Design and Implementation of Iris Pattern Recognition Using Wireless Network System ()
Received 8 March 2016; accepted 16 May 2016; published 19 May 2016

1. Introduction
With the rapid development of communication technologies, automatic authentication is an essential problem. How to quickly and accurately recognize a person to ensure information security has become a critical social problem to be determined in this information age. Personal Identification Numbers (PINs) or passwords are not appropriate for authentication methods in some cases, because they might be forgotten by many individuals nowadays [1] .
The automated personal identity authentication systems based on iris recognition are privileged to be the most dependable among all biometric methods. The probability of two people having the iris pattern almost zero depends on the phenotypic variation. The uniqueness of iris is such that even the left and right eye of the same person is very dissimilar. That’s why iris recognition technology is becoming a solution for people identification [2] .
Images of a person’s unique characteristic is captured and kept in a data storage. Later on, when identification is required, a new image is captured and compared with the previous image in the data storage. If the new image matches with stored one, then the person’s identity is proven. In order to provide an efficient storage and rapid transmission of biometric data, iris biometric data need to be compressed to allow reduction in the space needed to store these iris images [3] [4] .
The use of wireless technology is rapidly becoming the most common way to connect to a network and to access data in remote areas. Wi-Fi is one of the many existing technologies that offer convenience way of sending data to and from a device without physical connection is becoming increasingly attractive for many users. In such environments the image has to be transferred via a network link to the respective location, often over wireless channels with low bandwidth and high latency. Therefore, a minimization of the amount of data to be transferred is highly desirable, which is achieved by compressing the data before transmission [5] [6] .
In this research, the authors have proposed a system consists of three fields: the first field includes two methods of the iris pattern recognition, which are called Libor Masek and genetic algorithms. The two used iris recognition methods are compared according to the accuracy and execution time. The second field involves the iris image compression/decompression by using Principal Component Analysis/Inverse Principal Component Analysis PCA/IPCA. The third field includes the designation and the implementation of the wireless network system to transmit both compressed and uncompressed iris images and compare between them based on their transmission time.
2. Proposed Methodology: Main Steps
The proposed methodology for the two iris pattern recognition methods is discussed and the later sections includes a brief discussion of image compression and the proposed wireless network system.
2.1. Enhanced Mask Method
Libor Masek Algorithm takes the input iris image from the Chinese Academy of Sciences Institute of Automation (CASIA) database as shown in Figure 1. The first stage is the preprocessing of the input iris image that is divided into two sub stages; the first sub stage is the iris segmentation using circular Hough transform, that locates the circular iris and pupil regions, then occluding eyelids and eyelashes and reflections by using linear Hough transform. And the second sub stage is the iris normalization using Daugman rubber sheet model, which normalizes the segmented iris region into a rectangular block with fixed dimensions to account for imaging inconsistencies. The result of normalization sub stage is two Dimensional (2D) vectors, one that represents the normalized iris region, and the other represents the noise region that contains eyelids, eyelashes, and reflections. In the feature extraction stage, the phase data from one Dimensional (1D) Log-Gabor filters were extracted using 1D Log-Gabor wavelets method. Then the output of filtering is phase quantized to four levels to encode the unique pattern of the iris into a bit-wise 2D template, and mark not useful phase data (phase amplitude close to zero) in the corresponding 2D noise mask [7] . For matching purpose, the hamming distance was computed for the classification of the iris templates to compare between input image template with the templates from data storage to check if they are matched or not as shown in Figure 1 that illustrates all stages of Masek method.
2.2. Genetic Algorithm Optimization
Genetic algorithms are a type of optimization algorithms, meaning they are used to find the optimal solution(s) to a given computational problem that maximizes or minimizes a particular function [8] . In this paper, the proposed genetic algorithm is used as maximization function to find the best similarity score (best fitness) value between individuals as shown in Figure 2, that illustrates algorithm flowchart.
2.3. Image Compression Using Principal Component Analysis
Principal Component Analysis (PCA) is a method used in the reduction of data dimensions. Data dimensions
![]()
Figure 1. The main stages of the iris pattern recognition system by using Libor Masek algorithm.
can be reduced without much loss of information [9] . PCA formulation is used as an image compression algorithm with a low level of loss. PCA takes input gray scale image and compute the mean of it. Then computes the covariance matrix and find the eigenvectors (the principal components) and eigenvalues. The final compressed image matrix is decompressed by using the Inverse Principal Component Analysis (IPCA) as shown in Figure 3, which illustrates PCA and IPCA flowcharts.
