Practical Security of the Continuous-Variable Quantum Key Distribution with Locally-Generated Local Oscillators ()
1. Introduction
Continuous-variable quantum key distribution (CVQKD) allows two remote participants to establish a common key through an insecure quantum channel [1]. The CVQKD scheme using Gaussian-modulated coherent state (GMCS) is the most favorable one due to its optimal transmission rate under the Gaussian noise channel and its excellent compatibility with the standard optical equipments [2]. So far, the GMCS scheme has been theoretically proven to be unconditionally secure against collective attacks and coherent attacks [3] [4]. Meanwhile, some experiments have demonstrated its availability over long distance [5] [6].
In the traditional GMCS-CVQKD experiments, the local oscillator (LO) needs to be transmitted from the sender Alice to the receiver Bob over the insecure quantum channel for the homodyne detection at Bob’s side. However, the LO transmission brings secure issues quickly. The LO transmitted in the insecure quantum channel is most likely to be controlled and manipulated by eavesdroppers who may cause practical attacks on GMCS-CVQKD system, such as the LO fluctuation attack [7], the wavelength attack [8] and the saturation attack [9]. Although some solutions have been proposed to enhance the security of practical systems [10] [11] [12] [13], it is difficult to protect practical systems against all the potential loopholes caused by the LO transmission have been discovered.
Recently, in order to completely solve those loopholes caused by the LO transmission, several researchers adopt the local LO (LLO) scheme that the LO is generated locally at Bob’s side, while the reference pulses are transmitted instead of the LO pulses to ensure the reliability of coherent detection [14] [15] [16]. The local LO is absolutely controlled by Bob so that the shot-noise-limited coherent detection becomes secure and the high-speed homodyne detection can be achieved. Moreover, the reference pulses provide phase information for Bob’s coherent detection, so that the phase drift between Alice and Bob can be compensated exactly in real time. Besides, the reference pulses can be transmitted with quantum signals over the same quantum channel by time-multiplexing and polarization-multiplexing [17] [18], so that it is easy for practical systems to separate them.
However, while the issues caused by the LO transmission are eliminated in the LLO-CVQKD system, the reference pulses may open new loopholes at the same time. The role of reference pulses is to provide reliable phase information for phase compensation at Bob’s side, but reference pulses are also confronted with the potential threats in the insecure quantum channel. If these reference pulses are manipulated by eavesdroppers, the phase information carried by them will become unreliable, and the phase compensation during Bob’s coherent detection will become imperfect. As a result, the security of the practical LLO-CVQKD system will be reduced due to the imperfect phase compensation [19] [20].
In this paper, we present a type of phase attack on reference pulses in the LLO-CVQKD system with time-multiplexing. Under this phase attack, the phase noise of reference pulses can be easily manipulated by eavesdroppers, and then the phase compensation error is increased. The practical security of the LLO-CVQKD scheme under the phase attack is analyzed based on the noise model of imperfect phase compensation. The simulation results show that the practical security is reduced but it is still tight when the phase attack is present.
2. Theoretical Analysis
2.1. System Description
The practical LLO-CVQKD system using time-multiplexing is depicted in Figure 1. The sender Alice uses a commercial laser to generate a set of optical pulses, which are split by a beam splitter (BS) into the signal path and the reference path. In the signal path, the optical pulses are modulated by an amplitude modulator (AM) and a phase modulator (PM), and then the quantum signal pulses of Gaussian-modulated coherent states are generated, in which the quadratures
and
are two independent random variables with Gaussian distribution
, where
denotes the modulation variance. In the reference path, the reference pulses with source phase information
are delayed by a delay line and then they are multiplexed with the quantum signals in time-domain. Then, both the signal pulses and reference pulses are sent to the receiver Bob through a quantum channel with transmittance T and excess noise
, where the total channel-added noise referred to the channel input is expressed in shot noise units as
.
At Bob’s side, the received pulses are split into reference path and signal path by time-demultiplexing. In the reference path, the phase values of the reference pulses are measured by a heterodyne detector and they are used to modify the phase of LO generated locally at Bob’s side. In the signal path, the quantum signals are detected by a homodyne detector with the local LO, where the phase drift is compensated, so that the quadrature X or quadrature P of a coherent state can be measured exactly according to Bob’s random selection of measurement basis. For a practical homodyne detector of detection efficiency
and electronic noise variance
, the detection noise referred to Bob’s input is expressed in shot noise units as
. Thus, the total noise referred to the channel input can be expressed as
.
