Research on Embedding Capacity and Efficiency of Information Hiding Based on Digital Images ()
1. Introduction
The protection of digital data, especially for confidential data, becomes more and more important. As a kind of data security technique, digital steganography has been developed rapidly and attracts a great deal of attention from both the industrial and academic communities [1-15].
Digital steganography based on images is a way of hiding the existence of secret message under the cover of a carrier signal in such a way that no one apart from the sender and intended recipient even realizes there is a hidden message. An original image, used to carry secret message as a carrier signal, is called the cover image. And an image which has carried secret message is called the stego image. By virtue of generating stego images that are perceptually identical to the cover images with small embedding distortion, the secret messages are embedded into cover images.
The desires of good steganographic schemes are high embedding efficiency and security as well as large embedding payload. A steganographic scheme with low image distortion is more secure than that with high distortion because it does not raise any suspicion of adversaries. A steganographic scheme with high payload is expected because more secret messages can be transmitted. A steganographic scheme with high security can be powerful to resist the attacks by the steganalysis. However, the three factors are irreconcilable conflict. Therefore, we often make a compromise among them depending on different application requirements. A commonly used method, called the LSB (i.e. least significant bits) replacement method, is a simple hiding method by modifying the LSB of cover pixels to embed secret data [3-6]. However, it is easy to be detected. To improve the embedding efficiency, the (7,4) Hamming Code method is introduced into the steganographic schemes [1,11,13- 15]. The WPC (i.e. wet paper codes) schemes [7,13,14], not only achieving high embedding efficiency but also providing a non-shared selection channel, are also proposed. On the contrary, some other hiding methods are utilized to the steganographic schemes so as to achieve large embedding payload [2,10-12,15-18]. Specifically, the embedding payload of the scheme proposed in [11] is close to 1 bpp. And a hiding scheme called “Hamming + 1” was proposed by Zhang et al. [9], for the purpose of improving the embedding capacity.
For the current information hiding schemes, the improvement of the embedding capacity and the embedding efficiency is still the goal that we pursuit and the starting point that we consider as to improve the algorithms. Considering the advantages and disadvantages of the previous methods, the paper proposed two algorithms for information hiding, one is high capacity of information hiding algorithm (HCIH algorithm), and the other is high quality of information hiding algorithm (HQIH algorithm).
On the one hand, considering the performance standard of embedding capacity, we present a high capacity of information hiding algorithm (HCIH algorithm), based on the (7,4) Hamming Code and the LSB replacement method, and inspiring from the “Hamming + 1” method. The HCIH algorithm can be used to embed an email address as the secret message into an 8-bit gray-scale image, and achieves to embed twelve secret bits of the binary string of the secret message, which is converted from an email address, into a block of cover pixels of a cover image sized each time. Then we evaluate the validity of HCIH algorithm through experimental simulation. The experimental results show that our proposed HCIH algorithm achieves high embedding capacity (i.e. 0.75 bpp) and acceptable visual quality of the stego image, and can be used for the applications about large payload secret message transmission.
On the other hand, considering the performance standard of embedding efficiency, we present a high quality of information hiding algorithm (HQIH algorithm), by introducing wet paper codes technology, for the purpose of improving the embedding efficiency. Considering that the embedding capacity may be lower because of introducing wet paper codes technology, when the embedding operation fails first time, the HQIH algorithm may try the second embedding operation to embed again by (7,4) Hamming Code oriented wet paper codes, to assure the embedding capacity. Meanwhile, the double operation also achieves higher security. Then, we evaluate the validity of HCIH algorithm through experimental simulation. The simulation experiments show that the HQIH algorithm achieves high embedding efficiency, that is the value of PSNR [19,20] is more than 52 dB, and large embedding payload, that is the value of ER is between 0.5499 bpp and 0.8291 bpp, which can be used for different applications. Specially, our HQIH algorithm gives some degree of security by considering twofold safeguards.
In short, considering the improvement of the embedding capacity and the embedding efficiency, this paper mainly studies on the information hiding technology based on gray-scale digital images and proposes two algorithms with detailed procedures and effective simulation experiments.
2. HCIH Algorithm
On this part, considering the performance standard of embedding capacity, we present a high capacity of information hiding algorithm (HCIH algorithm), based on the (7,4) Hamming Code and the LSB replacement method, and inspiring from the “Hamming + 1” method. The HCIH algorithm can be used to embed an email address as the secret message into an 8-bit gray-scale image, and achieves to embed twelve secret bits of the binary string of the secret message, which is converted from an email address, into a block of 4 × 4 cover pixels of a cover image sized 512 × 512 each time. The date embedding phase and data extracting phase are described in the following sections 2.1 and 2.2 respectively.
2.1. The Data Embedding Phase
Step 1: Give a cover image I sized 512 × 512 pixels as the carrier and an email address as the secret message needed to be embedded.
