1. Introduction
With the large-scale proliferation of internet and network technologies, people are able to access any service from any place and at any time. Remote user authentication schemes are used to verify the legitimacy of remote user’s login request. Password-based authentication scheme is one of the convenient and efficient authentication mechanics. However, password-based authentication scheme suffers from attacks due to the low entropy password, thus designing a more secure and efficient authentication protocol is in urgent need. In 1981, Lamport proposed a remote user authentication scheme with password table [1] . Afterwards, several schemes and improvements [2] - [4] have been extensively proposed. However, most of them using the static identity (ID) are included. Since the user’s login ID is static in these verifier-free schemes, it may leak partial information about the user’s login messages so that the adversary can use it to forge the user’s login messages by some subtle means. One of the solutions to the problem is to employ dynamic ID in different login.
In 2004, Das et al. [5] proposed a dynamic ID-based remote user authentication scheme, which can resist replay, masquerade, and insider attacks. However, Wang et al. in 2009 [6] pointed out that Das et al.’s scheme is susceptible to smart card attack and does not provide mutual authentication. Then, Wang et al. proposed a more efficient and secure dynamic ID-based remote user authentication scheme. Recently, Khan et al. in 2011 [7] pointed out that Wang et al.’s scheme has insider attack and does not provide user’s anonymity and session key agreement. Then, they proposed a dynamic ID based remote user authentication scheme. We can see that these schemes have weaknesses because of using timestamps and lead to serious clock synchronization problems. In this paper, we proposed an enhanced dynamic ID-based remote user authentication scheme. In this scheme, mutual authentication is performed using a challenge-response handshake between user and server, and it avoids the problems of synchronism. Furthermore, the scheme provides user’s anonymity and session key agreement.
The remainder of this paper is organized as follows. In Section 2, we present an enhanced remote user authentication scheme. In Section 3, there is the analysis about this scheme. Finally, conclusions are presented in Section 4.
2. The Proposed Scheme
Although the implement of strict and safe time synchronization is very difficult and increases network overhead, most time synchronization schemes were not designed with security in mind. In addition, if the setting of the interval of transmission delay is too short, it will cause the failure of the legal users’ login. However, if the setting of the interval of transmission delay is too large, it will be suffered from the relay attacks. Therefore, authentication protocols based on the timestamps not only introduces more safety risk, but also is unpractical. In this section, we propose an enhanced remote user authentication scheme. To avoid the clock synchronization problem, we replace the timestamp design with a novel nonce-based mechanism in our scheme. The improved scheme is divided into four phase: registration phase, login phase, authentication phase, and password change phase. Detailed steps of these phases of the proposed scheme are described as follows. The notations used throughout this paper are in Table 1.
2.1. Registration Phase
A user Ui with identifier IDi should first carry out this phase once before he can use any of the services provided by the server S. In this phase, Ui and S need to perform the following steps.
Step R1. User Ui keys his identity IDi and password PWi, and his smart card computes and submits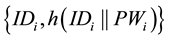 to S, through a secure channel.
to S, through a secure channel.
Step R2. After receiving the request, S computes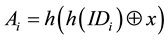 ,
, 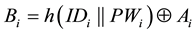 and
and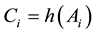 , where x is the permanent secret key of S. Then, S sends
, where x is the permanent secret key of S. Then, S sends 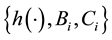 to Ui through a secure channel.
to Ui through a secure channel.
2.2. Login Phase
Whenever Ui wants to login a server S, he must perform the following steps:
Step L1. After inserting his smart card into the card reader, Ui inputs the identity IDi and password PWi. Then,
the smart card computes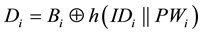 , and
, and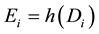 .
.
Step L2. The smart card checks whether or not Ei and Ci are equal. If yes, Ui passes the legitimate verification, and performs the following steps; otherwise, Ui is rejected.
Step L3. The smart card randomly chooses a nonce R1 and computes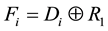 .
.
Step L4. Ui sends the login request message 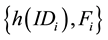 to the remote server S.
to the remote server S.
2.3. Authentication Phase
A user performs the remote authentication phase based on the login message for authentication as long as it visits the server. Ui and S perform the following steps to achieve mutual authentication and to establish a session key.
Step A1. After receiving the login message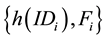 , S computes
, S computes 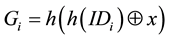 and
and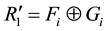 .
.
Then, S chooses a nonce R2 and computes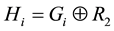 .
.
Step A2. The server S sends the mutual authentication message 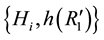 to the user Ui.
to the user Ui.
Step A3. After receiving the mutual authentication message 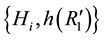 from the server S, the user Ui
from the server S, the user Ui
checks whether or not ![]() and h(R1) are equal . If no, Ui rejects this message and terminates the operation;
and h(R1) are equal . If no, Ui rejects this message and terminates the operation;
otherwise, Ui authenticates S successfully and computes![]() . Then, Ui sends
. Then, Ui sends ![]() to S.
to S.