![]()
Figure 1. The phase attack on reference pulses of the LLO-CVQKD system with time-multiplexing (BS: beam splitter, LO: local oscillator).
2.2. Phase Attack
In the LLO-CVQKD system with time-multiplexing, the reference pulses are located uniformly among signal pulses, where the reference pulses and signal pulses are transmitted alternately one by one. This simple multiplexing pattern enables Bob to demultiplex the signal pulses and reference pulses precisely. While this multiplexing pattern is employed by Alice and Bob, it is reasonable to assume that the eavesdropper Eve also knows this pattern.
For the signal pulses and reference pulses transmitted into quantum channel, Eve can easily split these pluses into signal path and reference path according to the multiplexing pattern (see Figure 1). In the signal path, the signal pulses are stored by quantum memories for being resent later. In the reference path, the reference phase of Alice’s reference pulse is measured by a phase detector, and then a forged reference pulse is produced where an additional phase noise is introduced. After being multiplexed, the signal pulses and the forged reference pulses are transmitted to Bob. At Bob’s side, the phase drift of a quantum signal is estimated by the adjacent reference pulse, so that the phase compensation error can be written as:
(1)
where
and
are the phase drifts for a quantum signal and its following reference pulse, and
is the additional phase noise caused by Eve’s phase attack. Assuming that the phase drifts of quantum signals can be can be compensated by reference pulses, namely
, the additional phase noise is left and then it leads to the imperfect phase compensation. Furthermore, assuming that this phase noise is zero-mean and with variance
, the deviation of the actual phase compensation error can be given by
(2)
2.3. Security Analysis
The security analyses of the traditional GMCS-CVQKD scheme with the imperfect phase compensation have been analyzed in the existing researches [19] [20]. Here, we utilize the noise model of imperfect phase compensation for GMCS-CVQKD to analyze the practical security of LLO-CVQKD scheme.
For the LLO-CVQKD scheme with imperfect phase compensation, the Gaussian modulated coherent states are transmitted from Alice to Bob over a quantum channel with transmittance T and excess noise
. At Bob’s side, The phase compensation error
leads to a random phase rotation between the modulated coherent state
and the measured one
. Therefore, the measurement results can be expressed as
(3)
(4)
where
and
are Gaussian noises with variance
for quadrature X and P respectively. In the noise model of imperfect phase compensation, it is assumed that the phase compensation error
is zero-mean, so that the covariance matrix of the mixture state
shared by Alice and Bob can be given by
(5)
where
is a second-order identity matrix,
and
. The parameter
denotes the actual transmittance, and the parameter
denotes the actual total noise referred to the channel input. On the one hand, due to the imperfect phase compensation, the actual transmittance can be expressed as
(6)
where
denotes the phase compensation accuracy which will be introduced in detail later. On the other hand, the actual total noise can be given by
(7)
where
is the actual total channel-added noise referred to the channel input, and
is the actual excess noise given by
(8)
For the CVQKD with imperfect phase compensation, the parameters
and
are closely related to the phase compensation accuracy
which can be expressed as
(9)
where
denotes the expectation of a random variable x. When the phase compensation error
is smaller than 5 degrees, the Taylor approximation
can be achieved, so that the phase compensation accuracy can be approximated as
(10)
where
is the deviation of phase compensation error that has been introduced in Equation (2).