Step 2: Convert the email address into binary string S of l bits by the ASCII code, denoted as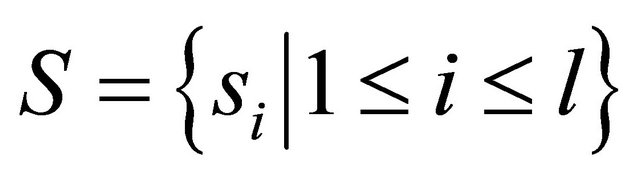 , where
, where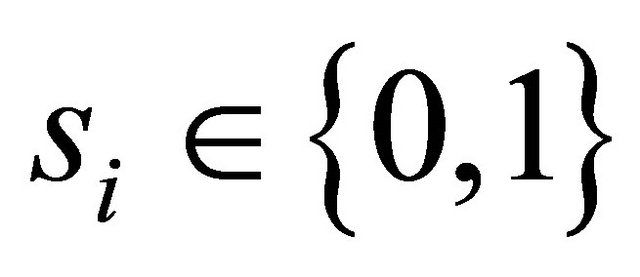 . And then divide it into non-overlapping partitions of twelve secret bits, denoted as
. And then divide it into non-overlapping partitions of twelve secret bits, denoted as  , where
, where 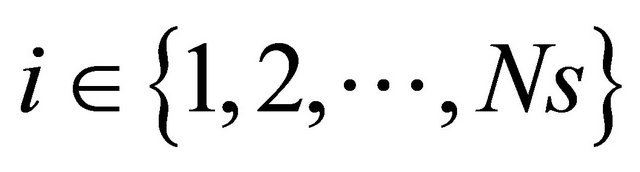 and Ns is the total number of the partitions.
and Ns is the total number of the partitions.
Step 3: Segment the cover image I into 128 × 128 blocks of 4 × 4 cover pixels, denoted as
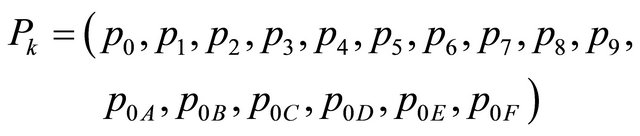 where
where
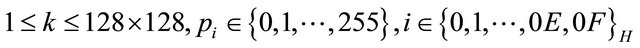
Step 4: Embed the first three bits 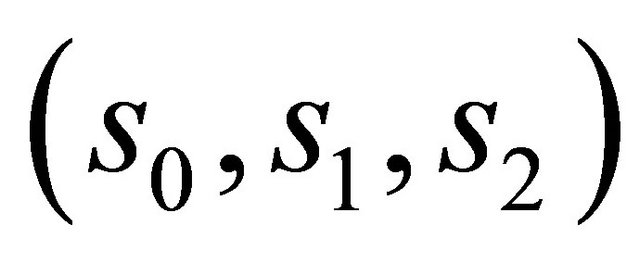 of si into the first seven cover pixels
of si into the first seven cover pixels  of block Pi by the (7,4) Hamming code and the LSB replacement method. And generate the first seven stego pixels
of block Pi by the (7,4) Hamming code and the LSB replacement method. And generate the first seven stego pixels 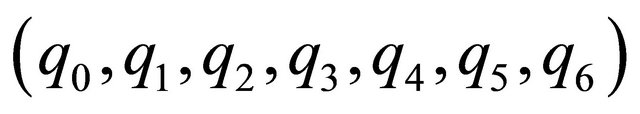 of the stego block Qi.
of the stego block Qi.
Step 5: Embed the secret bits sh into the cover pixel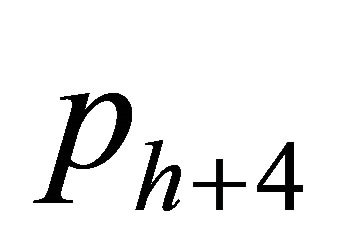 , where
, where 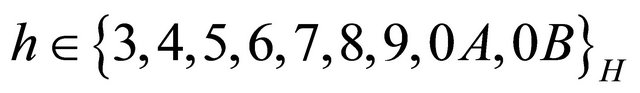 by taking the operation in (1).
by taking the operation in (1).
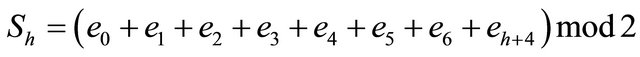 (1)
(1)
where ej is the 2nd-rightmost LSB of pj , where  and
and 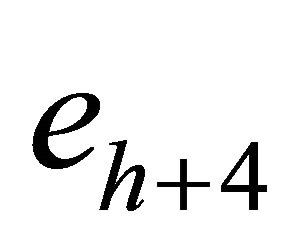 is the 1st-rightmost LSB of
is the 1st-rightmost LSB of , where
, where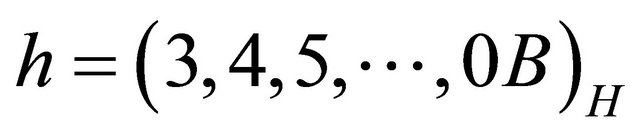 . If (1) holds, embed Sh with
. If (1) holds, embed Sh with  unchanged; If (1) does not hold, modify the value of
unchanged; If (1) does not hold, modify the value of 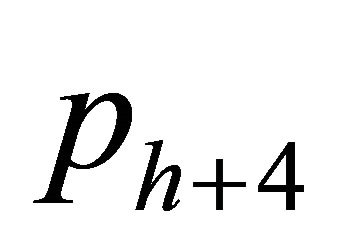 by taking the opposite of the 1st-rightmost LSB
by taking the opposite of the 1st-rightmost LSB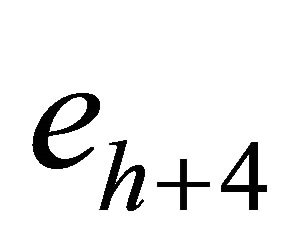 , to make (1) hold. At last, we embed sh and obtain the stego pixel
, to make (1) hold. At last, we embed sh and obtain the stego pixel  of the stego block Qi.
of the stego block Qi.
