1. Introduction
Power-Line Communication (PLC) is developed rapidly in recent years. Because it doesn’t need to build additional transmit channel and exists almost everywhere even in the backward areas, it is mostly recognized as the solution of “last mile” to the current network communication. Since power line was not originally built for information transmission, there are several problems. One of these is the data collision. When channel transmits multiple packets at the same time, packets will collide naturally causing packets to be destroyed. The station has to retransmit packets which will cause throughput decrease in the end. Thus, HomePlug AV [1] uses CSMA/CA [2] to avoid collision happening. The principle is as follows: each time the station tries to send package, it will detect channel’s status. If the channel is idle, the station sends the packets. Otherwise, it goes into the contention mode. This method can avoid too many stations transmitting at a time hence to effectively reduce the chance of data collision.
A PLC architecture consists of head end (HE) and user modem. HE erects at the transformer side and one side is connected to the transmission backbone, like Ethernet. Another side is connected to the power line to receive request from PLC users. The user modem connects to the communication equipment to communicate through the power line. If a PLC modem accesses the Internet, it will receive packets from the head end through the power line.
Although HomePlug AV standard can guarantee high throughput when the number of nodes is very limited, when the node number increases, the value of contention window setting in HomePlug AV will be big which leads throughput to decrease accordingly. In [3] , information theory and data mining technique were applied for network traffic profiling. Some research tasks focused on enhancing throughput via the revised MAC layers [3] [4] - [8] . Among which, the authors of [3] proposed an adaptive contention window mechanism for HomePlug AV and verified their designs through experiments. They have conducted an experiment to reach the best successful transmission number in a beacon period. That is, if the number of successful transmits is less than the optimal one, it means that the current contention window size is inappropriate. It will then change it in the next beacon period. In 2011, the authors of [4] found the optimal contention window value for the situation of different nodes. Both of them show that throughput can be improved in an efficient manner if the size of contention window is optimized.
Even though previous research can achieve the desired effect, most of them require information of all stations. That means that they need another bit to transmit that information to each node. Or, they have to modify the protocol. In this research, we propose a new strategy of an adaptive contention window mechanism that doesn’t change the original CSMA/CA procedure or require station’s information as a basis of modifying the contention window size. Our correction factor includes the CSMA/CA parameters. Soft experiments at the network simulator, NS3, show the improved effect in throughput.
2. Principles of CSMA/CA
For PLC, when a station tries to send a packet, it first checks the channel condition. If the channel is in idle, it transmits data accordingly. Otherwise, it enters the contention mode. The contention period is a region to contend the authority of using channel by other stations.
Before going into the contention period, the station will allocate each packet priority. Packets with higher priority use the channel first. If there are several packets possessing the same priority, it will become the contention period. In priority resolution, HPAV define four parameters, CA0, CA1, CA2 and CA3. CA3 present the highest priority, and CA0 is the lowest, etc. Each station will be defined the packet’s priority in two priority regions denoted PRS0 and PRS1 respectively. At each PRSi, the station chooses to send or not to send signals. According to the PRS, we can determine the packet’s priority level. Different priority level corresponds to different parameter settings. Table 1 shows the role of it.
After implementing the setting of priority, each station equips with a specific packet priority level. Higher priority level wins the contention and possesses more chances to send the packet. If there are several stations with the same priority, it will proceed to the next stage-random backoff procedure.
For the random backoff procedure, we first introduce contention window and three counters, backoff counter, deferral counter and backoff procedure counter.
1) Contention window (CW): Contention window is a fixed number defined in Table 2. It is used to determine the value of backoff counters.
2) Backoff counter (BC): Backoff counter’s value chooses from a random value of contention window. It means that CW is the maximal value of BC could be. BC will be decreased by one, each time when it senses a busy status in the channel until BC equals to zero. The station will transmit the packet.
3) Deferral counter (DC): When the number of users in the local area network is large, using only BC to delay the transmission time is not enough. Deferral counter is used to avoid collision further. At the beginning, DC is fixed. Different CAs have different initial values of DC corresponding to. If the channel status sensed is idle, DC remains unchanged. On the contrary, if it is busy, DC will be decreased by one. When DC reaches to zero, the time contention is declared “fail”. It will restart contention again.
4) Backoff procedure counter (BPC): Backoff procedure counter is set to be zero initially. When the station
![]()
Table 1. Relationship between PRS and CA.
fails to transmit packets (happened collision). Station will attempt to contend again and BPC will be increased by one. According to different BPC, there are different DC and CW settings to respond.
