An Anonymous Authentication Scheme for Vehicle-to-Grid Networks ()
1. Introduction
Depletion of fossil fuel reserves and prominence of environment problem gives a wakeup call for finding the alternative energy sources for these sectors. Because the traditional power grid has the feature of high cost, easy to cause waste and unreliable system, and with the increasing user demand for electricity diversity, traditional power grid has already can’t meet the development needs of the future [1]. However, smart grid can meet this Long-term demand. Smart grid support and encourage integration of new energy power generation system (such as wind energy, tidal power, solar power generation system), but because of the discontinuity and randomness, new energy will cause the fluctuation of power grid, so in order to smooth the fluctuations and ensure the stability of power grid voltage and frequency, smart grid need other auxiliary system as a compensation of new energy system. Vehicle to grid can be used as a buffer of new energy.
Vehicle to grid technology allows bidirectional energy exchange between electric vehicles and the power grid under the unified dispatch and control of power grid, and it is an integral part of the smart Grid. The core idea of V2G is using the storage energy of a large number of EV as a buffer of power Grid and new energy. When the power load is high, EV will feedback the surplus electricity to the power grid, and when the load is low, a large number of EV battery pack can be used to store excess power grid electricity. In this way, the V2G technology not only can be used as a buffer of new energy, but also play the role of peak shifting. Advantages of V2G: 1) using EV as a power grid buffer, and providing ancillary services for power grid, such as peak shaving, spinning reserve, reactive power compensation, etc., 2) providing EV owners with an extra income, and offsetting part of the cost to buy electric cars, which is conducive to the popularization of clean vehicles, 3) increasing power grid stability and reliability, and reducing the power system operating costs [2].
The remainder of paper is organized as follows: section II introduces security threats and requirement of V2G communication. Section III presents an anonymous group signature authentication scheme. Section IV shows the security analysis of our scheme. Finally, section V makes a conclusion.
2. Security Threats and Requirements of V2G Communication
V2G should follow a fundamental principle: V2G cannot reduce or damage the security of smart grid. Lu et al. [9] divided the threat of SG into three categories: 1) availability of communication network; 2) integrity of communication data; 3) confidentiality of communication data. These security threats are also exist in V2G. Here we present some specific V2G security threat scenarios and serious consequences.
・ When V2G communication network is under attack and data have been tampered, security control center will make wrong decision, which will influence the stability of power grid and charging/discharging plan of EVs. If a wide range of communication networks are subject to this type of attack, it will lead to the entire power system run under the conditions of fault data, and bring serious threat to the safety of power grid.
・ When V2G communications network is under distributed denial of service attack (DDOS), related data information will be delayed, blocked, or even damaged. PEV/PHEV charge and discharge cannot be reasonably arranged so as to adapt to the current network conditions, which is likely to aggravate the load on the grid. Users can’t get the vehicle energy state, the state power load and billing information etc. in time, and thus they cannot make full use of time-sharing electricity to charge and discharge EVs.
・ Data privacy of V2G in the process of communication include: the vehicle’s location information, the user’s identity, battery type, the user’s payment information, ST process information, etc. Regardless of the privacy protection would be likely to lead to leakage of users’ personal identity and electric car location information. A malicious attacker can also deduce user’s habits (activities range of the user, and, driving path and distance information) by basing on a lot of user data, such as charging time, charging locations and charging amount information [10].
・ When malicious terminal connected to the electricity grid in the form of V2G, the data of DSO can be tapped, forged and damaged, so it is needed to firstly verify identity in DSO communication network, which requires authentication protocol which has efficient design and can resist various attacks to meet the needs of real-time and security of V2G communication network.
3. An Anonymous Group Authentication Scheme for V2G
Boneh’s group signature has advantages of short signature and save communication bandwidth [11], here we take the group signature as cryptography foundation of the proposed scheme.
3.1. System Model
The system model is described in Figure 1. There are five kinds of entities involved in the architecture, including trusted authority (TA), central aggregator (CAG), local aggregator (LAG), charging/discharging station (ST), electric vehicles (EV). TA is responsible for assignment of public/private key, certificate of EV, and tracing of signature. CAG divide the recharge area into a number of LAG subsets. LAG carries out register of EV, distribute group for EV, and generates group public key and private key of group member. ST can directly monitor and communicate with each EV and send the collected monitoring data to LAG, and then provides charging or discharging service for EV.
3.2. Authentication Scheme
Boneh’s [11] group signature has advantages of short signature and save communication bandwidth, so we make the group signature as cryptography foundation of this scheme.
1) System initialization
a) CAG divides itself into a number of subsets, like LAG1, LAG2, ・・・, and announces them in the public.
b) EV sends its identity information IDEV to TA. TA generates public/private key pair for every entity (EV, ST, LAG, and CAG). EV’s public/private key pair: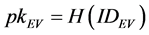 ,
, . LAG’s public/private key pair:
. LAG’s public/private key pair:
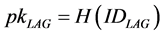 ,
,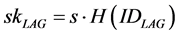 . S is the system key, which is only known by TA.
. S is the system key, which is only known by TA.
c) TA issues certificate 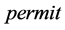 to EV, where
to EV, where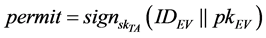 .