Step 6: Repeat Step 4 to Step 5 until all the secret bits are embedded and generate the stego image .
.
Figure 1 shows the block diagrams of the proposed data embedding phase.
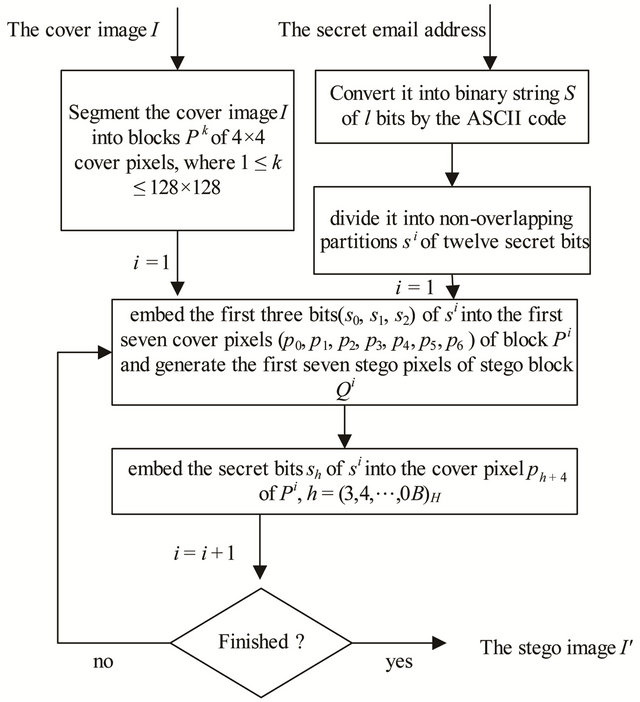
Figure 1. The block diagrams about the data embedding phase of HCIH algorithm.
2.2. The Data Extracting Phase
The receiver can extract the secret message S from the received stego image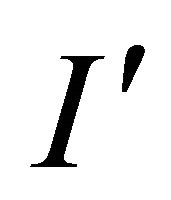 . The detailed steps are as follows:
. The detailed steps are as follows:
Step 1: Segment the stego image 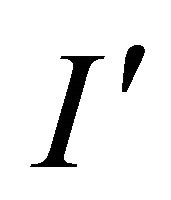 into 128 × 128 blocks of 4 × 4 stego pixels, denoted as
into 128 × 128 blocks of 4 × 4 stego pixels, denoted as
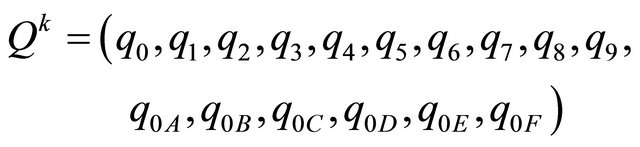 where
where
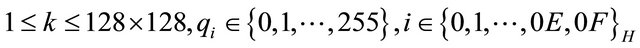 .
.
Step 2: Extract the first three bits 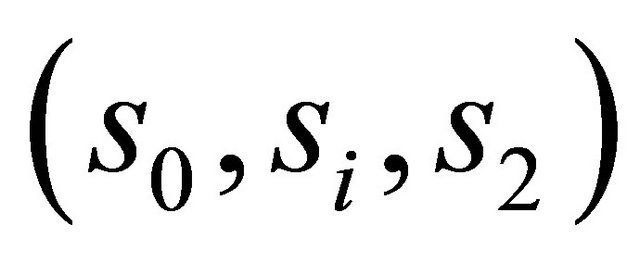 of si from the first seven stego pixels
of si from the first seven stego pixels 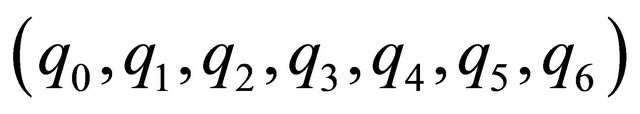 of block
of block  by (7,4) Hamming code and the LSB replacement method.
by (7,4) Hamming code and the LSB replacement method.
Step 3: Extract sh from the stego pixel  by taking the operation in (2).
by taking the operation in (2).
 (2)
(2)
fj is the 2nd-rightmost LSB of 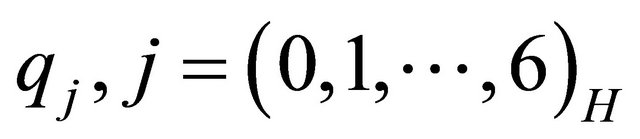 and fh+4 is the 1st-rightmost LSB of
and fh+4 is the 1st-rightmost LSB of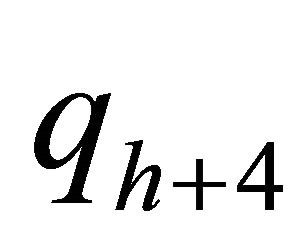 ,
, .