We express the behavior through Markov chain [4] in Figure 1. Each time we begin the backoff procedure by setting the same probability to obtain the value of BC from zero to CW (=W). Therefore, each probability at the top statement is 1/W. At each time slot (defined in HPAV is 35.85 ms), the station will detect the communication channel. The probability is P to sense an “busy”, and it is 1 − P to sense a “idle”. When DC or BC is equal to zero but the channel status sensed is still in busy. BPC will be increased by one and BC will be rechosen. That means that there are too many users occupying the channel. Then, DC and BC need to be increased for longer waiting time for collision avoidance. When BC reaches to zero and the channel status sensed is idle, the station can then transmit packets. The complete flow chart is illustrated in Figure 2.
The time of successful transmission can be expressed as in Figure 3. PRS0 and PRS1 are regions to decide packets priority, a contention region refer to the waiting time of the contended channel before transmitting packets, data transmission is the time of packets sent in the PHY layer; RIFS refers to the time before sending acknowledgement, ACK is the time of transmitting acknowledgement, and CIFS is time before starting the next packet. Among which, PRS0, PRS1, RIFS, ACKS, and CIFS are fixed numbers in HomePlug AV, see Table 3.
3. Slot Utilization and Relation with Throughput
Referring to Figure 3, we define  and
and 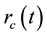 respectively, the time required for a successful data transmission and the time for a collision happened during data transmission. The two terms can be expressed by
respectively, the time required for a successful data transmission and the time for a collision happened during data transmission. The two terms can be expressed by
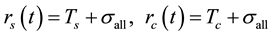
where 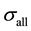 is the total slot time in the contention region and
is the total slot time in the contention region and
 (1)
(1)
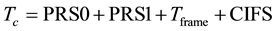 (2)
(2)
If we define 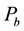 as the probability of slot sensed in busy. From [2] ,
as the probability of slot sensed in busy. From [2] ,  can be expressed by
can be expressed by
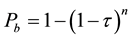 (3)
(3)
where  is the probability of the station transmitted in a slot and n is the number of stations. Since Pb reflects
is the probability of the station transmitted in a slot and n is the number of stations. Since Pb reflects
![]()
Figure 2. Operational flow chart of the CSMA/CA procedure.
![]()
Figure 3. The process for a successful transmission.
the probability of channel in busy status, it can also be defined as
![]() (4)
(4)
This is also referred as “slot utilization” [9] .
We conduct several extensive simulation experiments on the Network Simulator 3 (NS3) [10] . NS3 is an event driver developed to mimic network environment. Compared with its predecessor NS2, NS3 is completely developed by C++ and the system architecture is simpler than that of NS2. We record slot utilization every 30 seconds at various node arrangement. There are four CW cases in the simulation. The results are shown in Figure 4(a) where Ts defined in Equation (1) is set to be 3500 μs and the slot time is similar to that defined in Table 3.
In Figure 4(a), red line refers to HomePlug AV standard which let CW = [7 15 31 63]. Other lines are the situation with different CW values. When CW is set to be larger, the probability for obtaining a larger BC is higher. Correspondingly, its slot utilization is comparatively smaller. However, even the CW setting is as such, the slot utilization increases continuously. This fact inspires us to consider whether one can use slot utilization to relate the congestion level. Another simulation been conducted is to observe the variation of throughput at the same setting, illustrated as in Figure 4(b).
In Figure 4(b), HomePlug AV standard has the highest throughput when the number of contention nodes is small. However, when the node number increases, the throughput will decrease because of the higher collision probability. On the contrary, CW = [63 127 255 511] setting possesses the worst throughput at the beginning. That’s because it wastes too much time in the idle slot. However, it will cause low collision probability when the node number becomes larger. This why it possesses highest throughput when the node number is more than 35.
Therefore, if one can assign the system a low CW setting when the node number is few and a high CW when the node number is large then better throughput could be expected. This is the basic idea behind the adaptive contention window mechanism proposed in this research.
To compare Figure 4(a) and Figure 4(b), from the node number 5 to 12, CW = [15 31 63 127] has the highest throughput. From 13 to 35 nodes, CW = [31 63 127 255] possesses the highest throughput. After 35, CW = [63 127 255 511] has the highest throughput. Most of their slot utilization are in 0.1 ~ 0.2 when they possess the highest throughput. One can thus infer that the value of slot utilization in 0.1 ~ 0.2 would be the best setting in this case.
