The Objective Function Value Optimization of Cloud Computing Resources Security Allocation of Artificial Firefly Algorithm ()
1. Introduction
Cloud computing service model can save a lot of investment cost, get rid of resources such as regional restriction and time limitation, and complete the needs of different users for various calculations, storage, etc. [1] . The rational selection of workflow task scheduling strategy will have important influence on cloud computing efficiency, performance, etc.; the unreasonable scheduling may result in resource waste and cannot meet the demand of users. At the same time, in the process of scheduling, because the resource nodes jitter or lose efficacy, it will produce the security threats such as tasks to perform or delay [2] -[4] . So through in-depth analysis of workflow cloud environment task scheduling problem, designing safe and reasonable workflow task scheduling algorithm is of great significance [5] .
At present the latest research on the distribution of mobile cloud computing resources is mainly concentrated on the application of cloud computing in mobile terminals. The direction of the present study was to make the application of mobile cloud computing run on resource-constrained mobile terminals, and it can also run on the “cloud” based on the Internet [6] - [8] . So the limited resources of mobile terminal can easily give the complex computing tasks, communication tasks and other business which needs larger resources to “cloud” to complete. B. Chun mainly increased the number of executions to configure CloneCloud cloud resources, but without considering the actual running condition of the user terminal. X. Zhang made some preliminary research on the resource management to flexible application services of cloud computing network. Oberherde et al. through the cloud computing resources optimization, transferred antivirus services from mobile terminal to cloud computing network, and thus reduced the calculation burden of mobile terminal which was resource-constrained. Goayl and Carter presented an encrypted search mechanism based on cloud computing. D. Huang et al. put forward the mobile cloud computing network architecture. In this architecture, in order to use the cloud computing network and mobile terminal resources more reasonably, the author proposes a mobile terminal node as a network node in the cloud services integrated into mobile cloud computing network. In order to more effectively use cloud computing resources, some researchers have proposed a kind of resource allocation and economic optimization model based on the mobile cloud computing network. In a given allocation of resources under the condition of mobile cloud computing network, every decision step of the model can optimize the allocation of resources to different services, and according to the state of mobile cloud computing network resources, the cloud computing tasks transfer between mobile terminal and mobile cloud computing network. G. Wei et al. expounded a kind of resource allocation management model based on game theory; this model can dynamically allocate the cloud computing network resources according to the user’s quality of service (QoS) requirements. According to the dependencies of task in Heterogeneous environment, in order to meet the demand of high performance and improve the efficiency of task execution, Topcuoglu et al. presented two new scheduling algorithms, the Earliest Completion Time of Heterogeneous Scheduling Algorithm (Heterogeneous Earliest-Finish-Time, HEFT) and Critical Path Scheduling Algorithm (Critical Path-on-a-Processor, CPOP). Lan and Sun proposed the key task scheduling algorithm under the heterogeneous environment; this algorithm first defines the key tasks and idle time, and makes the task ahead of time through the critical tasks be copied to the free time slice of resources. Buyya et al. proposed cloud computing architecture based on market resources localization, and gave the resource management strategy based on the market, to support the resources localization of service level negotiation [9] -[11] .
This paper, according to the characteristics of cloud computing, puts forward a cloud computing resources security distribution model based on improved artificial firefly algorithm, in order to improve the security of cloud computing resources allocation.
2. Artificial Firefly Algorithm
The evolution process of the basic artificial firefly algorithm is completely inspired by nature fireflies group behavior, the group interaction is pushed by the intensity of fluorescence intensity and its influence. In basic artificial firefly algorithm, first we distribute the fireflies which have the same content of fluorescein and same independent decision domain in the target space we need to search by random, they communicate in their own decision domain, thus affecting the individual behavior of the fireflies around.
According to the biological characteristics of nature fireflies and the matching modify rules of artificial firefly algorithm, the basic artificial firefly algorithm in the algorithm can be divided into six stages, details are as follows:
(1) The initial deployment phase
n fireflies were randomly distributed in D dimensional search space, each firefly i has the same initial radius 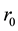 of the induction and fluorescence intensity
of the induction and fluorescence intensity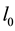 . Among them the initial radius
. Among them the initial radius 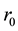 of the induction is decided by the radius of sensor.
of the induction is decided by the radius of sensor.
(2) On the basis of the objective function mathematical expression f to calculate the objective function value F of all fireflies’ locations, and in accordance with the following formula, we transform it into the corresponding fluorescence intensity value:
 (1)
(1)
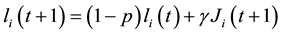 (2)
(2)
(3) Determine the neighbor
At this stage, artificial induction fireflies search the distance neighbor 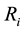 in the sensing radius, the brightness neighbor
in the sensing radius, the brightness neighbor 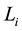 in the sensing radius, eventually determine the neighbor set
in the sensing radius, eventually determine the neighbor set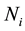 :
:
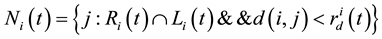 (3)
(3)
As can be seen from the Figure 1, for firefly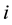 , the distance neighbor have
, the distance neighbor have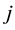 ,
, 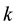 in the sensing radius, and then by calculating its brightness and probability to determine the direction of movement; For firefly
in the sensing radius, and then by calculating its brightness and probability to determine the direction of movement; For firefly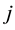 , there is only distance neighbor
, there is only distance neighbor 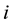 in its sensing radius
in its sensing radius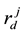 ; For firefly
; For firefly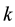 , it belongs to the empty set.
, it belongs to the empty set.