.
Step 4: Repeat Steps 2 and 3 until all the secret bits of the secret binary string are extracted.
Step 5: Convert the secret binary string into its original email address by the ASCII code.
Figure 2 shows the block diagrams of the proposed data extracting phase.
3. HQIH Algorithm
On this part, considering the performance standard of
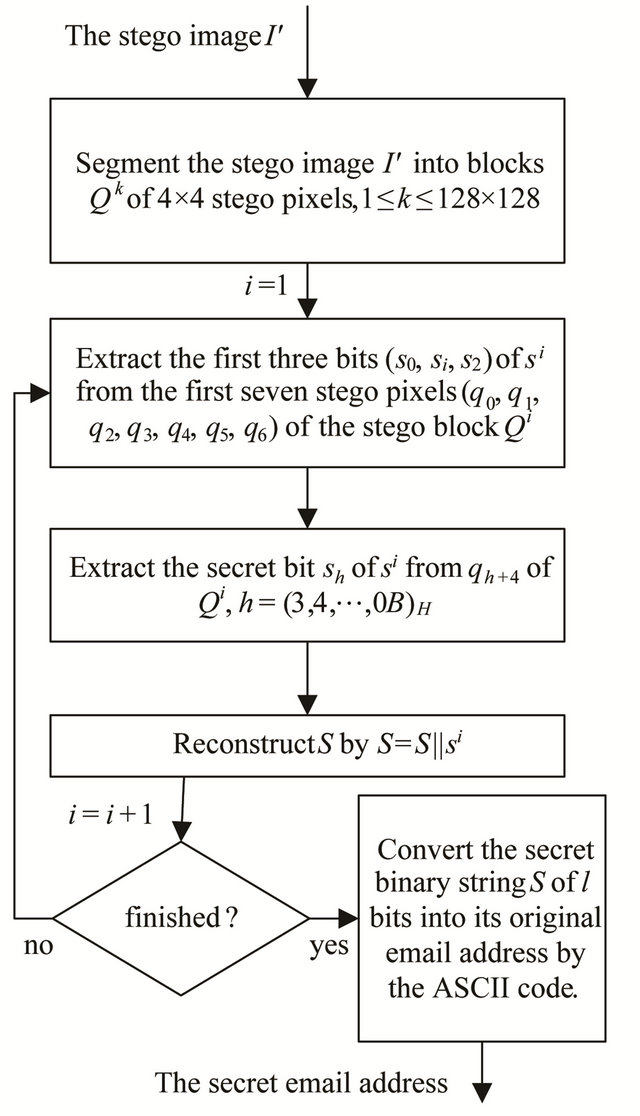
Figure 2. The block diagrams about the data extracting phase of HCIH algorithm.
embedding efficiency, we present a high quality of information hiding algorithm (HQIH algorithm), by introducing wet paper codes technology, for the purpose of improving the embedding efficiency. Considering that the embedding capacity may be lower because of introducing wet paper codes technology, when the embedding operation fails first time, the HQIH algorithm may try the second embedding operation to embed again by (7,4) Hamming Code oriented wet paper codes, to assure the embedding capacity. Meanwhile, the double operation also achieves higher security.
The main idea of the HQIH algorithm is as follows: Firstly, give an 8-bit gray-scale image as the cover image and the binary secret message need to be embedded. Secondly, segment the given cover image into non-overlapping pixel-groups, each pixel-group contains seven pixels, among which there may be some wet pixels (i.e. unchangeable pixels). Thirdly, after weighing the methods described above, we try to embed the first seven secret bits into the first pixel-group of seven pixels. If none of the wet pixels of the first pixel-group are modified during the embedding, the embedding operation is successful and the instruction array we have set flag . If not, we try to embed the first three secret bits into the first pixel-group of seven pixels, if none of the wet pixels are altered this time, the embedding operation is successful and flag
. If not, we try to embed the first three secret bits into the first pixel-group of seven pixels, if none of the wet pixels are altered this time, the embedding operation is successful and flag , if not, flag
, if not, flag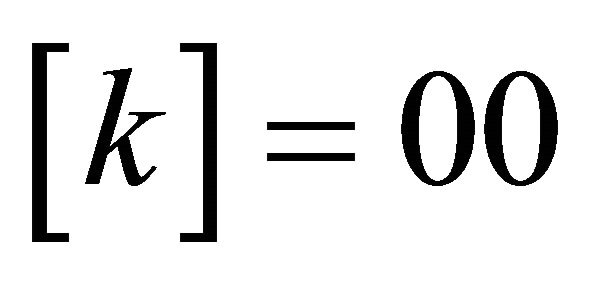 , that isthe operation of embedding secret bits into the first pixelgroup fails. So we try to embed the secret bits into the next pixel-group in the same way. Until all the secret bits are embedded, we can get the stego image I' and the instruction array flag at last.
, that isthe operation of embedding secret bits into the first pixelgroup fails. So we try to embed the secret bits into the next pixel-group in the same way. Until all the secret bits are embedded, we can get the stego image I' and the instruction array flag at last.
The date embedding phase and the data extracting phase are described in the following sections 3.1 and 3.2 respectively.