![]()
![]() (a) (b)
(a) (b)
Figure 4. Simulation on different CW setting: (a) Slot utilization; (b) Throughput.
In summary, if one can control slot utilization in an appropriate region then better throughput could be expected.
4. Adaptive Contention Window Mechanism
From [11] , it was known that when ![]() defined in Equation (3) as the following way, throughput of the network will exhibit the best performance:
defined in Equation (3) as the following way, throughput of the network will exhibit the best performance:
![]() (5)
(5)
where ![]() is the average time of collision transmission
is the average time of collision transmission ![]() in the slot time
in the slot time ![]() as
as
![]() (6)
(6)
Substituting Equation (6) into Equation (5) yields the new ![]() as
as
![]() (7)
(7)
Substituting Equation (7) into Equation (3) gives the optimal slot utilization which will lead to the optimal throughput. We set this optimal slot utilization as the standard which is expressed as![]() :
:
![]() (8)
(8)
where![]() .
.
After recognized data received, every station records the slot utilization by using Equation (4) for the last successful transmission packet. If slot utilization of the last packet is greater than![]() , it means that the current contention window is not big enough which may cause the congestion. It will assign the system a larger contention window. Otherwise, it will adjust the contention window for reduction. Our adaptive contention window architecture can be illustrated as in Figure 5.
, it means that the current contention window is not big enough which may cause the congestion. It will assign the system a larger contention window. Otherwise, it will adjust the contention window for reduction. Our adaptive contention window architecture can be illustrated as in Figure 5.
In this figure, ![]() is expressed as slot utilization of the last packet. By the revised function-
is expressed as slot utilization of the last packet. By the revised function-![]() , it converts the slot utilization to a revising factor to multiply the original contention window (CW = [7 15 31 63]). That is, the contention window of the next packet will be changed to
, it converts the slot utilization to a revising factor to multiply the original contention window (CW = [7 15 31 63]). That is, the contention window of the next packet will be changed to![]() .
.
![]()
Figure 5. System architecture of the proposed adaptive contention window mechanism.
We suppose that the revised function ![]() is given in the form shown in Figure 6. While the slot utilization is in between
is given in the form shown in Figure 6. While the slot utilization is in between ![]() and
and![]() ,
, ![]() appears as a linear positive gain. Since CW = [7 15 31 63] is originally suitable for the case with only a few nodes, it doesn’t need to be small when the slot utilization is apparently too small. Therefore, we set
appears as a linear positive gain. Since CW = [7 15 31 63] is originally suitable for the case with only a few nodes, it doesn’t need to be small when the slot utilization is apparently too small. Therefore, we set ![]() to be 1. On the other hand, we define M as the expression of
to be 1. On the other hand, we define M as the expression of ![]() to be a variable.
to be a variable.
Assume ![]() is expressed by the following form when
is expressed by the following form when ![]() is in between
is in between ![]() and
and![]() :
:
![]() (9)
(9)
Substituting ![]() and
and ![]() into Equation (9) yields m and k as
into Equation (9) yields m and k as
![]()
Finally, we obtain the complete form of the revised function![]() :
:
![]() (10)
(10)
The main idea here is to incorporate slot utilization to determine congestion level of the network. However, slot utilization determined by Equation (4) leads to a large alteration if the last packet is successfully transmitted at BPC = 0 (Table 2). Under this situation, it will bring the next packet with incorrect information in the congestion level. To tackle, we propose a virtual slot utilization instead of the previous slot utilization. A virtual slot utilization will lie in between ![]() and
and![]() . The neighboring two packets will not exhibit large difference virtual slot utilization. The virtual slot utilization comes from the following process.
. The neighboring two packets will not exhibit large difference virtual slot utilization. The virtual slot utilization comes from the following process.
We define ![]() and
and ![]() as the virtual slot utilization of the packets m and
as the virtual slot utilization of the packets m and![]() , respectively and
, respectively and ![]() is the slot utilization of the packet m, shown as in Figure 7.
is the slot utilization of the packet m, shown as in Figure 7.
The packet m + 1 uses ![]() as the previous slot utilization which adopts Equation (10) to obtain the revising factor as its contention window.
as the previous slot utilization which adopts Equation (10) to obtain the revising factor as its contention window. ![]() is obtained by the previous packet’s virtual slot utilization
is obtained by the previous packet’s virtual slot utilization ![]()
and the slot utilization of the packet m. If![]() ,
, ![]() will be
will be ![]() to increase the revising factor. If
to increase the revising factor. If![]() ,
, ![]() will be
will be![]() . If
. If![]() , set
, set![]() . We replace the slot utilization by the virtual slot utilization according to Equation (10):
. We replace the slot utilization by the virtual slot utilization according to Equation (10):
![]()
Figure 6. Correction factor of the contention window![]() .