In the case of reverse reconciliation, the secret key rate of the CVQKD system under collective attack is calculated asymptotically as
(11)
where
is the reconciliation efficiency,
is the Shannon mutual information between Alice and Bob, and
is the Holevo bound that defines the maximum information available to Eve on Bob’s secret information. For the homodyne detection employed by Bob, the Shannon mutual information is given by
(12)
The Holevo bound can be derived from the covariance matrix
shown in Equation (5) and then it is calculated as
(13)
where
, and
are given by
(14)
(15)
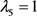 (16)
(16)
with symbols defined as
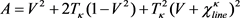 (17)
(17)
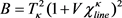 (18)
(18)
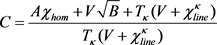 (19)
(19)
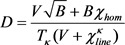 (20)
(20)
2.4. Parameters Estimation
For the practical LLO-CVQKD system, the actual transmittance 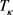 and the actual excess noise
and the actual excess noise 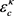 should be estimated by training signals which are randomly selected from the received quantum signals at Bob’s side. It is supposed that Bob randomly selects M quantum signals for training, and then the quadrature measurements of them are denoted as
should be estimated by training signals which are randomly selected from the received quantum signals at Bob’s side. It is supposed that Bob randomly selects M quantum signals for training, and then the quadrature measurements of them are denoted as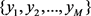 . Also, the modulated quadratures of them, denoted as
. Also, the modulated quadratures of them, denoted as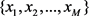 , are announced by Alice via a classical channel. According to the training signals, Alice and Bob would estimate the actual transmittance and the actual excess noise such as
, are announced by Alice via a classical channel. According to the training signals, Alice and Bob would estimate the actual transmittance and the actual excess noise such as
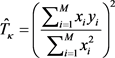 (21)
(21)
and
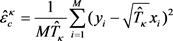 (22)
(22)
Statistically, the expectations of the estimated parameters are consistent with the theoretical ones as 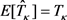 and
and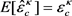 , so that the practical secret key rate for the LLO-CVQKD under collective attacks can also be calculated.
, so that the practical secret key rate for the LLO-CVQKD under collective attacks can also be calculated.
3. Simulation and Discussion
The secret key rates for the LLO-CVQKD under phase attack are shown in Figure 2. In the simulations, the parameters are fixed at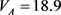 ,
, 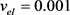 ,
,
![]()
Figure 2. The secret key rates of the LLO-CVQKD system under phase attack. The phase noise variance is 0.0000, 0.0009 and 0.0025 respectively. The solid line, dash line and dotted line are the secret key rates evaluated in theory, while the circles, squares and triangles are the secret key rates estimated by 2000 training signals.
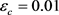 (in shot-noise units),
(in shot-noise units), ![]() and
and![]() , all of which are determined by the practical CVQKD experiment [19]. Besides, it is assumed that the phase noise caused by Eve’s phase attack is normally distributed from
, all of which are determined by the practical CVQKD experiment [19]. Besides, it is assumed that the phase noise caused by Eve’s phase attack is normally distributed from ![]() to
to ![]() degree, where
degree, where ![]() is given by 0, 3 and 5 degrees respectively, so that the corresponding noise variance
is given by 0, 3 and 5 degrees respectively, so that the corresponding noise variance ![]() is 0.0000, 0.0009 and 0.0025 (rad2), and then the phase compensation accuracy
is 0.0000, 0.0009 and 0.0025 (rad2), and then the phase compensation accuracy ![]() is evaluated as 1.0000, 0.9991 and 0.9975 respectively. With the noise model of imperfect phase compensation, the theoretical secret key rates of the LLO-CVQKD system under phase attack can be evaluated.
is evaluated as 1.0000, 0.9991 and 0.9975 respectively. With the noise model of imperfect phase compensation, the theoretical secret key rates of the LLO-CVQKD system under phase attack can be evaluated.
In order to confirm the validity of our security analysis, 2000 Gaussian-modulated coherent states are generated for training, all of which are added with a uniformly-distributed phase noise, and then the actual transmittance ![]() and the actual excess noise
and the actual excess noise ![]() are estimated by them. The practical secret key rates based on the estimated parameters are depicted by the circles, squares and triangles in Figure 2. By the comparison of the theoretical secret key rates and the practical ones, the security analysis of the LLO-CVQKD under phase attack is confirmed to be correct.
are estimated by them. The practical secret key rates based on the estimated parameters are depicted by the circles, squares and triangles in Figure 2. By the comparison of the theoretical secret key rates and the practical ones, the security analysis of the LLO-CVQKD under phase attack is confirmed to be correct.
4. Conclusion
In this paper, we propose a method of phase attack on reference pulses of the LLO-CVQKD with time-multiplexing. The phases of reference pulses can be manipulated by eavesdroppers, and then the secret key rate is reduced because of the increased phase compensation error. The practical security of LLO-CVQKD under phase attack is analyzed based on the noise model of imperfect phase compensation. The simulation results show that the practical security is reduced due to Eve’s phase attack, yet it is still tight when system parameters are estimated by training signals.
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grants No. U1738204, 61571096 and 61775030) and the Foundation of Key Laboratory of Optical Engineering Chinese Academy of Sciences (Grant No. 2017LBC003). The authors thank Dr. Bingjie Xu and Dr. Heng Wang for discussion.