3.1. The Data Embedding Phase
A cover image I sized 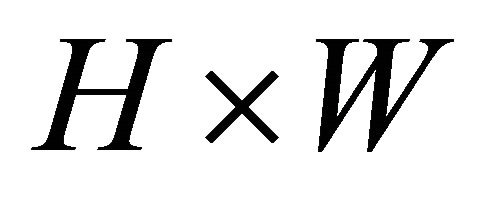 pixels is given as the carrier and the binary secret message need to be embedded.
pixels is given as the carrier and the binary secret message need to be embedded.
Initialization: Set an index i = 0, to indicate the secret bit; Set an instruction array flag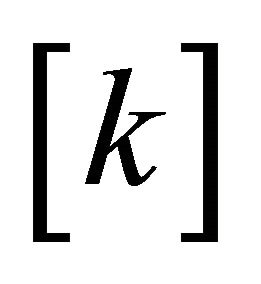 , to indicate the embedding.
, to indicate the embedding.
Step 1: Segment the given cover image I sized H×W into x non-overlapping pixel-groups, denoted as Qk. Each pixel-group contains seven pixels, among which there may be some wet pixels by any possibility, denoted as
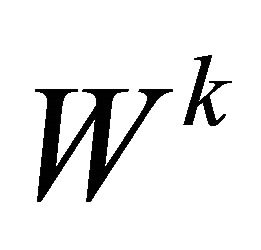
 is one of the subsets of
is one of the subsets of  .
.
Step 2: From i, read the first seven bits of the binary secret message S, denoted as .
.
Step 3: Read one pixel-group Qk of seven pixels, and calculate the LSB of Qk, denoted as  .
.
Step 4: Calculate the decimal value a of bits 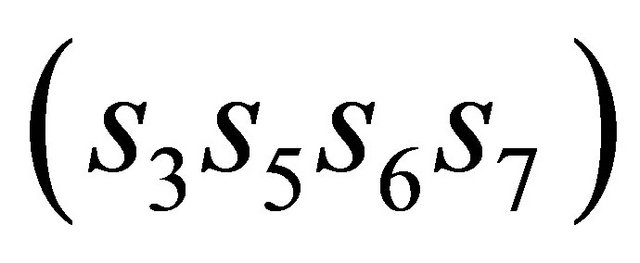 and the decimal value b of bits
and the decimal value b of bits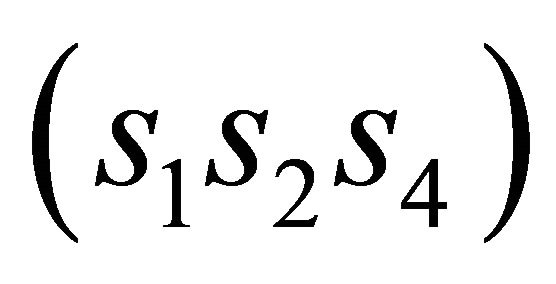 . If
. If , where ⊕ is the bitwise exclusive-or operation, and
, where ⊕ is the bitwise exclusive-or operation, and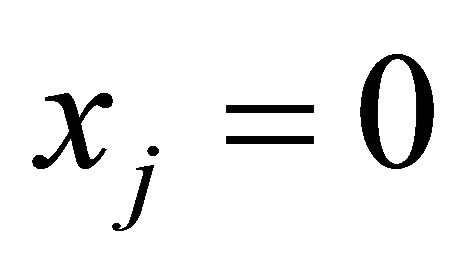 , where
, where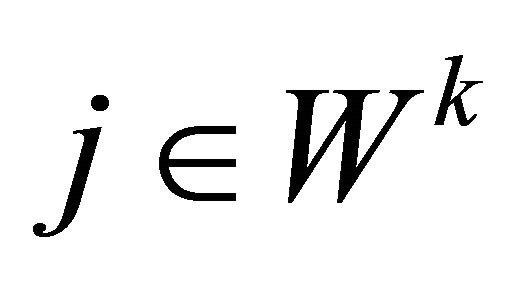 , we replace Ck with
, we replace Ck with , and
, and 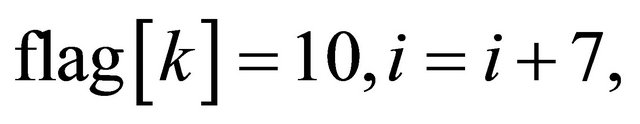 then go to Step 2; if
then go to Step 2; if , where
, where , then go to Step 5.
, then go to Step 5.