.
![]()
Figure 7. Sketch of slot utilization ![]() and virtual slot utilization
and virtual slot utilization![]() .
.
![]() (11)
(11)
By this process, every station CW will reach to a region which the probability of every station transmitting packets will be close. The revising factor ![]() will be increasing continuously when
will be increasing continuously when ![]() as well.
as well.
While the previous method works in an efficient way, there is a weakness, i.e. the contention window mechanism shows lower throughput when the node number is few. That’s because if we modify the contention window at BPC = 0 by the previous method, it tends to prompt a larger revising factor when the node number is few. Thus, it still exhibits a large contention window causing lower throughput. It is expected that, at each time instant, ρ could really reflect the previous congestion level. Thus, when n is large, we don’t want the station transmits at the first contention period time. It means that one still needs a larger CW at BPC = 0 when the node number is large. Therefore, one has to define an updated revising factor for the state BPC = 0.
Unlike the revising factor characterized in Figure 5 using a simple multiplication to modify the contention window, the revising factor at BPC = 0 should be updated in the way of addition. Comparing to the multiplication operation, the amount of addition should be smaller. It will be more suitable for the case of BPC = 0 since its deferral counter is 0.
The modification is to introduce a correction factor![]() , say
, say
![]() (12)
(12)
where the operator![]() . By this way, we obtain an integer
. By this way, we obtain an integer![]() , with its values in between 1 to 4, to indicate the congestion level.
, with its values in between 1 to 4, to indicate the congestion level.
Next, we record the counter of the backoff procedure of the last packet, denoted![]() . To proceed, set the maximum value of
. To proceed, set the maximum value of ![]() to be 3 and define
to be 3 and define
![]()
Therefore, the value of ![]() will be from 1 to 4. Combining
will be from 1 to 4. Combining ![]() and
and ![]() forms a congestion level indicator as
forms a congestion level indicator as
![]()
where Table 4 lists all possible values of![]() .
.
We choose ![]() as our revising factor when BPC = 0. By this process, the station will has less probability to transmit at the first round in the backoff region when the node number is large. It doesn’t influence throughput when the node number is fewer.
as our revising factor when BPC = 0. By this process, the station will has less probability to transmit at the first round in the backoff region when the node number is large. It doesn’t influence throughput when the node number is fewer.
The complete design process of our adaptive contention window process can be summarized as follows:
Step 1: Based on the given slot time![]() , collision transmission time
, collision transmission time ![]() and node number n obtain
and node number n obtain ![]() as
as
![]()
Step 2: Define the revising factor ![]() by
by![]() :
:
![]()
Step 3: Count the idle and busy slot numbers of the last transmission packet to obtain the virtual slot utilization:
![]()
![]()
Step 4: Specify the revising factor ![]() when BPC = 0 in Table 2:
when BPC = 0 in Table 2:
![]()
![]()
![]()
Step 5: Update the contention window via:
1) Backoff procedure is at BPC = 0:
![]()
2) Backoff procedure is at BPC > 0:
![]()
So far, our focus is only in own station. However, the station number in Equation (8) is not fixed which is unknown in general. To resolve this problem, we calculate Pb.opt ![]() with different n, see Figure 8.
with different n, see Figure 8.
When the node number is in 1 ~ 200, its value will not significantly affect![]() . To prove the node numbers will not influence
. To prove the node numbers will not influence ![]() further, we calculate the sensitivity when n is larger than 200.
further, we calculate the sensitivity when n is larger than 200.
Define![]() . It follows that the sensitivity function of Pb.opt with respect to the node number n is given by
. It follows that the sensitivity function of Pb.opt with respect to the node number n is given by
![]()
Figure 8. Variation of Pb.opt on different node numbers.
![]()
When n > 200, the terms ![]() and
and ![]() will be smaller than 1. However,
will be smaller than 1. However, ![]() . Thus,
. Thus,![]() .
.
In the following study, the network node number n is set to be 10. Furthermore, if we consider CW = [127 255 511 1023] as the largest contention window, which will be approximately 15 times to the case of CW = [7 15 31 63], then we set the maximum revising function M to be 15.
The operational flow chart of the updated adaptive contention window mechanism is illustrated in Figure 9.