.
2) EV joins the group
EV complete register at LAG, LAG distributes a group for EV, and generates group public key and private key of group member. More specifically, when EV wants to join to V2G network via ST, EV sends message “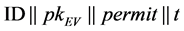 ” to LAG, t is a timestamp. After verifying the validity of the certificate, LAG generate generates group public key and private key of group member according to the following steps.
” to LAG, t is a timestamp. After verifying the validity of the certificate, LAG generate generates group public key and private key of group member according to the following steps.
a) LAG selects a generator: , and set
, and set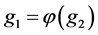 ,
,  is a calculation homomorphic mapping of
is a calculation homomorphic mapping of 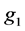 to
to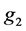 .
.
b) LAG selects 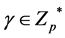 at random, and sets
at random, and sets , and announces w.
, and announces w.
c) 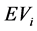 selects
selects 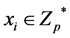 as its secret at random, and then sends this
as its secret at random, and then sends this 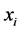 to
to
TA after encrypting it with its private key. TA computes:![]() ,
,
(![]() ), and sends
), and sends ![]() secretly to LAG.
secretly to LAG.
The group public key is![]() , each
, each![]() ’s private key is
’s private key is ![]() . The revocation token corresponding to a
. The revocation token corresponding to a![]() ’s key
’s key ![]() is
is![]() . No party is allowed to possess
. No party is allowed to possess![]() , it is only known to LAG.
, it is only known to LAG.
3) Signature computing
EV computes group signature of message M through the following steps:
a) Picking a random nonce![]() , and computing
, and computing ![]()
b) Computing ![]()
c) Selecting ![]() at random, and compute
at random, and compute ![]()
d) Setting ![]()
e) Picking blinding values:![]() , and compute
, and compute![]() , where
, where
![]() ,
, ![]() ,
, ![]()
f) Computing a challenge value ![]()
g) Computing ![]()
h) Outputting signature![]() , and EV sends
, and EV sends ![]() to ST.
to ST.
4) Signature verification
When receiving![]() , STi verifies the signiture according to the following steps:
, STi verifies the signiture according to the following steps:
a) Computing ![]()
b) Computing
![]() ,
,
![]()
![]()
c) Checking if the challenge c is correct.
![]()
If it is, the signature is verified, and STi makes revocation check, i.e. for each element![]() , STi checks whether
, STi checks whether ![]() is encoded in
is encoded in![]() , by
, by ![]() . If no element of RL is encoded in
. If no element of RL is encoded in![]() ,
, ![]() has not been revoked.
has not been revoked.
The overall process is shown in Figure 2.
3.3. Batch Authentication
Batch validation method can judge whether the signature collection contains invalid signature, thus reduce the verification time. When large-scale EVs connect to power grid, it is needed to use batch authentication to reduce verification time.
Let![]() , after ST received collection of messages
, after ST received collection of messages ![]() and signatures
and signatures![]() , it verifies the signature collection using batch authentication by
, it verifies the signature collection using batch authentication by
1) Computing ![]()
2) Checking![]() , If equality holds, continue. Otherwise, return “false”;
, If equality holds, continue. Otherwise, return “false”;
3) Select n numbers (the length is b):![]() , checking:
, checking:
![]()
If it is, return “true”. Otherwise, return “false”.
4. Security Analysis
Firstly, LAG, TA or malicious EV cannot fake other entities to generate group signature, so this scheme has strong unforgeability. For example, suppose a malicious EV has forged a signature![]() . However, ST will compute c’ and check whether c’ is equal to c signature scheme. If the signature is forged, it cannot pass the verification process.
. However, ST will compute c’ and check whether c’ is equal to c signature scheme. If the signature is forged, it cannot pass the verification process.
![]()
Figure 2. Vehicle to grid schematic diagram.
Secondly, it is not feasible for other entities to determine the vehicle status according to the result of group signature. Other group members only know group public key![]() , but they do not know private key
, but they do not know private key ![]() of each group member. Although everyone can verify each signature is generated by group member, they cannot confirm who is signer. And only LAG can open the signature to confirm the identity of the signer. So our scheme has strong anonymity, and it can ensure that the identity information of EV user cannot be leaked. So this scheme has the characteristics of anonymity.
of each group member. Although everyone can verify each signature is generated by group member, they cannot confirm who is signer. And only LAG can open the signature to confirm the identity of the signer. So our scheme has strong anonymity, and it can ensure that the identity information of EV user cannot be leaked. So this scheme has the characteristics of anonymity.
Thirdly, due to the unforgeability of this group signature, only group members can generate valid group signature. Moreover, this scheme use Hash function, and it is not feasible that outside attackers want to get EV’s private key through collecting common parameters to compute inverse operation of Hash function. So, our scheme can resist outside attack and protect data security of EV users.
5. Conclusion
This paper has proposed an anonymous group authentication scheme based on revocable group signature in view that EVs are frequently join and leave from ST, in which the signature scheme is dynamic, and EVs can dynamically join and withdraw. Algorithm overhead is essentially same with ordinary group signature algorithm. ST only need to add the vehicle information to revocation list RL when EV logs out ST, and other EVs can anonymously prove that they are not revocable group members. Besides, this scheme solves the problem that ST revocation management is complicated.