Step 5: Calculate the decimal value u of the first three bits  and compare the values between
and compare the values between  and Ck from v = 0 to 15 in group
and Ck from v = 0 to 15 in group . If
. If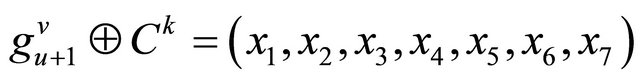 , where ⊕ is the bitwise exclusive-or operation, and
, where ⊕ is the bitwise exclusive-or operation, and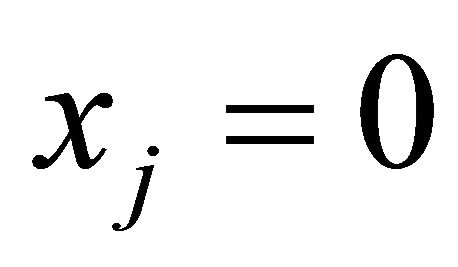 , where
, where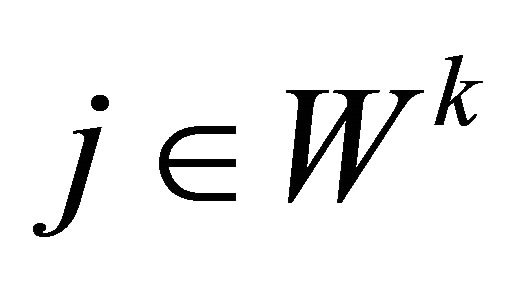 , we replace Ck with
, we replace Ck with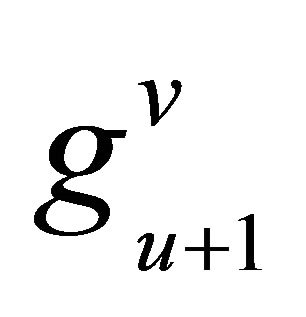 , and
, and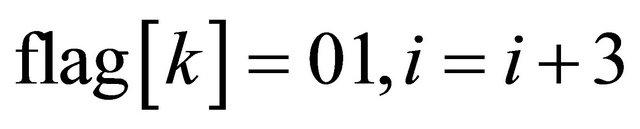 , then go to Step 2; if
, then go to Step 2; if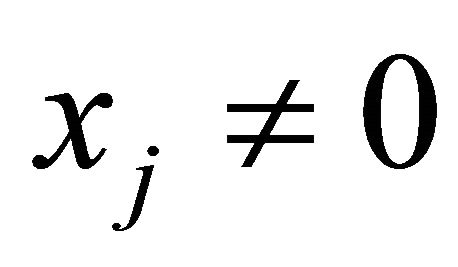 , where
, where ,
,  , that is, the embedding operation fails. Go to Step 3 to try the next pixel-group
, that is, the embedding operation fails. Go to Step 3 to try the next pixel-group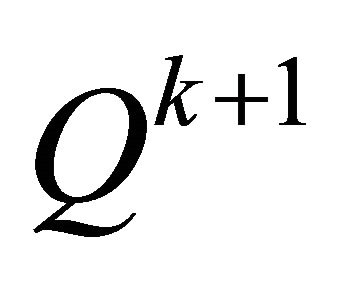 .
.
At last, we can obtain the stego image I' when all the secret bits are embedded. Figure 3 gives the block diagrams of the data embedding phase.
3.2. The Data Extracting Phase
The receiver can extract the secret message S from the received stego image I' with the help of the pre-shared instruction array flag between the sender and the receiver. The detailed steps are narrated as follows.
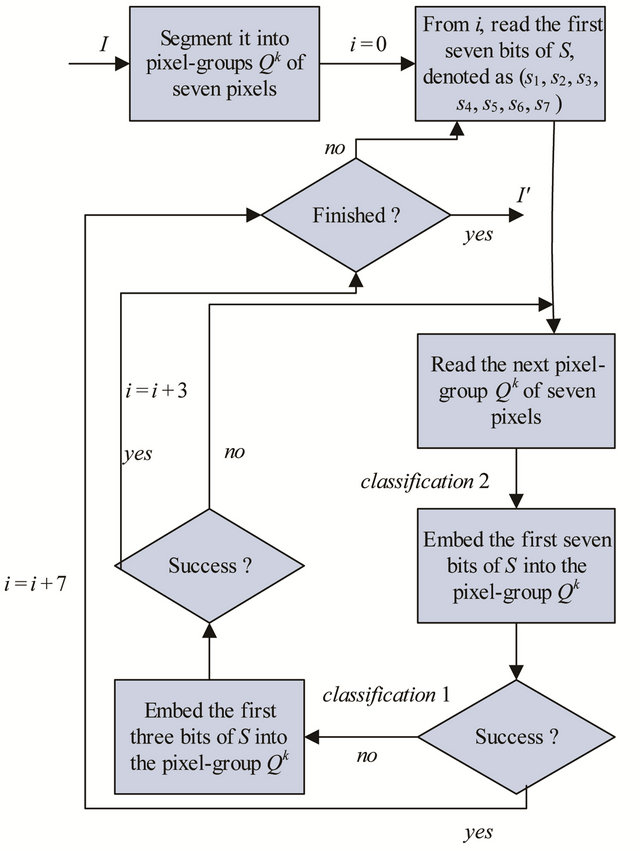
Figure 3. The block diagrams about the data embedding phase of HQIH algorithm.
Step 1: Segment the received stego image I' sized H × W pixels into x non-overlapping pixel-groups, denoted as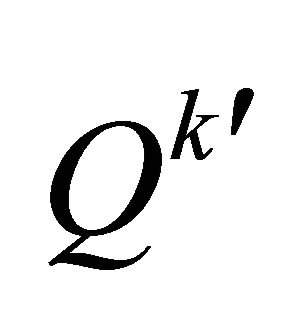 . Each pixel-group contains seven pixels.
. Each pixel-group contains seven pixels.
