is made only once at the publisher. Multicast groups are constructed and the events are broadcasted to the appropriate groups. The author of [42] distinguished three categories for event routing: flooding, selective-based routing that include rendez-vous and filter-based routing, and gossiping based routing that is probabilistic and suitable for dynamic environments.
An interesting recent technique for content-based routing is called Kyra of [42] . It generates a two level topology through the Hierarchical Agglomerative Clustering (HAC) algorithm [43] that groups the servers into
![]()
Figure 1. Filter and multicast-based routing.
clusters. Then, Kyra builds a spanning tree [44] that includes clique servers which know about each other. Typically, Kyra filters the received events and forwards them along the tree. The key feature of Kyra is its ability to balance the routing load over the sub-servers. The authors of [45] proposed the Context and Content-Based Routing Protocol (CCBR) for multi-sink mobile wireless sensor networks. It capitalizes on the broadcast feature of wireless networks. Each network node maintains a distance and a content table. The first table keeps track of the estimation of the distance between the considered node and the network’s sinks. The content table serves for storing the interests of sinks that are relevant for the considered node. According to CCBR, a node that receives a packet should compare the distance included in that packet’s header to the distance that separates itself from the sink. The packet will be dropped if its distance is greater than the packet distance. Otherwise, it will update the distance in the header and schedule the packet for transmission. The results in [45] show that CCBR’s delivery rate is good and the routing cost is low. Another technique for event routing has been proposed in [46] . The Topic-based Event Routing (Tera) is a powerful technique for large scale dynamic peer to peer systems where the network nodes can subscribe/unsubscribe at any time. It associates a tag to each event. The tag represents a topic and it should be used to deliver the events to all subscribers that have expressed their interests in the corresponding topic. Tera is based on a distributed algorithm Overlay Maintenance protocol (OMP) [47] and adopts inner and outer cluster routing such that the inner routing is just a broadcasting process. The scalability of Tera was tested in [46] and it demonstrates a good scalability. More importantly, [48] provided a formal description of a content-based routing scheme that includes distributed brokers which are connected to an acyclic topology and each broker handles a private routing table. The suggested protocol in [48] enables a broker to send a notification to its local clients upon receiving a publish message. The authors of [48] described also formally a simple filter-based routing protocol that floods new canceled subscriptions to all other brokers.
5. EECBR
Our proposed protocol aims at providing an efficient routing service for IoT sensors which are responsible for collecting and routing data. Different from routing protocols for wireless sensor networks, EECBR takes advantage of the publish/subscribe middleware to achieve two functions without any prior knowledge of the location of the underlying sensors:
1) Organizing IoT’ sensors via a virtual topology that is created according to the set of sensors that are interested to a specific event. It also considers the energy of the sensors.
2) Routing the events hop by hop through the virtual topology until reaching the interested sensors.
Assume the scenario of a smart home where the equipment integrates sensors like: door control sensor, motion sensor, light sensor, humidity sensor, window control sensor… and RFID systems. The scope of such system concerns ensuring the safety and the security of the house. The integrated sensors are connected to the Internet to allow a remote control of the house. In such scenario, the activity of some sensors is related to other ones. For example, the light sensor depends on the motion sensor. Further, some sensors may adjust their power of transmission according on the events provided by the light and the humidity sensors. So, our idea to use publish/subscribe communications stems from the possibility of registering dependent sensors to the interested events. Upon the occurrence of an event, the dependent sensors are notified and the virtual topology is used to relay the events form the publishers to the interested sensors.
Our protocol is based on the following assumptions:
・ Our IoT system includes sensors that are integrated to the things.
・ Each sensor is aware about its neighbors.
・ Each sensor has a battery with an initial random energy amount.
・ The energy is decreased for each transmission.
・ The topology of the things is ad hoc.
・ The things are static.
・ The links between the things are reliable with no data loss.
・ The IoT system is provided by a publish/subscribe middleware and the role of the network layer is to deliver the published events to their adequate destinations.