Step A4. When the server S receives![]() , checks whether or not
, checks whether or not ![]() and h(R2) are equal. If no, S
and h(R2) are equal. If no, S
sends reject message to the Ui; otherwise, S authenticates Ui.
After finishing mutual authentication phase, the user Ui and the server S each can compute a common session
key ![]() for the next data transmission.
for the next data transmission.
2.4. Password Change Phase
The user Ui can change his password without the help of the server S, and the details of the password change procedures are as follows:
Ui inserts the smart card, and input his old password pwi and the identity IDi. Then, the smart card computes
![]() ,
, ![]() , and checks whether or not
, and checks whether or not ![]() and Ci are equal. If the verification
and Ci are equal. If the verification
process is correct, the smart card asks the cardholder to resubmit a new password![]() , and then smart card
, and then smart card
computes![]() . At last, the smart card replaces the values of Bi stored in its memory
. At last, the smart card replaces the values of Bi stored in its memory
with ![]() to finish the password change phase.
to finish the password change phase.
3. Security Analysis
In this subsection, we present these security analyses of our scheme and show that proposed scheme can resist many kinds of attack. To analyze the security of our scheme, we assume that an attacker can obtain the secret values stored in the smart card by monitoring the power consumption [8] [9] and intercept the messages communicating between the user and the server.
3.1. User Anonymity
The proposed scheme can protect user’s anonymity. In login phase, the user Ui will send the login request mes-
sage ![]() to the server S. Thus, the attacker might incept and analyze the login message. It is infeasi-
to the server S. Thus, the attacker might incept and analyze the login message. It is infeasi-
ble to derive the user identity IDi through h(IDi). Furthermore, the login message is dynamic in each login. Among the parameters of login message, Fi is associated with nonce R1 and dynamically changed. Consequently, the attacker cannot identify the person who is trying to login.
3.2. Relay Attack
The proposed scheme can resist replay attack because the login request message and the mutual authentication message both contain the nonce instead of timestamp. Suppose that the attacker has intercepted a previous login
request message ![]() from Ui, the attacker can resend the same message to S, but he can’t continue, because he can’t compute
from Ui, the attacker can resend the same message to S, but he can’t continue, because he can’t compute ![]() without knowing x and can’t compute
without knowing x and can’t compute![]() . For the same reason,
. For the same reason,
the attacker still cannot successfully impersonate the server S to cheat the users by replaying the server’s pre-
vious mutual authentication message![]() .
.
3.3. Impersonation Attack
The proposed scheme can withstand impersonation attack. Assume the attacker intercepts h(IDi), Fi, Hi, but these information has no meaning to an attacker. He can’t derive the secret parameter x and password PWi. Without R1, R2, x and PWi, the attacker can’t compute Hi, so impersonation can’t continue. What’s more, the attacker can’t impersonation of S, because he can’t compute ![]() without knowing the secret key x.
without knowing the secret key x.
3.4. Denial-of-Service Attack
In our proposed scheme, the smart card of user Ui checks the validity of user identity IDi and password PWi before update procedure. The attacker has to insert the smart card of user Ui into the smart card reader and has to
guess the identity IDi and password PWi correctly. Since the smart card computes![]() ,
,![]() , and compares the computed value of
, and compares the computed value of ![]() with the stored value of Ci in its memory to verify the le-
with the stored value of Ci in its memory to verify the le-
gitimacy of Ui before the smart card accepts the password update request. It is not possible to guess the identity IDi and password PWi correctly at the same time in real polynomial time even after getting the smart card of user Ui. Therefore, the proposed protocol is secure against DOS attacks.
3.5. Insider Attack
If an attacker obtains Bi and Ci from Ui’s smart card, he can’t extract sensitive information, like IDi, PWi, x, because it is computationally infeasible to invert the one-way hash function h(). Moreover, he can’t extract Ai from Bi without the knowledge of IDi and PWi. Furthermore, if the attacker is a legal user Ui, he can’t obtain x from his smart card. Thus, the insider attack is resisted.
3.6. Password Guessing Attack
In our scheme, Ui’s password is only involved with ![]() instead of login request message
instead of login request message ![]()
or response message![]() , it is more difficult for an attacker to compute a valid authentication request
, it is more difficult for an attacker to compute a valid authentication request
message without knowing the server’s secret value x. Therefore, we believe that the on-line password guessing attacks can be prevented more efficiently.
On the other hand, in our scheme Ui’s login message, i.e. h(IDi), Fi, are well-protected and un-involved with Ui’s password. This design eliminates the correlation between Ui’s password and the transmitted messages, i.e. h(IDi), Fi, Hi, an attacker has no ability to examine his guessed password with previous legitimate request or reply message in an off-line mode. Hence, our scheme is secure against the off-line password guessing attack.