Step 2: Read the next pixel-group  of seven pixels:
of seven pixels:
If , no secret bits are embedded into
, no secret bits are embedded into , go to Step 2;
, go to Step 2;
If , calculate the LSB of
, calculate the LSB of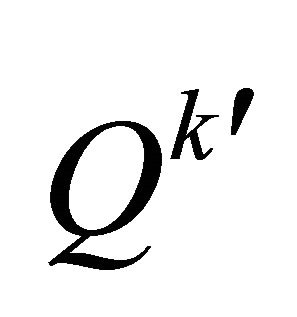 , denoted as
, denoted as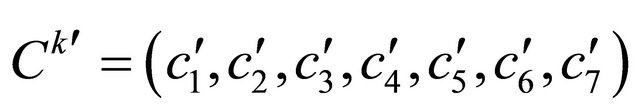 , compute
, compute
 and reconstruct S by
and reconstruct S by where || denotes the concatenation operation, then go to Step 2;
where || denotes the concatenation operation, then go to Step 2;
If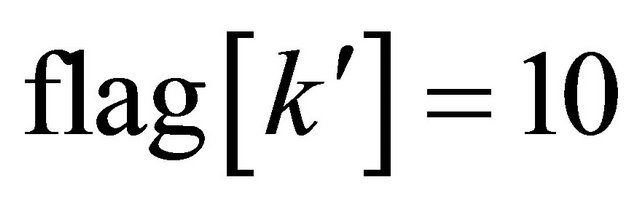 , calculate the LSB of
, calculate the LSB of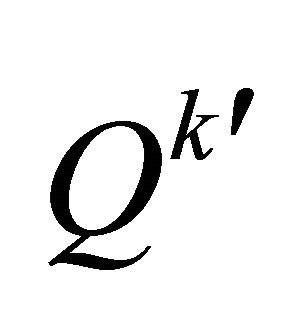 , denoted as
, denoted as , compute
, compute
 , and extract the next partition s of seven secret bits
, and extract the next partition s of seven secret bits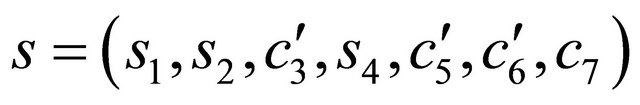 . Reconstruct S by
. Reconstruct S by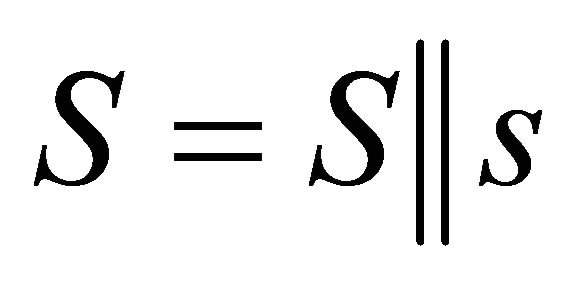 , where || denotes the concatenation operation, then go to Step 2.
, where || denotes the concatenation operation, then go to Step 2.
At last, we can extract all the secret bits and the block diagrams of the data extracting phase are shown in Figure 4.
4. Experimental Results and Discussions
As is well-known, high embedding efficiency and high
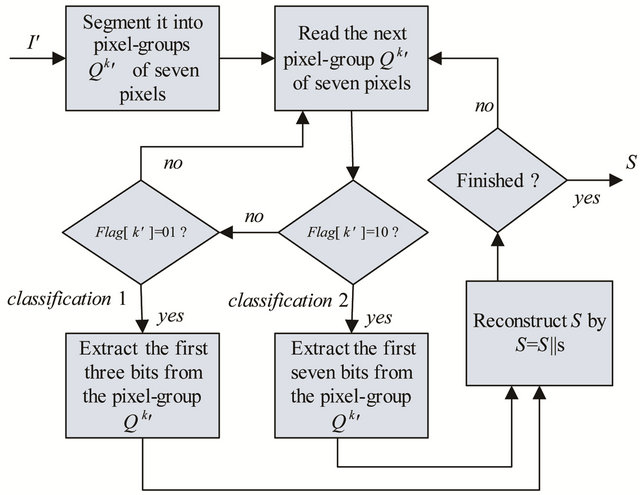
Figure 4. The block diagrams about the data extracting phase of HQIH algorithm.
embedding payload are the primary goal of a good steganographic scheme. So, correspondingly, there are two important evaluation criterions to measure the performance of a steganographic scheme, one is the embedding efficiency of the stego image, and the other is the embedding payload of the cover image.
For embedding efficiency, also called embedding quality or visual quality of the stego image, in order to avoid a subjective evaluation by the human naked eyes, a wellknown measurement, namely peak-signal-to-noise-r-ate (PSNR for short), is used to evaluate the degree of similarity between a stego image and its original image. PSNR is defined as following equation in (3).
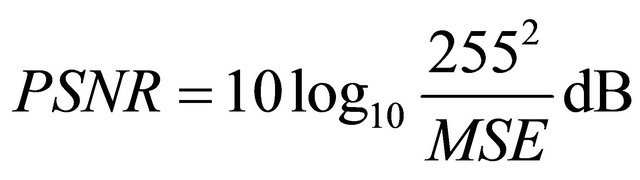 (3)
(3)
Here, MSE, being short for the mean square error, represents the difference between the stego image and its original image sized H × W pixels. The MSE is defined as in (4).