5. Experimental Results
The goal of this research is to acquire higher throughput while maintaining slot utilization. The simulation experiments have been conducted at the network simulator NS3. We set ![]() to be 35.84 μs which remains the same as in HomePlug AV. Simulation study is mainly conducted for different Ts and CW.
to be 35.84 μs which remains the same as in HomePlug AV. Simulation study is mainly conducted for different Ts and CW.
Figure 10(a) shows slot utilization for various CW settings. No matter HomePlug AV standard or other CW settings, their slot utilizations exhibit large variations when the number of nodes increases. However, there is
![]()
Figure 9. Operational flow chart of the proposed adaptive CW mechanism.
only slight difference among different cases in our proposed approach. This result shows that our method is effectively to control slot utilization. Even for a large scale network, it shows no significant difference.
After verifying slot utilization, the main point of this research is to get better throughput on the large scale network.
We prove in the follows that the proposed approach exhibits the best throughput performance while comparing to other fixed CW settings.
Including the original HomePlug AV (CW = [7 15 31 63]). All packets are supposed to possess the same priority and all stations are on the saturated situation which means that all stations have packets to transmit at all time. We record the average throughput every 30 seconds for each condition.
Figure 10(b) shows throughput of various CW settings with Ts equal to 3500 μs. HomePlug AV standard exhibits the highest throughput at the beginning. When the node number becomes large, HomePlug AV standard’s CW setting is not big enough because its throughput decreases seriously. On the other hand, CW = [63 127 255 511] has the lowest throughput at the beginning because the system wastes too much time on the idle slots. However, it rises subsequently when the node number become large. Our method shows the highest at all time since its CW setting is not fixed. When the node number is relatively few, it uses a small CW. When the node number increases, it automatically increases the CW value accordingly. Thus, when the node number becomes large, it still exhibits low probability in network collision. That’s why it can keep high throughput of the network over the whole communication time. This is as expected before. Figure 10(c) shows that when the node
number is increased to 95, it performs as the cases of CW = [127 255 511 1023] in the simulation study. The simulation result shows that when the node number approaches to a large value, throughput will converge to a small region. Thus, setting an extremely large CW doesn’t bring positive effect. That’s also the reason that we set a limit to![]() .
.
To prove performance robustness of the present mechanism, we conduct experiments for different transmission time. Figure 10(d) illustrates that throughput of the successful transmission time equals 5500 μs. This shows the similar result, our method performs the best at all time. From Figure 10(b) and Figure 10(d), it can be seen that if transmission time is less, the degree of CW affecting throughput is larger and our adaptive CW mechanism performs better than other cases as well.
We also verify the case when there is an abrupt change in the node number and examine if it still works. Consider the network has 40 nodes at the beginning. At 60 seconds, it reduces to 10 nodes. We compare the situation with 10 nodes at the beginning and record throughput at each second. The simulation result is shown in Figure 11(a). It displays that after 60 seconds, throughput of the situation 1 has been improved and quickly approaches to the line of situation 2. This endorses performance robustness of our proposed mechanism
Finally, the number n in Equation (8) was changed to 10 at the previous simulation test. To prove that it won’t significantly alter the result, we conduct extra tests with the number of nodes n = 30 and compare it to the case of n = 10. See Figure 11(b) for the result. It clearly shows that the value of n doesn’t significantly affect throughput. That demonstrates robustness of our proposed approach to the network complexity.
![]()
![]() (a) (b)
(a) (b)
Figure 11. Throughput at different special case: (a) Situation 1: 40 nodes at network beginning. It remains 10 nodes after 10 s. Situation 2: 10 nodes at all time; (b) Various setting of Pb.opt.
6. Conclusion
PLC is becoming mature in recent years. However, as the usual network communication, the network congestion problem is crucial when considering maintaining communication quality. While HomePlug AV is already a mature protocol in PLC, we propose here an adaptive contention mechanism instead of formulating a new protocol. The adaptive contention window scheme only needs the information from CSMA/CA in HomePlug AV. In addition, because the information needed is self-contained, one does not need not to correct the PHY layer setting to acquire extra information from other stations. All needed are to substitute the new CW and BC into the original HomePlug AV mechanism. This makes the approach more practical and presents better feasibility. From the simulation experiments conducted at NS3, it is found that the proposed scheme can effectively improve throughput. We have tested it with a variety of several scenarios; satisfactory results have been observed which show identifiable improvement of our proposed design.
Acknowledgements
This research was sponsored by National Science Council, Taiwan, under the Grant NSC 101-2221-E-005- 015-MY3.