2.4. Wireless Network
Wireless networks are cost effective and they allow computers to be mobile, cable less and communicate with speeds close to the speeds of wired Local Area Networks (LANs) [10] . In this paper, all stations are connected to router device as an infrastructure network. The connected stations communicate with each other via wired or wirelessly through router. The proposed wireless network shown in Figure 4 transmits iris image into two lines; line 1 represents compressed-decompressed iris image pattern recognition process, and line 2 represents the real iris image pattern recognition process, where PC1 is connected with PC2 and PC3 via wire to make transmission process faster, and PC2 and PC3 are connected wirelessly with PC4 and PC5 respectively.
![]()
Figure 4. Proposed wireless network hardware system.
3. Experimental Results
The system was tested by iris images taken from the CASIA database (version 1.0). The CASIA database is the most known and widely used by many researchers. In this work, the authors selected four iris images for training and three for testing of each class (108 classes).Input iris image template is compared with the stored templates to give the final decision. In mask method, the threshold (lowest hamming distance) chosen among 108 persons or classes is less than 0.3834 to make at least one image sample among each 3 testing image samples correct matched. In genetic method, the threshold (the best fitness score of the individuals in the population) chosen is higher than 0.800. To measure the performance of the iris recognition system, False Acceptance Rate (FAR), False Rejection Rate (FRR), and Correct Recognition Rate (CRR) are computed for three groups of samples as shown in Table 1, and they are expressed in the following equations,
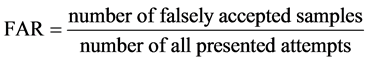 (1)
(1)
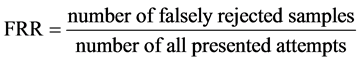 (2)
(2)
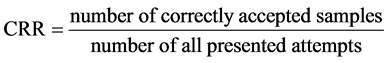 (3)
(3)
Table 1 shows that the results of the performance measurements for the two iris pattern recognition methods. The Masek algorithm has zero FAR and FRR equals to 1.33% for the first 150 samples. But when 324 samples are taken, FRR increased to 4.93% and FAR still zero. The CRR of the Masek algorithm for the 150 samples is 98.66% and decreased to 95.06% for 324 samples. In the genetic algorithm, a zero error rate and 100% recognition rate has been achieved for the first 75 samples. For the second group of samples, the FAR and FRR of the genetic algorithm are increased to 0.66% and CRR is decreased to 99.33%. When 324 samples are tested by genetic algorithm, the FAR is increased from 0.66% to 1.54% and FRR is increased from 0.66% to 2.77% and the CRR is decreased from 99.33% to 97.22%.
The system determines the type of iris recognition method used in the beginning of the network transmission in central PC (PC1). Iris image is transferred in two lines as shown in Figure 4; the first line that includes iris
![]()
Table 1. Performance results for different sample size.
![]()
Table 2. Timing results of 25 samples.
(1) Represents compressed/decompressed iris image, (2) represents real iris image.
image compression/decompression using PCA/IPCA, and the second line transfers the same input iris image. Then PC4 and PC5 will send the results of recognition back to PC1 wirelessly. All network PCs are monitored in PC1 by using Net Support School Professional version 10.70.5. The execution time for iris image recognition and network transmission time is computed for 25 samples using MATLAB version R 2015a program as shown in Table 2.
In Table 2, the average recognition time for decompressed iris image using Masek algorithm is 135.7 second, which is a lot more than the average recognition time for real iris image that equals to 11.5 second. But, the average recognition time for decompressed iris image using genetic algorithm is 9.3 second, which is larger than the average recognition time for real iris image that equals to 6.5 second. The transmission time in Line 1 involves the transmission time from PC1 to PC2 as shown in Figure 4, in addition to the time to transmit compressed image to PC4, and the time to transmit the result of decompressed iris image recognition back to PC1. And the same for the transmission time in Line 2 except that there is no compressed image transmission happens because, the same input iris image is transmitted. The transmission times for Line 1 are 24.6 second and 23.3 second for Masek and genetic methods respectively, which are a bit less than the transmission times for Line 2 that equals to 25.5 second for both methods.
4. Conclusions
In Table 1, the performance results have demonstrated that the error rate increases when the number of samples is increased and the recognition rate decreases when more samples are taken. According to CCR, the results have shown that genetic algorithm is more accurate than Masek algorithm.
The timing results in Table 2 show that the Masek algorithm takes more recognition time in average than genetic algorithm. Both methods take more time recognizing the iris image in line 1 because the image is compressed earlier in PC2 using PCA and it is recognized after decompression process using IPCA in PC4. The transmission time of line 1 is lower than line 2 because, PC2 transmits compressed iris image unlike PC3, which transmits real uncompressed iris image.
The execution time of genetic algorithm is less than the execution of Masek algorithm. This makes genetic algorithm faster, and more accurate than mask algorithm. Both methods were able to recognize decompressed iris images. The decompressed iris image makes recognition process longer than the recognition process of uncompressed real image. Compressed iris images are transferred across wireless network with less time than real images.