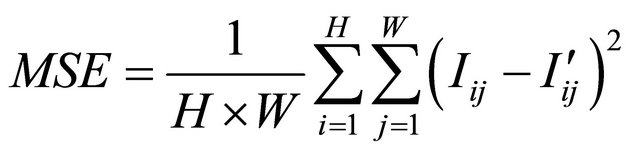 (4)
(4)
According to the visual quality evaluation, a high value of PSNR means that a stego image is very similar to its original image and the embedding efficiency of the steganographic scheme is high. In contrast, a low value of PSNR means that a stego image has visible and sensible distortion with its original image and the embedding efficiency is low. Generally speaking, if the value of PSNR is higher than 30 dB, it is hard to distinguish the distortion by human eyes.
For embedding payload, also called embedding capacity, we use ER, being short for embedding rate, to represent the percentage of the embedded secret bits in the whole pixels of the cover image. The ER is defined as in (5).
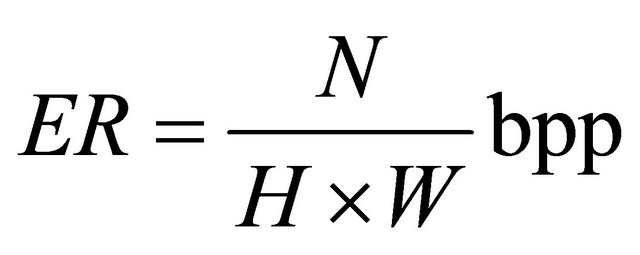 (5)
(5)
Here, N is the total number of the embedded secret bits and H × W is the size of the carrier. According to the embedding payload evaluation, a large value of ER represents that the steganographic scheme has better performance in terms of the embedding payload, that is, a cover pixel in the cover image can carry more secret bits. On the contrary, a small value of ER represents a worse performance.
In order to evaluate the performance of HCIH algorithm, nine commonly-used gray-scale images sized 512 × 512 pixels were used to simulate the experiments as shown in Figure 5.
By using MATLAB 7.0 software, we simulated the procedure of the HCIH algorithm.
Figure 6 shows the visual quality of the stego images generated by the proposed method when .
.
Table 1 compares the results of the performance between HCIH algorithm and other methods, such as Matrix coding and the “Hamming + 1” method.

Figure 5. The nine commonly-used gray-scale images.

Figure 6. The visual quality of the stego images generated by HCIH algorithm with ER = 0.75 (bpp).
Table 1. The comparison results between HCIH algorithm and others.
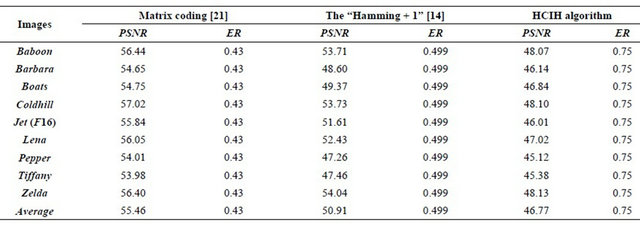
From the Figure 6 and the Table 1, we can see that the proposed method achieved high embedding capacity (0.75 bpp) with acceptable visual quality (i.e. the PSNR value is higher than 45 dB).
Figure 7 compares the embedding rate of Matrix coding, “Hamming+1” and HCIH algorithm and shows that the proposed HCIH algorithm achieves higher embedding rate, that is higher embedding capacity. Figure 8 gives the PSNR of different stego images generated by HCIH algorithm and shows that the average value of PSNR is higher than 46 dB. According to the embedding efficiency evaluation, HCIH algorithm also achieves acceptable visual quality.
By using MATLAB 7.0 software, we simulated the procedure of the HQIH algorithm. In our simulation experiments, we chose 4 different wet rates (i.e. the values of WR is from 0.1 to 0.4) for each test image, in order to assure high accuracy of the experimental results. Meanwhile, we randomly generated 10 different wet maps for each WR, each map had different distribution of the wet pixels, and also generated 10 different binary strings of the same size as the different secret data. Based on the experimental data mentioned above, cyclic-cross tests were adopted. Ultimately, the average of all the values except for the maximum and the minimum was considered as the experimental results.
Table 2 in the following gives the results of the simulation experiments when WR is from 0.1 to 0.4. As is shown, the average value of PSNR is higher than 52 dB. For the visual quality evaluation, the stego image which carried the secret data is greatly similar to its original image and it is hard to distinguish the difference by human naked eyes. Thus, the HQIH algorithm of information hiding achieves higher embedding efficiency, that is, the stego image has better visual quality.
Table 2 also illustrates the results of ER. The values of ER decrease with the increase of WR and it can achieve 0.55 bpp at least and 0.83 bpp at most.
Figure 9 gives the embedding rate of different images with different wet rates, the value of which is from 0.1 to 0.4 and shows that the embedding rate rises with the decrease of WR. Figure 10 compares the embedding rate of Matrix coding, “Hamming + 1”, HCIH algorithm and HQIH algorithm (with WR = 0.1). We can find that the HQIH algorithm can achieve higher embedding capacity than others.