EECBR is a simple protocol that tackles the problem of routing IoT events in an energy-efficient manner by balancing the energy consumption of the IoT devices. It first creates a virtual topology. The virtual topology may be a tree or a set of clusters. It depends on the network’s topology. Starting from a set of sensors which are interested to a specific event, EECBR marks a sensor as a leader if it covers the maximum set of interested sensors that are located in its communication range. EECBR may add more levels depending on the topology of the network.
Different from many protocols that establish a scheduling and decide on awake/sleep sensors by electing some leaders for monitoring a certain area, our contribution builds a virtual topology to organize sensors and reduce the communication cost. The leaders may ensure two functions: collecting data that is gathered by sensors that are located in the range of the leader, relay events to the sensors that are interested to them. The context of our proposed protocol concerns the second function. EECBR calculates the contribution of each sensor for deciding on the leaders. The contribution of a sensor s depends on: the number of uncovered sensors that are interested to a specific event/uncovered leaders of level (i-1) that are located within the range of s, and the energy of s. a sensor becomes a leader if its contribution if it has the largest contribution. This enables to broadcast an event to the intended receivers. The algorithm for EECBR is illustrated in Figure 2.
The probability for constructing a tree is very high for fully and partially connected networks. Our virtual topology is bottom-up. It starts with the interested subscribers. Our idea is closely related to [49] which maximizes the network lifetime by finding the covering nodes for a set of targets. So, we proceed to define the contribution of each device as the set of uncovered interested subscribers by the device’s energy and the device with the highest contribution is selected to be a leader.
Upon constructing the first level of the virtual topology more levels may be included. The routing process is performed in a distributed way using the following rules:
1) Each publisher sends the generated event (E) to its leader.
2) Each leader sends the received event (E) to its connected interested subscribers and any other leader that is connected to it.
6. Simulation Results
We have conducted our simulation runs through the Omnet++ simulator. OMNeT++ standing for Objective Modular Network Test-bed in C++ is an object-oriented modular discrete event network simulation framework that has a generic architecture. OMNeT++ itself is not a simulator of anything in particular, but rather provides infrastructure and tools for writing simulations. OMNeT++ is currently gaining widespread popularity as a network simulation platform in the scientific community as well as in industrial settings. It provides a discrete event simulation environment. OMNeT++ provides a component architecture for models. The Modules are programmed in C++ and assembled into components using NED. The main characteristic of OMNET++ is that the reusability of models comes for free. Omnet++ is successfully used for complex and queuing systems. Ad hoc and sensor networks [50] … We simulated five scenarios that are summarized in Table 1. The simulation of the scenarios that require the positions of the devices has been performed through the integration of Mixim [51] . The networks topology includes 20 devices.
We have calculated the variance of the energy per device as a metric to compare the different scenarios. By definition, the variance measures how far a set of numbers is spread out. A variance of zero indicates that all the values are identical. A small variance indicates that the data points tend to be very close to the mean and hence to each other, while a high variance indicates that the data points are very spread out around the mean and from each other. Equation (1) states that the variance depends on the mean. In case of many variables, we need to include their numbers in the variance equation.
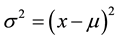 (1)
(1)
We considered the variance between the initial and the remaining energy for each device. Figure 3 shows that EECBR has the lowest energy variance. The performance of the distance-based routing (Figure 4) in term of the energy variance is better than the performance of the progress, greedy and distance-energy schemes (Figure 5, Figure 6 and Figure 7) respectively. Figure 6 and Figure 7 illustrate that the performance of the greedy and the distance-energy routing schemes are approximately similar. This means that the energy is more important than the distance for the routing decision.
![]()
Figure 4. Energy variance of distance-based routing.
![]()
Figure 5. Energy variance of progress-based routing.
![]()
Figure 6. Energy variance of greedy routing.
![]()
Figure 7. Energy variance of distance-energy routing.
7. Conclusion
In this paper, we introduced EECBR that performed a matching between IoT events and the subscribers and then routed the events through a virtual topology which was constructed from the bottom to the top. Our Omnet++ simulation results show the comparison between EECBR and other geographic routing schemes that use to the position information for deciding on the next forwarder which should be located in the way between the source and the destination. The variance between the remaining energy and the initial ones is very small in EECBR. This allows extending the lifetime of IOT sensors. Our future work will focus on solving the cross-layer issue in IoT routing.