(4) Choose the moving objects
According to the surely neighbor set![]() , calculate the roulette probability
, calculate the roulette probability![]() , compare the value of each
, compare the value of each![]() , calculate and determine a moving object
, calculate and determine a moving object![]() :
:
![]() (4)
(4)
(5) Move the fireflies
Move the firefly ![]() according to the moving direction
according to the moving direction ![]() to the selected object
to the selected object![]() :
:
![]() (5)
(5)
![]() (6)
(6)
(6) Adaptive sensing radius
After firefly moving, we will modify the next iteration of the sensing radius ![]() adaptively according to the number of neighbor collection:
adaptively according to the number of neighbor collection:
![]() (7)
(7)
The change of ![]() change the local decision domain, to select its neighbors in the form of this change, the individual sensing radius changes, in view of the entire group, group behavior of multiple individuals show as the separate group behavior, the number of the clustering theory is equal to the number of clustering.
change the local decision domain, to select its neighbors in the form of this change, the individual sensing radius changes, in view of the entire group, group behavior of multiple individuals show as the separate group behavior, the number of the clustering theory is equal to the number of clustering.
3. Artificial Firefly Algorithm Optimization
3.1. Population Search Optimization Based on the Complex Method
Increased with the dimensions of the function, the solution space of the function is expanding rapidly, caused the complexity of the function. So in the later stages of artificial firefly algorithm, there will be a lot of bad fireflies around the optimal fireflies, frustrate the optimization of the algorithm precision, so that the algorithm in the final optimization precision will have very big defects.
According to characteristics of the artificial fireflies swarm algorithm and the complex method, incorporate the ideas of complex method into the artificial firefly algorithm, use the complex method to guide the search of artificial fireflies in population. Algorithm thought graph description as shown in Figure 2.
In the iteration, we will use the improved equation in this paper:
![]() (8)
(8)
![]() (9)
(9)
On the base of the complex method of population search optimization steps as follows:
(1) Random initialization ![]() fireflies and dimension within the scope of the feasible region, the parameters which is needed to initialize;
fireflies and dimension within the scope of the feasible region, the parameters which is needed to initialize;
(2) Random initialization ![]() fireflies in the position of the objective function search space;
fireflies in the position of the objective function search space;
(3) Use the formula (8) to get the center ![]() of the kth points;
of the kth points;
(4) Each firefly within their own decision-making domain![]() , through the comparing makes sure the set of firefly
, through the comparing makes sure the set of firefly ![]() which has higher luciferin;
which has higher luciferin;
![]()
Figure 2. Schematic diagram of the complex method.
(5) Through the comparison of fluorescein value, find out the worst firefly luciferin values, then according to the formula (9) to reflect;
(6) According to the formula (4) calculating the probability of firefly ![]() move to the neighborhood firefly
move to the neighborhood firefly![]() . Using roulette method to select individual
. Using roulette method to select individual![]() , then move the firefly, and according to the formula (6) to update location;
, then move the firefly, and according to the formula (6) to update location;
(7) According to the formula (7), dynamic update decision domain radius of fireflies.
3.2. Optimization Efficiency and Convergence Precision Optimization
In basic GSO algorithm, each firefly in its decision-making domain finds the firefly which has brighter luciferin, then they move to it, they use roulette method to move to it based on a certain probability, this will make the firefly mobile position is not the best location in decision domain, it will reduce the optimization efficiency and convergence precision of the algorithm. In this paper, the firefly mobile mechanism is introduced in local search operator, algorithm thought graphics can be described in Figure 3.
The concrete implementation steps of GSO algorithm with local search operator are:
(1) Initializes the fireflies’ number and dimension of search space, the parameters which is needed to initialize;
(2) According to the formula (2) calculate the firefly![]() ’s values of fluorescein
’s values of fluorescein ![]() at the corresponding position
at the corresponding position ![]() at time
at time![]() ;
;
(3) Each firefly within their own decision-making domain![]() , through the comparing makes sure the set of firefly
, through the comparing makes sure the set of firefly ![]() which has higher value of fluorescein;
which has higher value of fluorescein;
(4) According to the formula (4) calculate the probability that firefly ![]() move to the neighborhood firefly
move to the neighborhood firefly![]() . Using roulette method to choose individual
. Using roulette method to choose individual![]() ;
;
(5) Make the individual ![]() as the current optimal position to local search;
as the current optimal position to local search;
(6) Make sure the new moving direction by local searching, and according to the formula (6) to update the location;
(7) According to the formula (7), dynamic update decision domain radius of fireflies.
4. Algorithm Simulation
In order to verify the effectiveness of the improved algorithm proposed in this paper, we do the simulation experiments on it. We do the cloud computing resources security distribution optimization efficiency and convergence precision test to the standard artificial firefly algorithm and improved artificial firefly algorithm. The result is shown in Figure 4 and Figure 5.
![]()
Figure 3. Mobile diagram of the improved algorithm.
![]()
Figure 4. Contrast optimization algorithm efficiency standards and improved algorithm.
![]()
Figure 5. Comparison of convergence between the standard algorithm and improved algorithm.
From the simulation results showed that the proposed improved artificial firefly algorithm has better convergence and optimization efficiency, and the application in the cloud computing resources security distribution is good.
5. Conclusion
Cloud computing is a way of calculation which is developed with the development of computing and communications technology in recent years. How to make full use of the existing cloud computing resources, through the reasonable allocation of cloud computing resources between different areas to improve the quality of the cloud computing security service and system returns of the cloud computing network system, so as to improve the ratio of revenue and expenditure of cloud computing network, has become an increasingly prominent research topic in the cloud computing network. The simulation experimental results show that the improved model proposed in this paper has higher optimization efficiency and convergence, and it has good application effect.
Funding
This work was supported by the National Natural Science Foundation of China (Grant No. 61170132).