3.7. Stolen Smart Card Attack
Our scheme can prevent stolen smart card attack. If the smart card is stolen or lost, the attacker can extract the secret information Bi and Ci from the smart card. With the parameter, the attacker tries to impersonate the user to
login to the server S, however, he must produce a valid login request message![]() . It can be observed
. It can be observed
that it is impossible to compute Ai and Fi from the given parameters without knowing x, IDi, and PWi, so the attacker can’t generate a valid login message.
3.8. Parallel Session Attack
Assume the attacker can masquerade as legitimate user Ui by replaying a login request message![]() .
.
However, he can’t compute the agreed session key ![]() between user Ui and server S because he
between user Ui and server S because he
does not know the values of x, R1, R2. Therefore, the proposed scheme is secure against parallel session attack.
3.9. Mutual Authentication
Our scheme provides mutual authentication of Ui and S. In our scheme, S sends mutual authentication message
![]() to Ui validate its authenticity. The value of Hi is calculated by Gi which is only known to Ui and S
to Ui validate its authenticity. The value of Hi is calculated by Gi which is only known to Ui and S
and this message is infeasible to forge by a fake server to impersonate the S.
3.10. Session Key Agreement
The proposed scheme provides session key agreement during the authentication phase. Suppose the attacker obtains the secret values in the legal user’s smart card and intercepts messages communicating between the user and the server, he may attempt to compute the session key SK. However, he can’t continue without knowing R1 and R2.
4. Performance Comparison
In this section, we summarize some performance issues of the proposed scheme. We compare the proposed scheme with related schemes in terms of cost and security requirements.
4.1. Cost Analysis
An efficient authentication scheme must take computation and communication cost into consideration during us- er’s authentication. The computation cost of each phase is defined as the total time of various operations executed in that phase. The communication cost of authentication includes the cost of transmitting messages involved in the authentication scheme. We mainly focus on the computations of registration, login and authentication phases since these phases are the main body of the proposed scheme.
In order to carry out the computation cost evaluation, we use the following notations: Th and Ts are defined as the execution time of the one-way hash function and symmetric operations. Because exclusive-or operation and concatenation operation require very low execution time, it is usually neglected considering its computational cost. The time complexity associated with the different operations can be expressed as T? = Th < Ts. The comparative results are shown in Table 2.
From the table, it is noticed that our scheme requires nearly the same computation as other related schemes, but our scheme provides more security.
In addition, we have shown the comparison of communication cost between our scheme and related scheme. The comparative results are shown in Table 3, we assume that the output size of secure one-way hash function is 128 bits. For comparison, we also assume that, the lengths of IDi, PWi, x, y are 128 bits, and the sizes of timestamps and random number are 64 bits.
From the table, it is noticed that the communication cost of Das et al.’s scheme is the least with 448 bits, because, it does not support mutual authentication. However, our scheme needs less bits than others.
4.2. Security Requirements Analysis
In this section, we summarize the security features of our proposed scheme and compare its security robustness with related schemes. The comparative results are shown in Table 4.
From the table, it is noticed that our scheme is more secure and robust than other schemes and achieves more security requirements, which were not considered in the their scheme and are essentially required in implementing a practical and universal remote user authentication scheme using smart cards.
5. Conclusions
In this paper, we see that several dynamic user authentication schemes have weaknesses because of using timestamps. Besides, the implement of strict and safe time synchronization is very difficult and increases network overhead. To eliminate these weaknesses, we propose a new dynamic user authentication scheme based on
![]()
Table 2. Computation cost comparison.
![]()
Table 3. Communication cost comparison.
![]()
Table 4. Security properties comparison.
S1: Resist impersonation attack; S2: Resist DOS attack; S3: Resist insider attack; S4: Resist replay attack; S5: Resist password guessing attack; S6: Resist stolen smart card attack S7: Resist Parallel session attack; S8: Provide user’s anonymity; S9: Provide mutual authentication; S10: Provide session key agreement.
nonce instead of timestamps. Mutual authentication is performed using a challenge-response handshake between user and remote server. Moreover, our scheme uses hashing functions to implement user’s anonymity and session key agreement. The other merits include: 1) our scheme provides a secure password change method to prevent the adversary from updating password freely; 2) our scheme can resist various attack, including forward se- crecy; 3) our scheme requires less computation and communication traffic; 4) it is a nonce-based scheme to avoid the time-synchronization problem.
Therefore, this scheme is well suited to the network-based application systems. In our future work, we would carry on experiments if the conditions are met.
Acknowledgements
Yang Xiaohui, Cui Xinchun, Cao Zhenliang and Hu Ziqiang thank the anonymous reviewers for their valuable comments and suggestions.